Week 8 9 Cryptography Symmetric Encryption 1 Part 1 2 Pdf

Week 8 9 Cryptography Symmetric Encryption 1 Part 1 2 Pdf Week 8 9 cryptography symmetric encryption 1 part 1 2 free download as powerpoint presentation (.ppt .pptx), pdf file (.pdf), text file (.txt) or view presentation slides online. Question 3 –types of symmetric ciphers symmetric ciphers are often used to provide confidentiality for messages. a) why is the term ‘symmetric’ used for these ciphers? what aspect of the operation has symmetry? b) there are two main categories of symmetric ciphers: stream ciphers and block ciphers.

Symmetric Encryption Pdf Cryptography Key Cryptography From shannon’s results, it is known that no perfect symmetric key encryption scheme exists, unless the length of the key is at least the sum of the lengths of all transmitted messages. practical schemes try to imitate vernam’s perfect encryption scheme, by expanding a long term key to a pseudorandom sequence, which is used to encrypt the message. An example of symmetric key encryption is the one time pad encryption scheme, invented by vernam in 1917. in a one time pad, the key is a uniformly random sequence of bits the same length as the message to be encrypted. 18 330 cryptography notes: symmetric encryption note: this is provided as a resource and is not meant to include all material from lectures or recitations. the proofs shown, however, are good models for your homework and exams. Symmetric cryptography. chapter 10 is concerned with how to formalize security of ryptographic primitives. it first discusses the most common adversary models and what it means for an attack to be succe.

Symmetriccryptography Part3 Tagged Pdf 18 330 cryptography notes: symmetric encryption note: this is provided as a resource and is not meant to include all material from lectures or recitations. the proofs shown, however, are good models for your homework and exams. Symmetric cryptography. chapter 10 is concerned with how to formalize security of ryptographic primitives. it first discusses the most common adversary models and what it means for an attack to be succe. Study with quizlet and memorize flashcards containing terms like cryptography, key, symmetric algorithms and more. This is part of the 4 course specialization introduction to applied cryptography by the university of colorado. this is the third course in this specialization. Let's take an example to understand the caesar cipher, suppose we are shifting with 1, then a will be replaced by b, b will be replaced by c, c will be replaced by d, d will be replaced by c, and this process continues until the entire plain text is finished. caesar cipher is a weak method of cryptography. The document discusses symmetric encryption and message confidentiality. it covers symmetric encryption techniques like the data encryption standard (des) and advanced encryption standard (aes).

Week 2 Symmetric Encryption Flashcards Quizlet Study with quizlet and memorize flashcards containing terms like cryptography, key, symmetric algorithms and more. This is part of the 4 course specialization introduction to applied cryptography by the university of colorado. this is the third course in this specialization. Let's take an example to understand the caesar cipher, suppose we are shifting with 1, then a will be replaced by b, b will be replaced by c, c will be replaced by d, d will be replaced by c, and this process continues until the entire plain text is finished. caesar cipher is a weak method of cryptography. The document discusses symmetric encryption and message confidentiality. it covers symmetric encryption techniques like the data encryption standard (des) and advanced encryption standard (aes).

Sec220 L2part1 Symmetric Encryption Docx Sec625 Lab 2 Part 1 Lab 2 Let's take an example to understand the caesar cipher, suppose we are shifting with 1, then a will be replaced by b, b will be replaced by c, c will be replaced by d, d will be replaced by c, and this process continues until the entire plain text is finished. caesar cipher is a weak method of cryptography. The document discusses symmetric encryption and message confidentiality. it covers symmetric encryption techniques like the data encryption standard (des) and advanced encryption standard (aes).
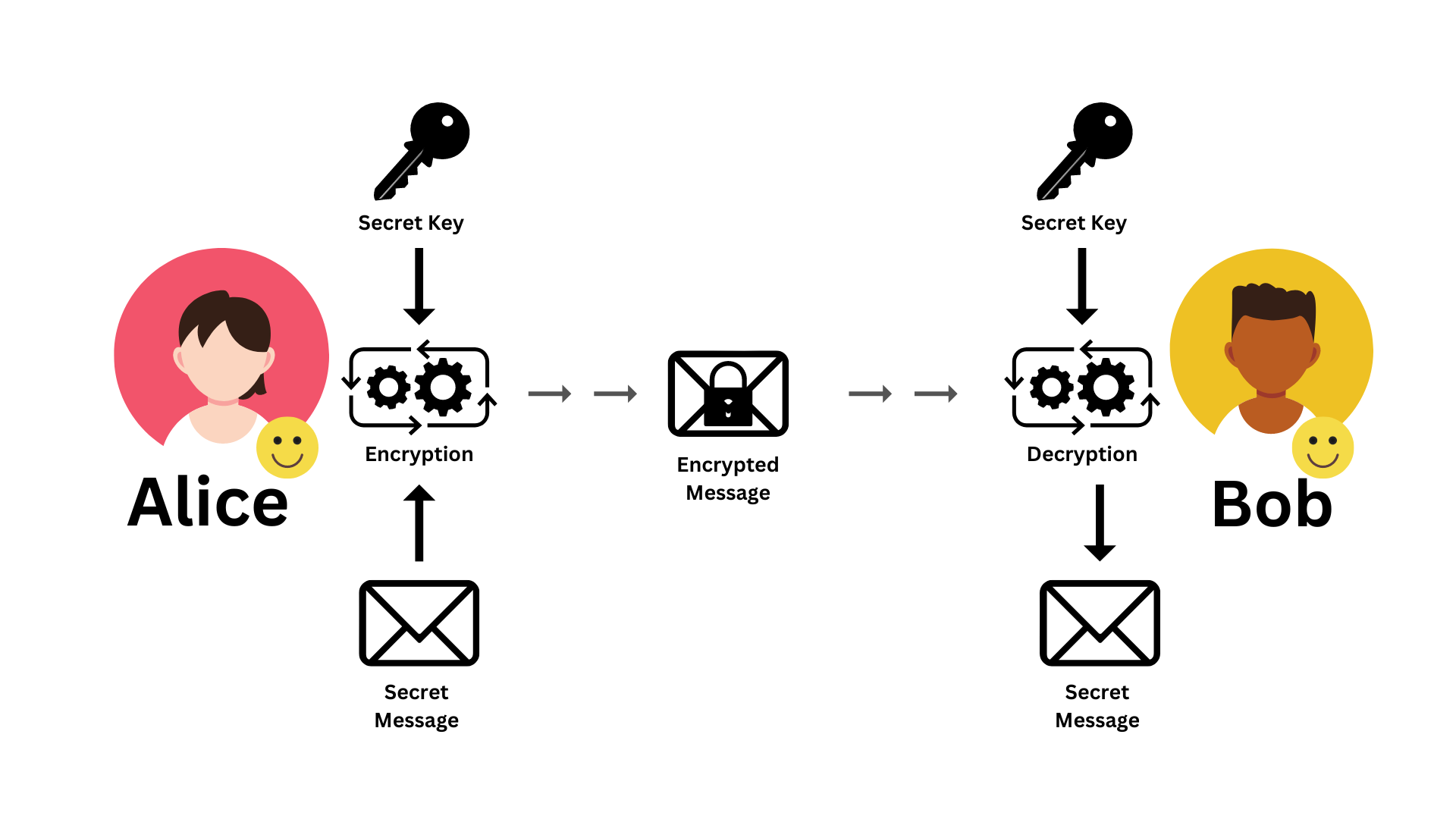
Symmetric Vs Asymmetric Encryption Part 02 Understanding The
Comments are closed.