Windows Exploit Development Remote Stack Buffer Overflow

Introduction To Exploit Development Buffer Overflows Pdf Download In this article we will details how to exploit a buffer overflow in order to achieve remote code execution via shellcode injection. as previously stated in the introduction, today’s memory layout of a running application has become significantly more complex due to the implementation of various security measures. This write up guides you through all the steps of developing a windows exploit, using a program that deliberately has a simple buffer overflow vulnerability.
Github Kaikoh95 Stack Buffer Overflow Exploit This Repository This article is based on exploiting a simple buffer overflow in windows using vulnserver. if you don’t have an idea about buffer overflows, read my previous article about exploiting a linux buffer…. Buffer overflow vulnerability happens when data written to a buffer exceeds its size, which may overwrite important data or execute malicious code. attackers can exploit these vulnerabilities to gain unauthorized access, execute malicious code, or steal sensitive data. Stack based buffer overflow exploits are likely the shiniest and most common form of exploit for remotely taking over the code execution of a process. Today, i will show you how to use windgb and immunity debugger to make a buffer overflow. i’ll pay more attention to windgb. windbg is a debugger for the microsoft windows operating system that can be used for many different things. debugging is the process of finding and fixing bugs in a computer system.

Windows Stack Buffer Overflow In A Real Life App Exploit Development Stack based buffer overflow exploits are likely the shiniest and most common form of exploit for remotely taking over the code execution of a process. Today, i will show you how to use windgb and immunity debugger to make a buffer overflow. i’ll pay more attention to windgb. windbg is a debugger for the microsoft windows operating system that can be used for many different things. debugging is the process of finding and fixing bugs in a computer system. Unfortunately, yes, buffer overflow and similar attacks are still possible. microsoft has found approximately 70% of security vulnerabilities are various forms of memory unsafety, including buffer overflows. In this lab, we're going to exploit the vulnerable program and make it execute our shellcode by following the below process: overflow the vulnerable program's stack with a buffer larger than it expected. the buffer will be crafted in such a way, that once in the vulnerable program's memory, it will have:. This module is your first step into windows binary exploitation, and it will teach you how to exploit local and remote buffer overflow vulnerabilities on windows machines. In order to effectively and efficiently complete any simple x86 stack based windows buffer overflow (such as the ones within the oscp exam), we have to follow a step by step approach. the steps include: exploitation. these steps will be elaborated below.
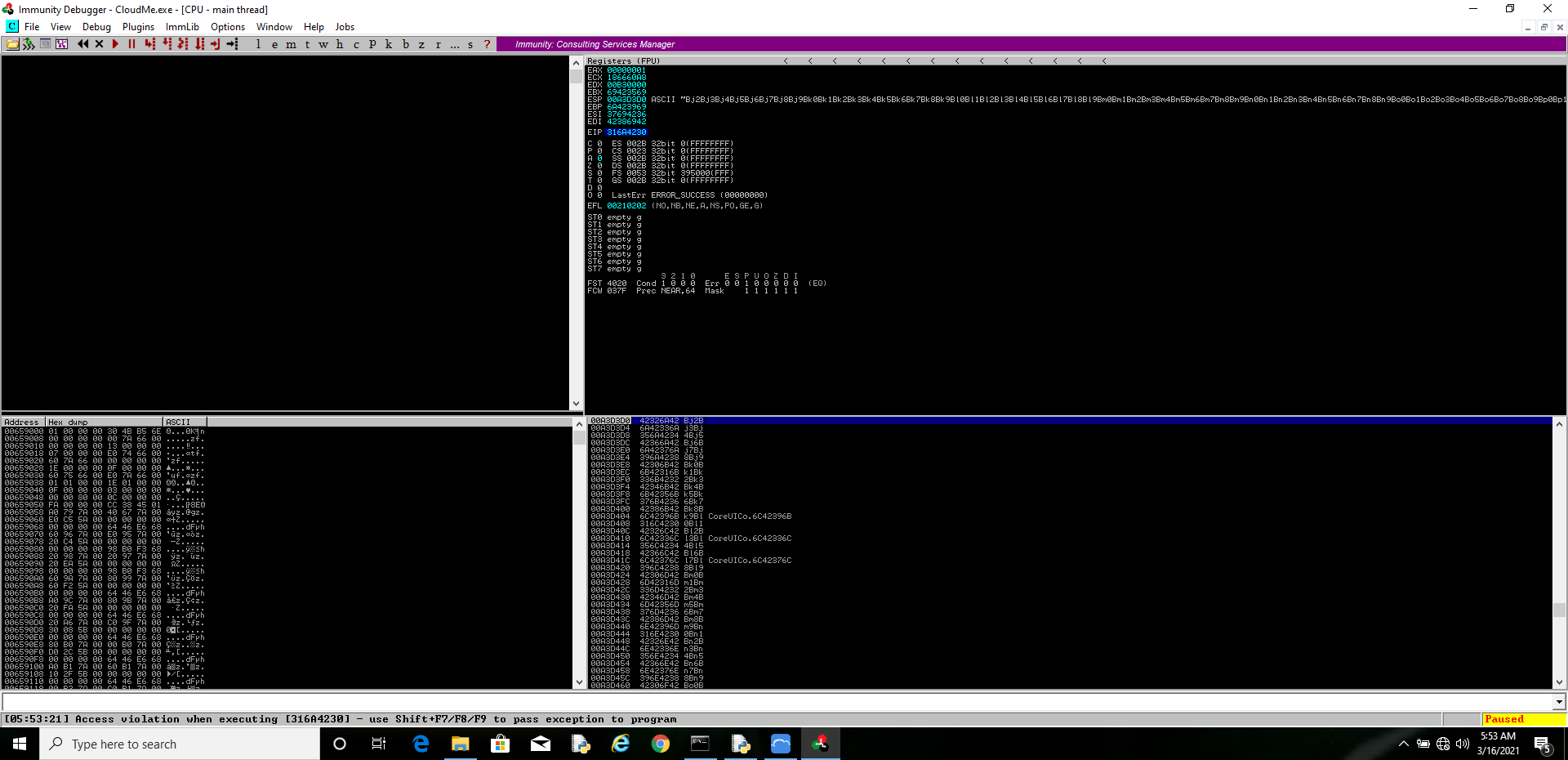
Windows Stack Buffer Overflow In A Real Life App Exploit Development Unfortunately, yes, buffer overflow and similar attacks are still possible. microsoft has found approximately 70% of security vulnerabilities are various forms of memory unsafety, including buffer overflows. In this lab, we're going to exploit the vulnerable program and make it execute our shellcode by following the below process: overflow the vulnerable program's stack with a buffer larger than it expected. the buffer will be crafted in such a way, that once in the vulnerable program's memory, it will have:. This module is your first step into windows binary exploitation, and it will teach you how to exploit local and remote buffer overflow vulnerabilities on windows machines. In order to effectively and efficiently complete any simple x86 stack based windows buffer overflow (such as the ones within the oscp exam), we have to follow a step by step approach. the steps include: exploitation. these steps will be elaborated below.

Windows Stack Buffer Overflow In A Real Life App Exploit Development This module is your first step into windows binary exploitation, and it will teach you how to exploit local and remote buffer overflow vulnerabilities on windows machines. In order to effectively and efficiently complete any simple x86 stack based windows buffer overflow (such as the ones within the oscp exam), we have to follow a step by step approach. the steps include: exploitation. these steps will be elaborated below.

Windows Stack Buffer Overflow In A Real Life App Exploit Development
Comments are closed.