What Is Public Key Encryption Analytics Steps

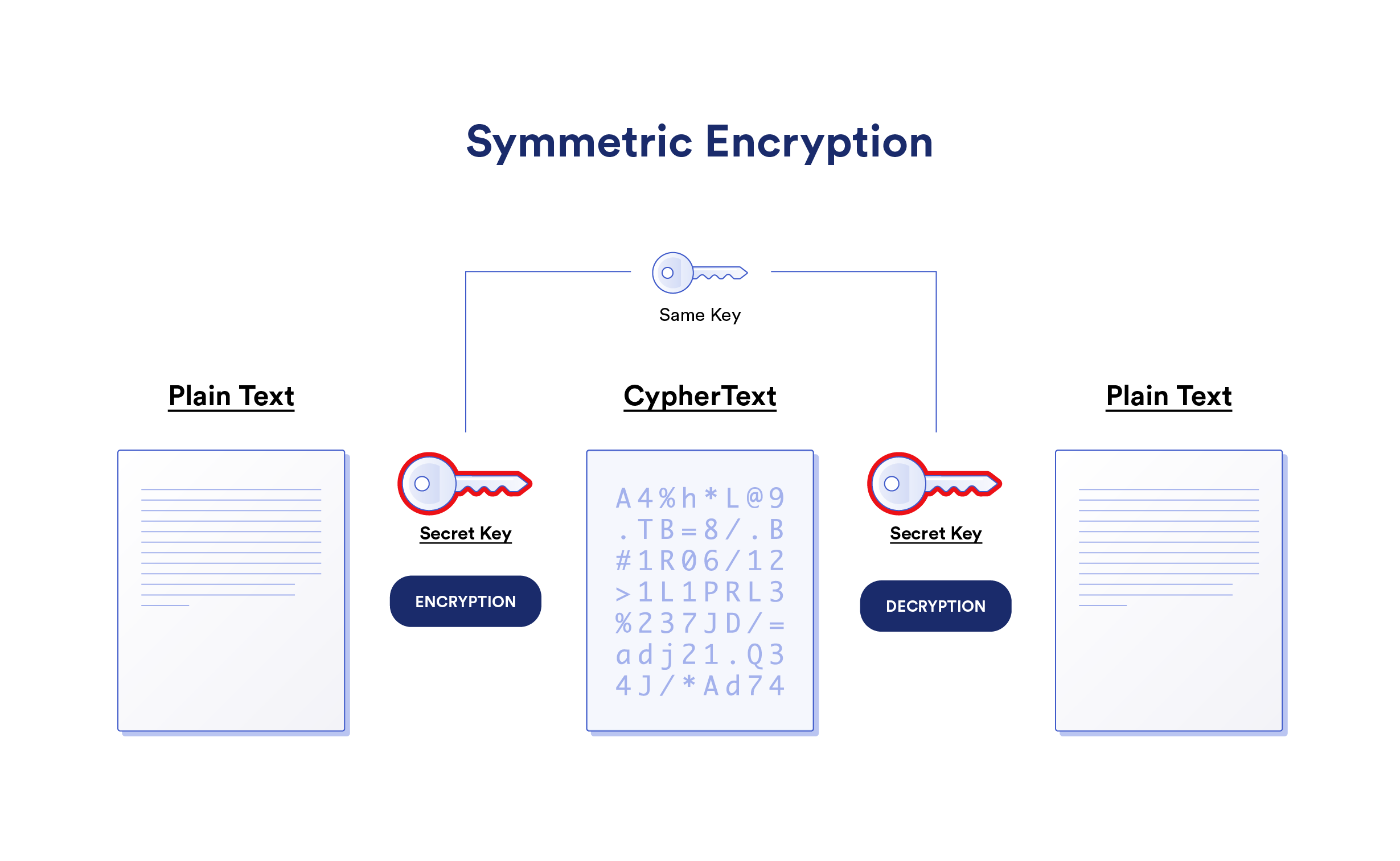
Public Key Encryption Pdf Public Key Cryptography Cryptography Public key encryption is a technique for encrypting or signing data using two separate keys while having the public key accessible to everyone. learn what it is and its applications. Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing.

Public Key Encryption Pdf Cryptography Key Cryptography However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc. Public key infrastructure (pki) is a comprehensive governing framework that helps establish secure end to end digital communication. pki outlines a set of mechanisms and protocols to verify the identities of users, devices, applications, programs, and other entities involved in digital communications. last updated date : 18 apr 2025. 01. Let’s take a closer look at pki security fundamentals to understand how it’s used to secure data on the internet. asymmetric cryptography relies on a public private keypair: the public key encrypts data, and the private key decrypts it. for you skimmers, here’s a quick overview of pki basics in video form:. Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures.

What Is Public Key Encryption Analytics Steps Let’s take a closer look at pki security fundamentals to understand how it’s used to secure data on the internet. asymmetric cryptography relies on a public private keypair: the public key encrypts data, and the private key decrypts it. for you skimmers, here’s a quick overview of pki basics in video form:. Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures. Public key encryption uses that key pair for encryption and decryption. the public key is made public and is distributed widely and freely. the private key is never distributed and must be kept secret. Public key encryption converts plain text messages into ciphertext that can only be decrypted by the intended recipient’s private key. this ensures confidentiality and privacy. digital signatures enable authentication and integrity while preventing repudiation. Key generation: the receiver generates a public private key pair. this is typically achieved using complex mathematical algorithms. public key distribution: the receiver makes their public key available to anyone who wishes to send them encrypted messages. Receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver.
What Is Public Key Encryption Analytics Steps Vrogue Co Public key encryption uses that key pair for encryption and decryption. the public key is made public and is distributed widely and freely. the private key is never distributed and must be kept secret. Public key encryption converts plain text messages into ciphertext that can only be decrypted by the intended recipient’s private key. this ensures confidentiality and privacy. digital signatures enable authentication and integrity while preventing repudiation. Key generation: the receiver generates a public private key pair. this is typically achieved using complex mathematical algorithms. public key distribution: the receiver makes their public key available to anyone who wishes to send them encrypted messages. Receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver.
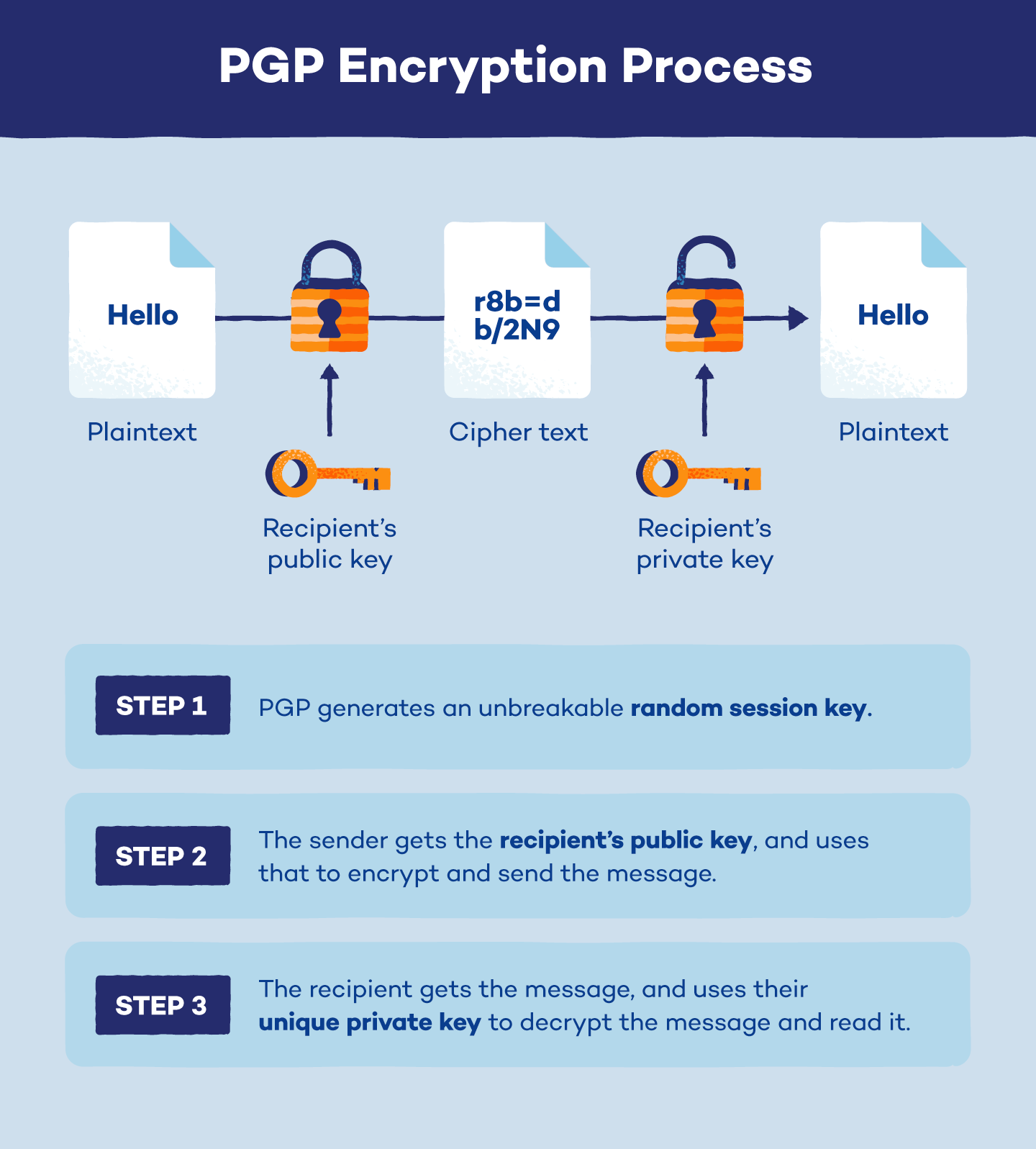
What Is Public Key Encryption Analytics Steps Vrogue Co Key generation: the receiver generates a public private key pair. this is typically achieved using complex mathematical algorithms. public key distribution: the receiver makes their public key available to anyone who wishes to send them encrypted messages. Receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver.

What Is Public Key Encryption Analytics Steps Vrogue Co
Comments are closed.