Using Symmetric And Asymmetric Cryptography Pdf Cryptography

Symmetric And Asymmetric Cryptography Pdf Asymmetric (public key) schemes use a public private key pair where the public key is used by senders to encrypt and only the recipient with the private key can decrypt the message. What are the two fundamental classes of cryptographic mechanisms: symmetric, and asymmetric? what are the important algorithms for symmetric crypto? how are these algorithms used? some of the main asymmetric crypto algorithms: rsa, dh, how do they work? how can they be used? introduction to cryptography. secret key cryptography (symmetric crypto).

Lecture 4 Asymmetric Key Cryptography Part I Pdf Asymmetric systems make it possible to authent2cate messages whose contents must be revealed to an opponent or allow atransmitter whose k has y been compromised to communmate m privacy toa receiver whose k has y been kept secret neither of which is possible using a symmetric c yptosystem. Use cases of symmetric encryption: store a file on a cloud server. you may want to encrypt the file on the server because you can’t trust the cloud provider. the key difference between symmetric and asymmetric cryptography is the number of keys. symmetric cryptography uses 1 key asymmetric cryptography uses 2 keys. Symmetric and asymmetric cryptography overview modern cryptographic methods use a key to control encryption and decryption two classes of key based encryption algorithms. Using symmetric encryption, security requires that each pair of users share a secret key. in an asymmetric system, each user has a public private key pair. keys in the two approaches have very different characteristics and are not directly comparable.

Symmetric Asymmetric Cryptography Ppt Symmetric and asymmetric cryptography overview modern cryptographic methods use a key to control encryption and decryption two classes of key based encryption algorithms. Using symmetric encryption, security requires that each pair of users share a secret key. in an asymmetric system, each user has a public private key pair. keys in the two approaches have very different characteristics and are not directly comparable. Also known as secret key cryptography or conventional cryptography, symmetric key cryptography is an encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message. In this chapter we will look at some classical encryption schemes. we will start by looking at the symmetric encryption schemes. in constrast to asymmetric, or public key encryption, the encryption and decryption keys of the symmetric schemes are the same. definition 1. This paper tells about the study of symmetric and asymmetric key encryption algorithm like aes, des, triple des, rc4, multiphase encryption, rsa, elgamal cryptosystem, digital signature and diffie hellman. Using symmetric and asymmetric encryption together s public key ke. alice generates a random secret k to generate c = fe(m, k). alic encrypts k by ke t generate l = fd(c, k).
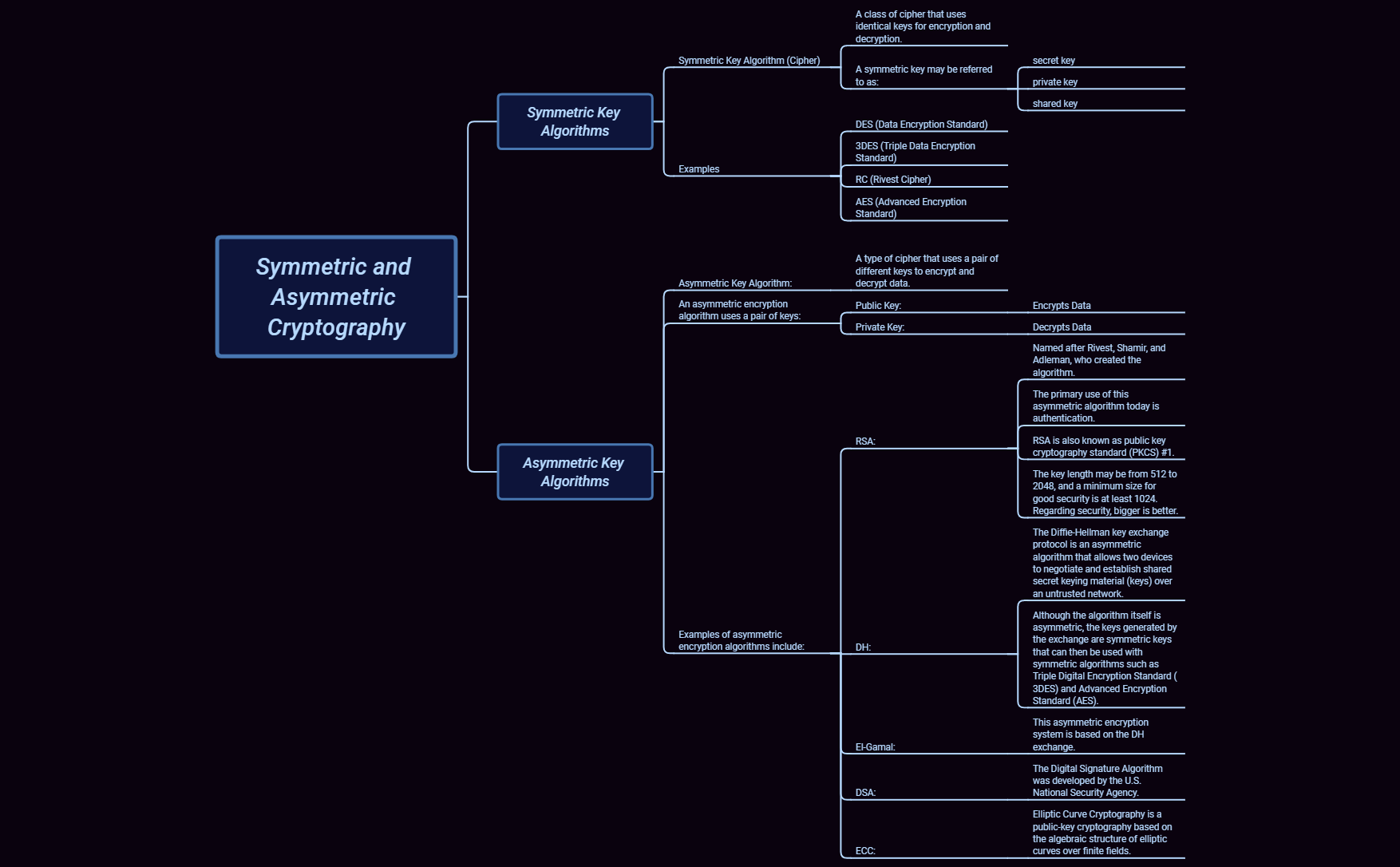
6 1 2 Symmetric And Asymmetric Cryptography Cvumftgqul Xmind Also known as secret key cryptography or conventional cryptography, symmetric key cryptography is an encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message. In this chapter we will look at some classical encryption schemes. we will start by looking at the symmetric encryption schemes. in constrast to asymmetric, or public key encryption, the encryption and decryption keys of the symmetric schemes are the same. definition 1. This paper tells about the study of symmetric and asymmetric key encryption algorithm like aes, des, triple des, rc4, multiphase encryption, rsa, elgamal cryptosystem, digital signature and diffie hellman. Using symmetric and asymmetric encryption together s public key ke. alice generates a random secret k to generate c = fe(m, k). alic encrypts k by ke t generate l = fd(c, k).

Symmetric And Asymmetric Key Cryptography Ppt This paper tells about the study of symmetric and asymmetric key encryption algorithm like aes, des, triple des, rc4, multiphase encryption, rsa, elgamal cryptosystem, digital signature and diffie hellman. Using symmetric and asymmetric encryption together s public key ke. alice generates a random secret k to generate c = fe(m, k). alic encrypts k by ke t generate l = fd(c, k).
Comments are closed.