What Is A Cryptographic Hashing Function Example Purpose

Cryptographic Hash Function Wikipedia Pdf Cryptography Password Cryptographic hash functions are intended to be fast, deterministic, and one way, meaning that even a minor change in input yields a very different hash. these functions are important for securing information digitally by allowing data verification and authentication. Most cryptographic hash functions are designed to take a string of any length as input and produce a fixed length hash value. a cryptographic hash function must be able to withstand all known types of cryptanalytic attack.

Cryptographic Hash Function And Its Properties Pdf Cryptography They're a fundamental part of cryptography, which is like a secret language for computers. these functions take any data—whether it's a sentence, a file, or a piece of a code—and turn it into a fixed size string of characters. this string is called a 'hash'. This type of function has tolerance to changes and can be used to tell how two inputs differ based on their hash codes. applications include malware classification and digital forensics. Hash functions are used for cryptocurrency, password security, and message security. hash functions are data structures used in computing systems to check the integrity of messages and. Hash functions play a crucial role in various security applications, including password storage (hash values instead of passwords), digital signatures, and data integrity checks. hash values, or message digests, are values that a hash function returns. the hash function is shown in the image below −.

M 3 Cryptographic Hash Functions Pdf Public Key Cryptography Hash functions are used for cryptocurrency, password security, and message security. hash functions are data structures used in computing systems to check the integrity of messages and. Hash functions play a crucial role in various security applications, including password storage (hash values instead of passwords), digital signatures, and data integrity checks. hash values, or message digests, are values that a hash function returns. the hash function is shown in the image below −. One common example of a hash function in cryptography is its use in password verification. in this context, the cryptographic hash function transforms the user's password into a hash value, which is then stored instead of the plaintext password. This article explains what cryptographic hash functions are, their various applications, how they work, their strengths and weaknesses, and provides some examples of popular hash functions. What is a hash? understanding the role of hash functions in cryptography a hash is a mathematical function that transforms input data of any size into a fixed length string of characters. this output is called a hash value or hash code. hash functions generate a unique fingerprint for data, ensuring that even the smallest change in input completely alters the resulting hash. Cryptographic hash functions: definition and examples. in the realm of computer science and cybersecurity, cryptographic hash functions play a critical role. they underpin many security protocols and systems, including digital signatures, data integrity verification, and cryptocurrency transactions.
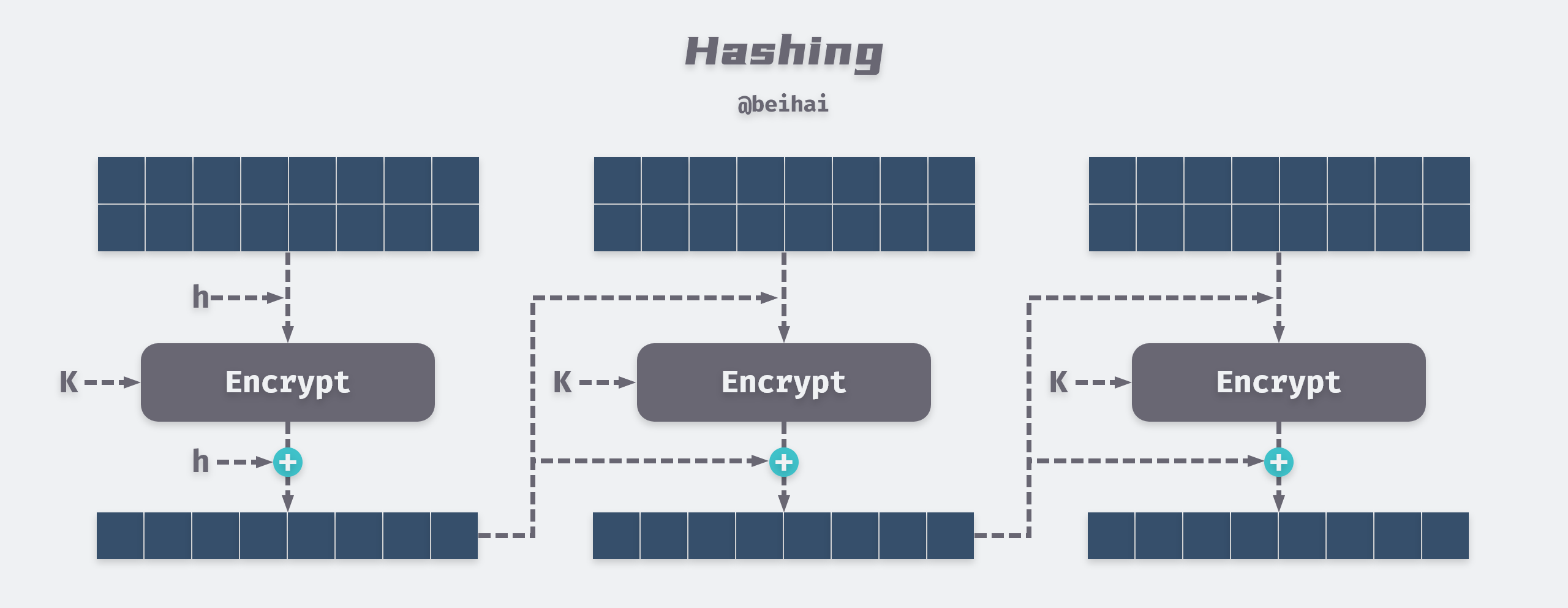
Implementation Principle Of Cryptographic Hash Algorithm Sobyte One common example of a hash function in cryptography is its use in password verification. in this context, the cryptographic hash function transforms the user's password into a hash value, which is then stored instead of the plaintext password. This article explains what cryptographic hash functions are, their various applications, how they work, their strengths and weaknesses, and provides some examples of popular hash functions. What is a hash? understanding the role of hash functions in cryptography a hash is a mathematical function that transforms input data of any size into a fixed length string of characters. this output is called a hash value or hash code. hash functions generate a unique fingerprint for data, ensuring that even the smallest change in input completely alters the resulting hash. Cryptographic hash functions: definition and examples. in the realm of computer science and cybersecurity, cryptographic hash functions play a critical role. they underpin many security protocols and systems, including digital signatures, data integrity verification, and cryptocurrency transactions.
Comments are closed.