What Is Secure Hash Algorithm 1 Securityfirstcorp Com

Secure Hash Sha1 Algorithm Download Scientific Diagram What is secure hash algorithm 1? secure hash algorithm 1 (sha 1) is a cryptographic hash function that has played a significant role in the field of cybersec. In cryptography, sha 1 (secure hash algorithm 1) is a hash function which takes an input and produces a 160 bit (20 byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits. it was designed by the united states national security agency, and is a u.s. federal information processing standard. [3].

Secure Hash Sha1 Algorithm Download Scientific Diagram Sha 1 or secure hash algorithm 1 is a cryptographic algorithm that takes an input and produces a 160 bit (20 byte) hash value. this hash value is known as a message digest. Sha 1 (secure hash algorithm 1) is a cryptographic hash function designed to create a unique, fixed size hash value from data of any size. it is commonly used in cybersecurity to verify data integrity, ensuring that data has not been altered in transit. Sha 1 is a cryptographic hash function that generates a 160 bit hash value (also known as a message digest) from any input message up to 2 64 1 bits. the national security agency (nsa) devised sha 1, which was published by the national institute of standards and technology (nist) in 1995 as part of the secure hash standard (shs). What exactly is sha 1? sha 1, which stands for secure hash algorithm 1, is a cryptographic hash function. okay, let's break that down. imagine you have a document, a picture, or any piece of digital data. sha 1 takes this data and creates a fixed size "fingerprint" of it. this fingerprint is called a "hash.".

Secure Hash Algorithm Sha 1 is a cryptographic hash function that generates a 160 bit hash value (also known as a message digest) from any input message up to 2 64 1 bits. the national security agency (nsa) devised sha 1, which was published by the national institute of standards and technology (nist) in 1995 as part of the secure hash standard (shs). What exactly is sha 1? sha 1, which stands for secure hash algorithm 1, is a cryptographic hash function. okay, let's break that down. imagine you have a document, a picture, or any piece of digital data. sha 1 takes this data and creates a fixed size "fingerprint" of it. this fingerprint is called a "hash.". What is sha? secure hash algorithms (sha) comprises bit wise operations, modular additions, and compression functions. bit wise operations are operations performed on 2 bits. Sha1 (secure hash algorithm 1) is a widely used cryptographic hash function designed by the nsa and published as a standard in 1995. it generates a condensed 160 bit hash value representation of data to help ensure integrity and authenticity. Sha 1 (secure hash algorithm 1) is a cryptographic hash function that is used to encrypt and verify data in cybersecurity. it generates a unique fixed length output that is used to ensure the integrity of data and detect any changes made to it. The secure hash algorithm 1 (sha 1) is a cryptographic hash function that is used to generate a unique fixed length digital fingerprint of a message or data. it was developed by the united states national security agency (nsa) and published by the national institute of standards and technology (nist) in 1995.
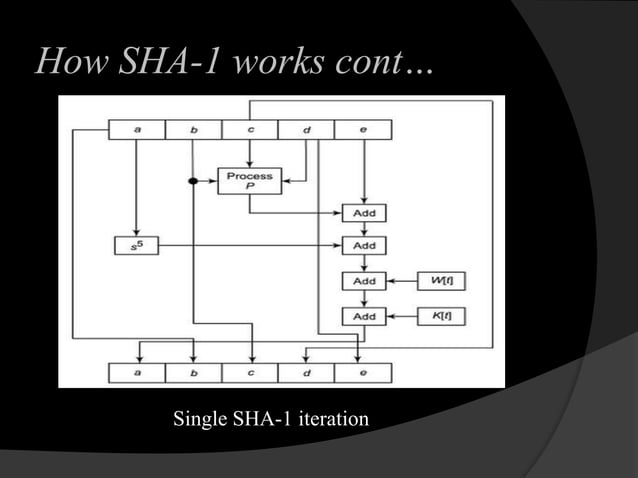
Secure Hash Algorithm What is sha? secure hash algorithms (sha) comprises bit wise operations, modular additions, and compression functions. bit wise operations are operations performed on 2 bits. Sha1 (secure hash algorithm 1) is a widely used cryptographic hash function designed by the nsa and published as a standard in 1995. it generates a condensed 160 bit hash value representation of data to help ensure integrity and authenticity. Sha 1 (secure hash algorithm 1) is a cryptographic hash function that is used to encrypt and verify data in cybersecurity. it generates a unique fixed length output that is used to ensure the integrity of data and detect any changes made to it. The secure hash algorithm 1 (sha 1) is a cryptographic hash function that is used to generate a unique fixed length digital fingerprint of a message or data. it was developed by the united states national security agency (nsa) and published by the national institute of standards and technology (nist) in 1995.

Secure Hash Algorithm 1 Deemed Unsafe Techcentral Ie Sha 1 (secure hash algorithm 1) is a cryptographic hash function that is used to encrypt and verify data in cybersecurity. it generates a unique fixed length output that is used to ensure the integrity of data and detect any changes made to it. The secure hash algorithm 1 (sha 1) is a cryptographic hash function that is used to generate a unique fixed length digital fingerprint of a message or data. it was developed by the united states national security agency (nsa) and published by the national institute of standards and technology (nist) in 1995.

Secure Hash Algorithm
Comments are closed.