Types Of Cryptography Algorithms Explained Essential Mcq For Cybersecurity Computer Science

Mcq Cryptography Basics Pdf Cryptography Encryption Is a cybersecurity major right for you? Learn about the different types of cybersecurity degrees, plus focus areas and career pathways GCSE Computer Science Principles of computer science learning resources for adults, children, parents and teachers

Cryptography Mcqs Ct 3 Mcq Continuous Learning Assessment 3 Check important MCQ for CBSE Class 12 Computer Science board exam 2021 As we all know term 1 of CBSE Class 12 board exam 2021 will be based on MCQs only so these questions are important for Cryptography is the art of keeping information secret and safe by transforming it into form that unintended recipients cannot understand It makes secure data transmission over the internet possible In July, the National Institute of Standards and Technologies selected four cryptography algorithms as national standards for public key security in order to prepare for an era of quantum computers, A (relatively easy to understand) primer on elliptic curve cryptography Everything you wanted to know about the next generation of public key crypto
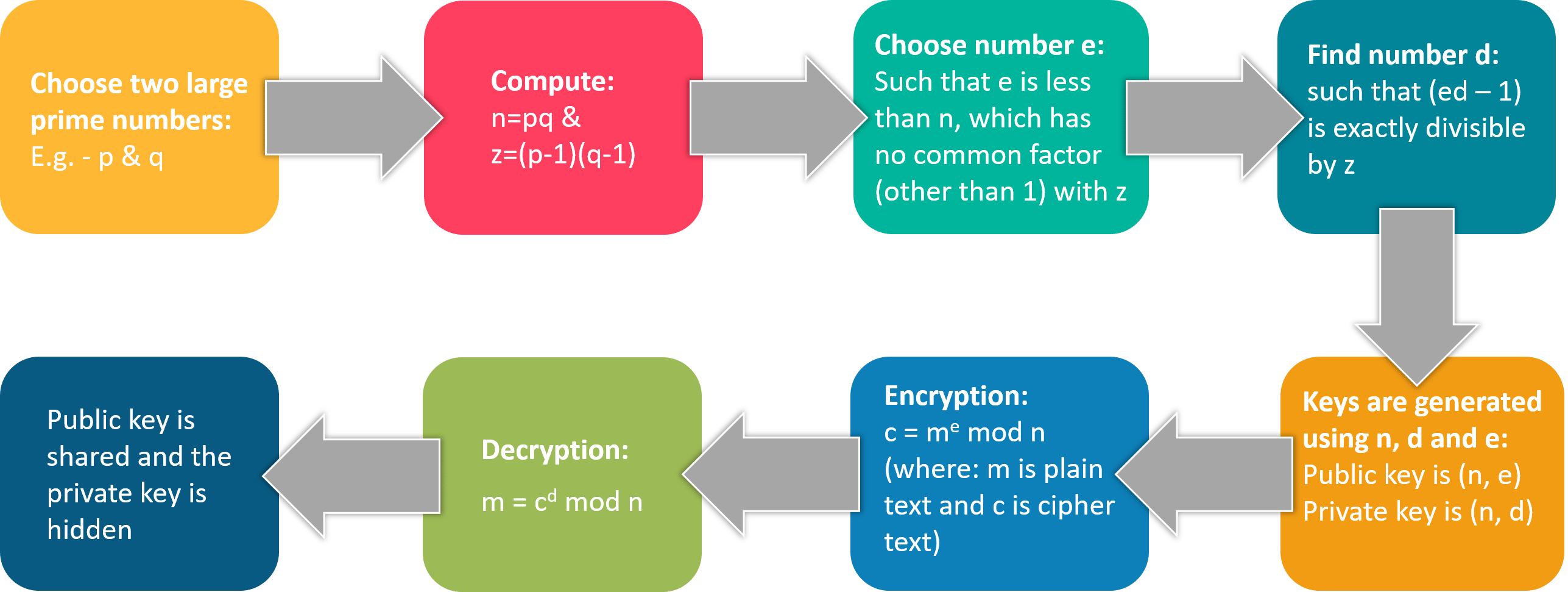
Modern Cryptography And Its Types Information Securit Vrogue Co In July, the National Institute of Standards and Technologies selected four cryptography algorithms as national standards for public key security in order to prepare for an era of quantum computers, A (relatively easy to understand) primer on elliptic curve cryptography Everything you wanted to know about the next generation of public key crypto Cybersecurity researchers and analysts are rightly worried that a new type of computer, based on quantum physics rather than more standard electronics, could break most modern cryptography Actually, other types of cryptography have been developed to get around this vulnerability Banks and e-commerce will start to use them instead of existing methods if and when necessary The quantum computer revolution could break encryption — but more-secure algorithms can safeguard privacy
Comments are closed.