What Is Asymmetric Encryption How Does It Work Infosec Insights And
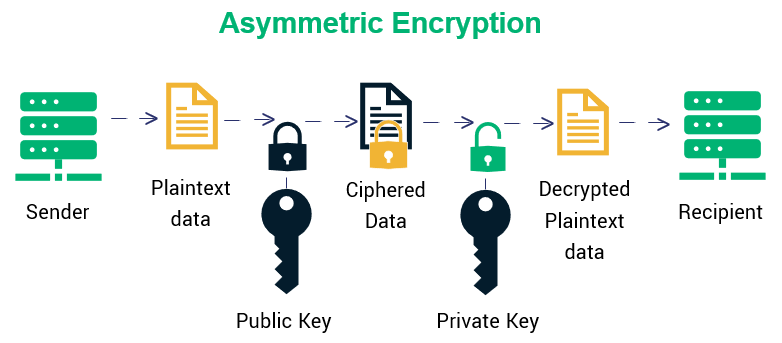
Types Of Encryption What To Know About Symmetric Vs Asymmetric In this article, we’ll cover what asymmetric key encryption is and answer your question “how does asymmetric encryption work?” in layman’s terms. later on, we will also take a look at the strengths and weaknesses of this type of encryption. In this post, we will be focusing on and discussing asymmetric encryption in detail. asymmetric encryption is when the sender and the recipient of the data use different keys to encrypt and decrypt the data.
Encryption Insights Sslinsights What is asymmetric encryption? asymmetric encryption is an encryption method that uses two different keys—a public key and a private key—to encrypt and decrypt data. it’s generally regarded as more secure, though less efficient, than symmetric encryption. Asymmetric encryption, also known as public key cryptography, is a type of encryption that uses a pair of keys to encrypt and decrypt data. the pair of keys includes a public key, which can be shared with anyone, and a private key, which is kept secret by the owner. Asymmetric encryption, also known as public key cryptography, is an essential concept in modern information security. this beginner’s guide will introduce asymmetric encryption and how it works. How does asymmetric encryption work? asymmetric encryption uses a method known as public key or asymmetric key encryption to create a public key private key pairing. the public key only works for encryption, and the private key only works for decryption.

Asymmetric Encryption Network Encyclopedia Asymmetric encryption, also known as public key cryptography, is an essential concept in modern information security. this beginner’s guide will introduce asymmetric encryption and how it works. How does asymmetric encryption work? asymmetric encryption uses a method known as public key or asymmetric key encryption to create a public key private key pairing. the public key only works for encryption, and the private key only works for decryption. From online banking to encrypted messaging, asymmetric encryption plays a crucial role in safeguarding data. but what exactly is asymmetric encryption, and how does it work? in this blog, we explore its principles, key components, applications, pros, cons, and its role in modern cybersecurity. Asymmetric encryption is an encryption technique used to encrypt and decrypt the data that is being transferred between two parties in public. the process of asymmetric encryption involves using two keys, one for encryption and the other one for decryption. Asymmetric encryption uses a pair of keys: one for encryption and another for decryption, ensuring secure data transmission. key components include a public key for encryption and a private key for decryption, generated using complex mathematical algorithms. Asymmetric cryptography differs from symmetric cryptography in that it uses two encryption keys: a public key and a private key. these keys are related by a mathematically “hard” problem, making it possible to derive a public key from a private key but not vice versa.
Comments are closed.