What Are Common Symmetric Encryption Algorithms Cryptobasics360 Com

Symmetric Encryption Algorithms Dapcash In this informative video, we will discuss the essentials of symmetric encryption algorithms and their signi. Some popular symmetric encryption algorithms are: aes, chacha20, cast, twofish, idea, serpent, rc5, rc6, camellia and aria. all these algorithms are considered secure (when configured and used correctly).

Which Of The Following Best Explains How Symmetric Encryption Symmetric key algorithms require both the sender and the recipient of a message to have the same secret key. all early cryptographic systems required either the sender or the recipient to somehow receive a copy of that secret key over a physically secure channel. Symmetrical key cryptography also known as conventional or single key encryption was the primary method of encryption before the introduction of public key cryptography in the 1970s. in symmetric key algorithms, the same keys are used for data encryption and decryption. Symmetric algorithms are the cryptographic functions that are central to symmetric key encryption. they’re a set of instructions or steps that computers follow to perform specific tasks relating to encrypting and decrypting data. Symmetric encryption algorithms not only ensure confidentiality but also data integrity, a critical factor in financial transactions. by generating message authentication codes (macs), symmetric keys can help confirm that no one altered the data during transmission.

Ppt Symmetric Encryption Algorithms Pdfslide Net Symmetric algorithms are the cryptographic functions that are central to symmetric key encryption. they’re a set of instructions or steps that computers follow to perform specific tasks relating to encrypting and decrypting data. Symmetric encryption algorithms not only ensure confidentiality but also data integrity, a critical factor in financial transactions. by generating message authentication codes (macs), symmetric keys can help confirm that no one altered the data during transmission. When two parties use symmetric encryption, a symmetric key is generated using a symmetric encryption algorithm such as advanced encryption standard (aes). this key is then shared between the parties communicating. This module explores asymmetric key cryptography, explaining how public and private keys work, the process of key pair generation, popular algorithms like rsa and ecc, and their applications in secure communication. A symmetric encryption algorithm is a type of encryption algorithm that uses a single secret key for both encryption and decryption processes. it is known for its high security and fast processing speed, making it suitable for encrypting large amounts of data. Common symmetric encryption algorithms include advanced encryption standard (aes), data encryption standard (des), triple des (3des), and blowfish. one of the main challenges with symmetric encryption is the secure distribution and management of the secret key.
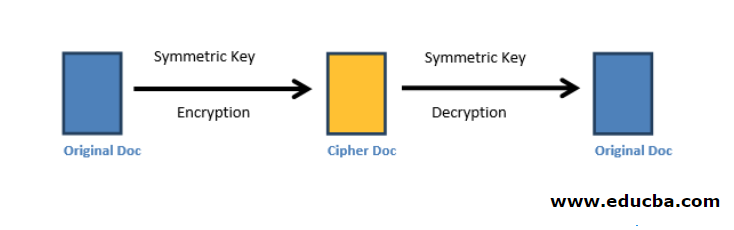
Symmetric Algorithms Types Of Symmetric Algorithms When two parties use symmetric encryption, a symmetric key is generated using a symmetric encryption algorithm such as advanced encryption standard (aes). this key is then shared between the parties communicating. This module explores asymmetric key cryptography, explaining how public and private keys work, the process of key pair generation, popular algorithms like rsa and ecc, and their applications in secure communication. A symmetric encryption algorithm is a type of encryption algorithm that uses a single secret key for both encryption and decryption processes. it is known for its high security and fast processing speed, making it suitable for encrypting large amounts of data. Common symmetric encryption algorithms include advanced encryption standard (aes), data encryption standard (des), triple des (3des), and blowfish. one of the main challenges with symmetric encryption is the secure distribution and management of the secret key.
Comments are closed.