What Is Phishing Phishing Attacks Explained In 2 Minutes

What Is Phishing Phishing Attacks Explained In 2 Minutes Such attacks require a great deal of time and energy from IT and security teams, which, on average, spend approximately 28 minutes dealing with a single phishing email at a cost of about $31 per According to the 2024 Phishing Report by Zscaler ThreatLabz, there were 582 percent more phishing attacks globally in 2023 than in 2022, showing that phishing isn’t just alive and well—it’s

Phishing Attacks How To Prevent Them Sucuri Oct 27—For Jody Hagemann, the senior director of sales engineering for the Northeast Division of Comcast Business, issues of cybersecurity and, specifically, of phishing are of the utmost concern In Q2 2024 alone, there was a 522% increase in phishing attacks that successfully bypassed SEG detection You may like AI is making phishing emails far more convincing with fewer typos and better The number of incidents has been growing as per the following chart: 2024: 14264 - 2023: 4968 - 2022: 4169 - 2021: 3948 - 2020: 2798; and 2019: 2217 According to the website wwwphishing Vishing attacks rose steeply by 442% between H1 2024 and H2 2024 as threat actors employed helpdesk social engineering and callback phishing methods to target victims How AI is enhancing vishing
.png#keepProtocol)
Phishing Attacks The Anatomy Of A Threat The number of incidents has been growing as per the following chart: 2024: 14264 - 2023: 4968 - 2022: 4169 - 2021: 3948 - 2020: 2798; and 2019: 2217 According to the website wwwphishing Vishing attacks rose steeply by 442% between H1 2024 and H2 2024 as threat actors employed helpdesk social engineering and callback phishing methods to target victims How AI is enhancing vishing In terms of email attacks, phishing remained the top attack method at 333% This makes it by far the most common attack vector, next to malicious URLs But not all phishing is the same Top 10 most-phished brands Among the top 10 most-phished brands in the fourth quarter of 2024, Microsoft remained in the top spot, appearing in 32% of all attacks seen by Check Point There are many known phishing attacks that target users of Apple devices to gain access to their Apple ID However, a new “elaborate” attack uses a bug in the Apple ID password reset feature Email security and threat detection company Vade has found that phishing emails in the third quarter this year increased by more than 31% quarter on quarter, with the number of emails containing

Phishing Attack Png How To Recognize Common Phishing Attacks Omega Vrogue In terms of email attacks, phishing remained the top attack method at 333% This makes it by far the most common attack vector, next to malicious URLs But not all phishing is the same Top 10 most-phished brands Among the top 10 most-phished brands in the fourth quarter of 2024, Microsoft remained in the top spot, appearing in 32% of all attacks seen by Check Point There are many known phishing attacks that target users of Apple devices to gain access to their Apple ID However, a new “elaborate” attack uses a bug in the Apple ID password reset feature Email security and threat detection company Vade has found that phishing emails in the third quarter this year increased by more than 31% quarter on quarter, with the number of emails containing The second, more systematic way to root out a number of phishing attacks is to educate the masses “You’ve got to do regular human intervention, education, testing…” said Hagemann
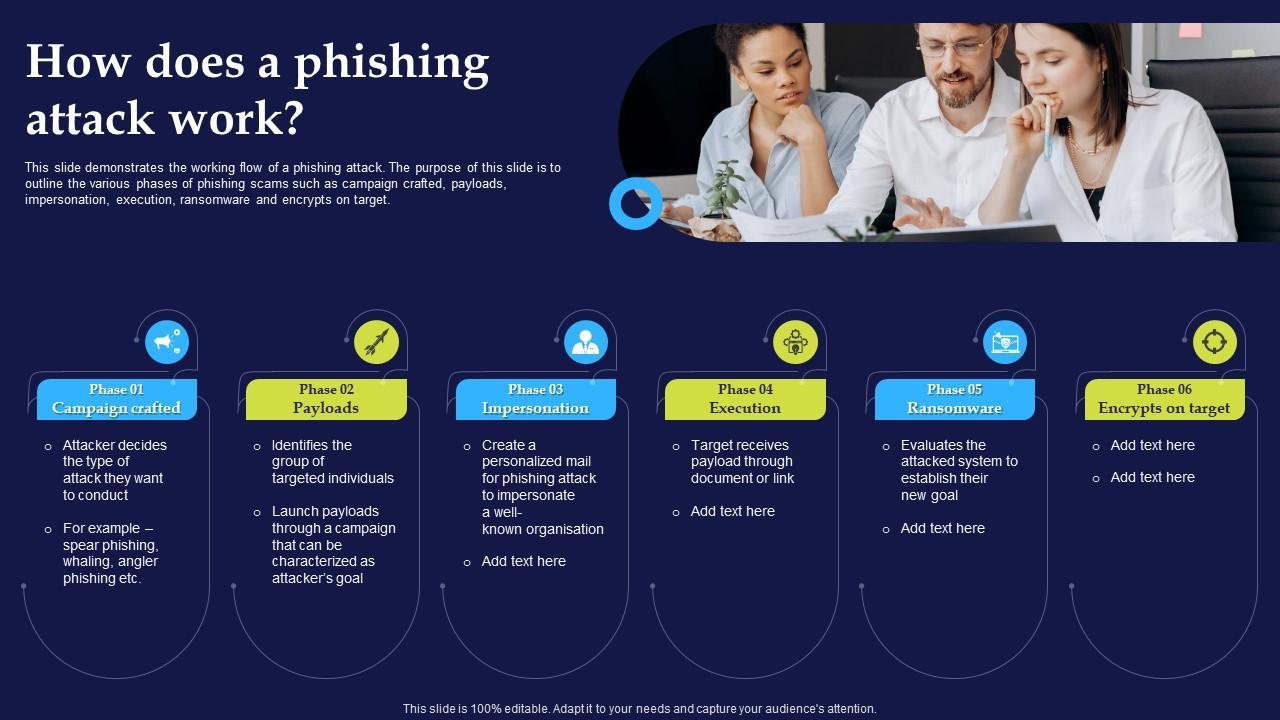
How Does A Phishing Attack Work Phishing Attacks And Strategies Ppt Slide There are many known phishing attacks that target users of Apple devices to gain access to their Apple ID However, a new “elaborate” attack uses a bug in the Apple ID password reset feature Email security and threat detection company Vade has found that phishing emails in the third quarter this year increased by more than 31% quarter on quarter, with the number of emails containing The second, more systematic way to root out a number of phishing attacks is to educate the masses “You’ve got to do regular human intervention, education, testing…” said Hagemann
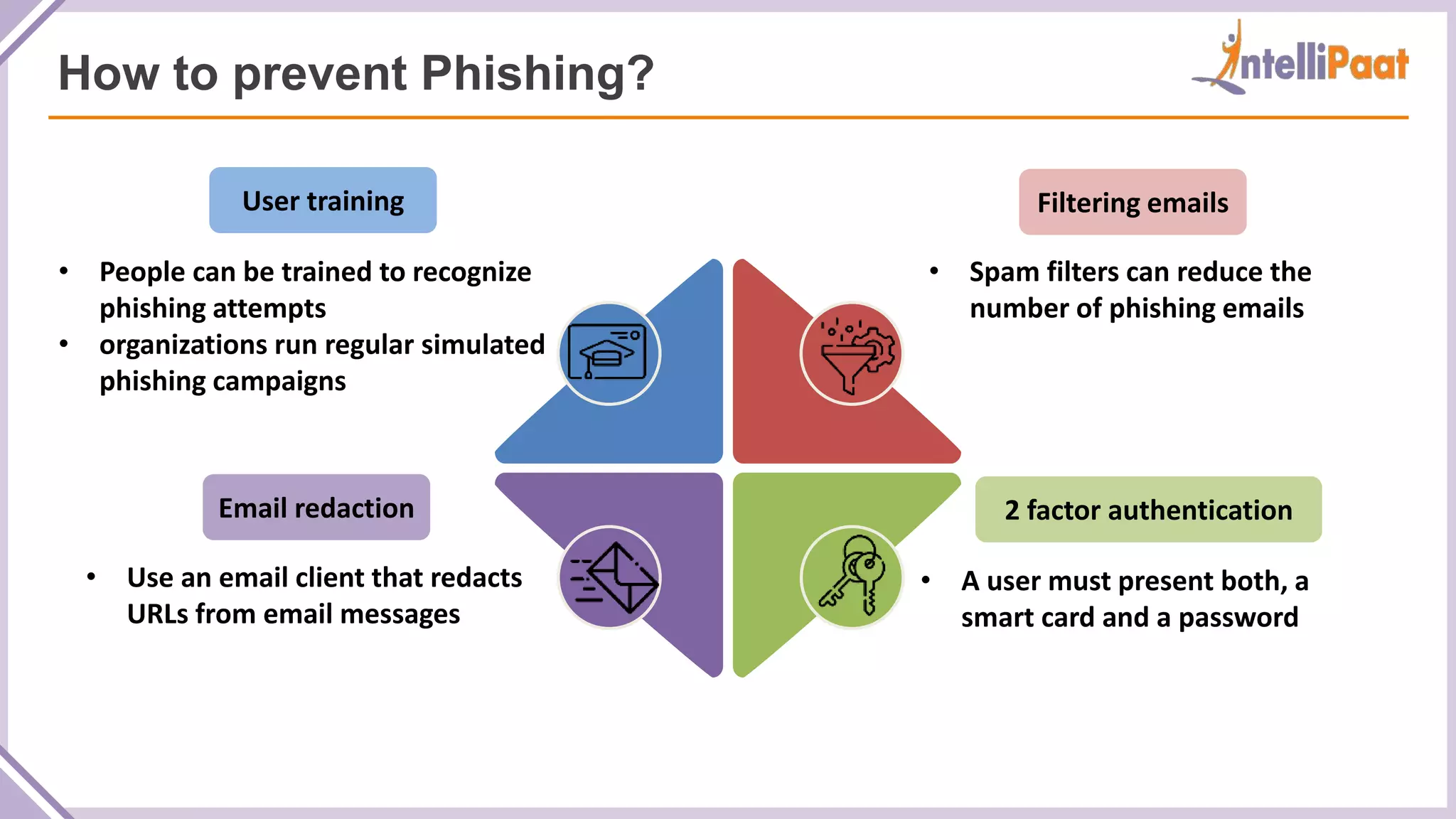
Phishing For Beginners Phishing Tutorial What Is Phishing The second, more systematic way to root out a number of phishing attacks is to educate the masses “You’ve got to do regular human intervention, education, testing…” said Hagemann
Comments are closed.