Cryptography Special Issue Cryptographic Algorithms In Blockchain
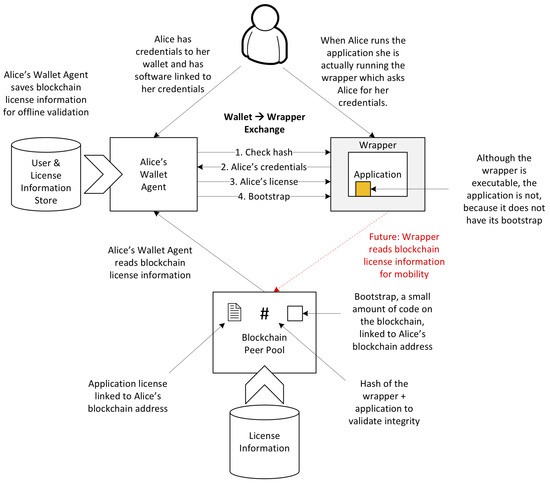
Cryptography Special Issue Cryptographic Algorithms In Blockchain Blockchain is one such example of the development cycle in action Satoshi Nakamoto’s work on Bitcoin was the application of principles first described by David Chaum in the early 1980s Cryptography plays a significant role in the principle of self-sovereign data today, but I believe we will see this concept become more prevalent in Web 30 applications
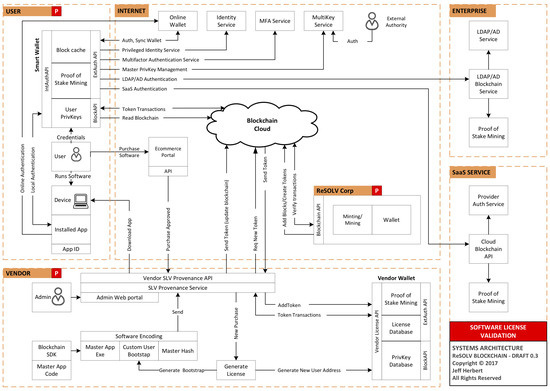
Cryptography Special Issue Cryptographic Algorithms In Blockchain Quantum computing is on the horizon, promising to solve complex problems beyond the capabilities of classical computers But for Bitcoin and other cryptocurrencies, which rely on today’s The fundraising, co-led by Blockchain Capital and 1kx, will be used to "build computing chips, software and cryptographic algorithms," the company said BTC $ 106,17704 Fabric Cryptography say hardware in their sector needs a new approach Fabric Michael Gao, the co-founder of California-based start-up Fabric Cryptography, makes a bold claim“We’re going to Theft of funds across the blockchain 2 51% Attacks Made Easier Quantum computing could accelerate mining capabilities to the point where a bad actor might dominate the network's hash rate
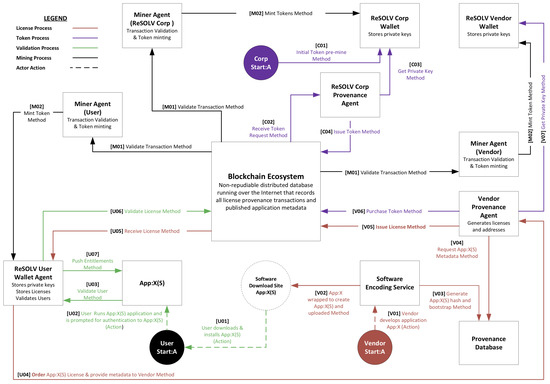
Cryptography Special Issue Cryptographic Algorithms In Blockchain Fabric Cryptography say hardware in their sector needs a new approach Fabric Michael Gao, the co-founder of California-based start-up Fabric Cryptography, makes a bold claim“We’re going to Theft of funds across the blockchain 2 51% Attacks Made Easier Quantum computing could accelerate mining capabilities to the point where a bad actor might dominate the network's hash rate These cryptography algorithms are designed to protect ephemeral data transmitted between edge devices and sensors, not long-term secrets Written by Liam Tung, Contributing Writer Contributing Writer Cryptocurrency generally uses two different cryptographic methods—one dedicated to generating its public-private key pairs and another for the purpose of validating transactions The "Crypto" in 1 Understanding the basics: Foundation in Computer Science: Blockchain is built on concepts like cryptography, distributed computing, and consensus algorithms “However, the challenge of blockchain is not just about the threat that quantum computing represents but scope of how blockchain will migrate to the new version of cryptography”

Blockchain Meets Lightweight Cryptography Pdf These cryptography algorithms are designed to protect ephemeral data transmitted between edge devices and sensors, not long-term secrets Written by Liam Tung, Contributing Writer Contributing Writer Cryptocurrency generally uses two different cryptographic methods—one dedicated to generating its public-private key pairs and another for the purpose of validating transactions The "Crypto" in 1 Understanding the basics: Foundation in Computer Science: Blockchain is built on concepts like cryptography, distributed computing, and consensus algorithms “However, the challenge of blockchain is not just about the threat that quantum computing represents but scope of how blockchain will migrate to the new version of cryptography”
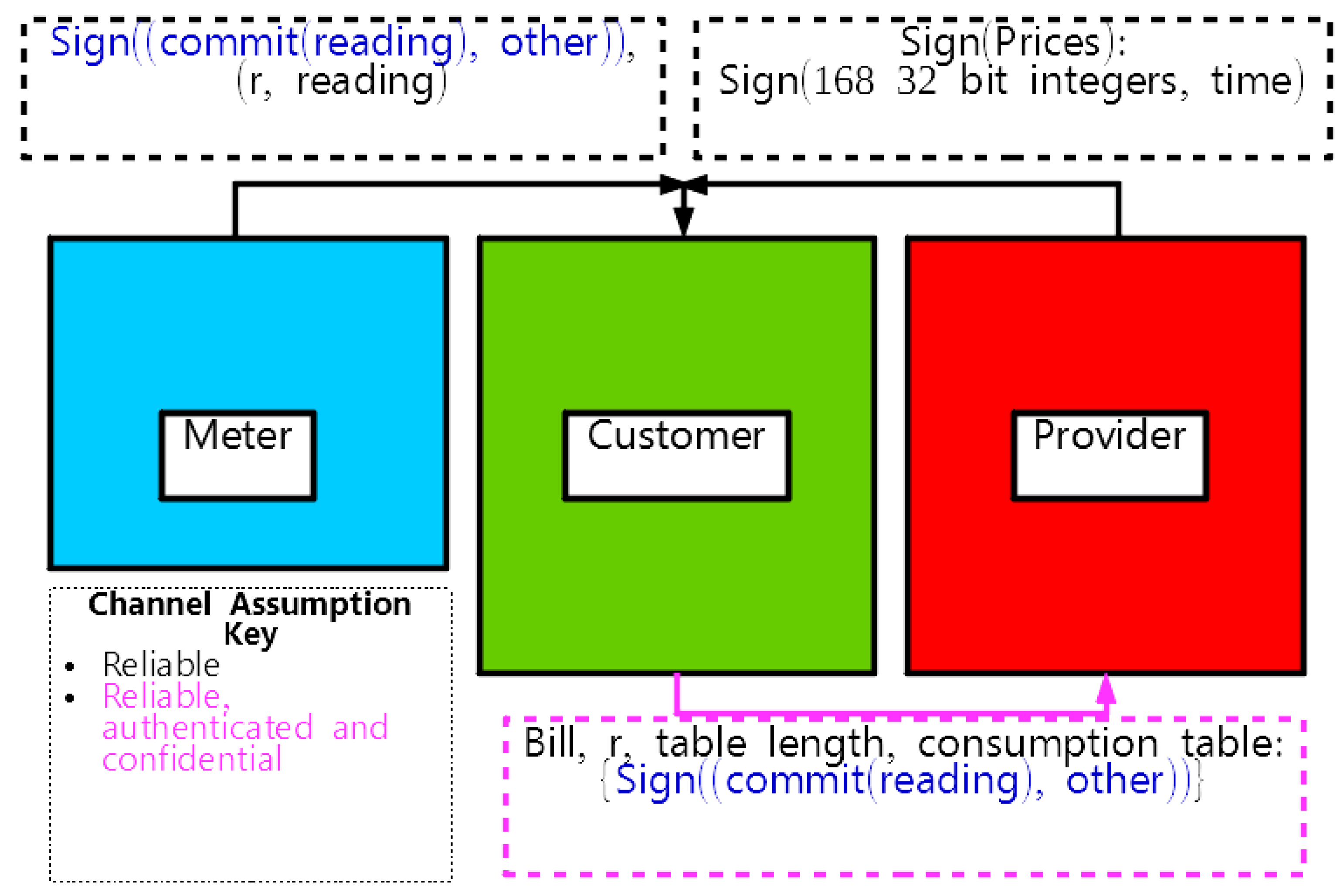
Cryptography Special Issue Cryptographic Protocols 1 Understanding the basics: Foundation in Computer Science: Blockchain is built on concepts like cryptography, distributed computing, and consensus algorithms “However, the challenge of blockchain is not just about the threat that quantum computing represents but scope of how blockchain will migrate to the new version of cryptography”

Cryptography Algorithms A Guide To Algorithms In Blockchain Quantum
Comments are closed.