Using C99 Shell Hacking
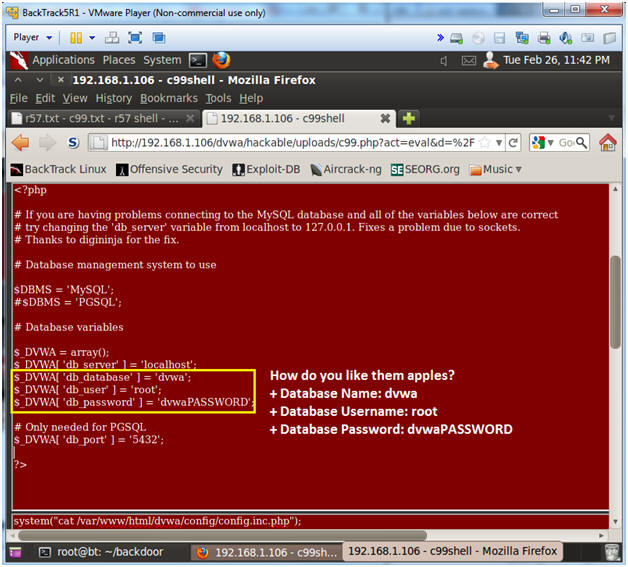
Shell C99 Php For Baplogin In this article we will learn about the infamous c99 shell. in our previous tutorial rfi hacking for beginners we learnt what is remote file inclusion vulnerability and how hackers use this vulnerability to upload files into the web server. There are numerous c99 variants which infect vulnerable web application to give hackers a gui. the shell lets the attacker take control of the server and also browse the file system, upload, edit, delete, view files and even change file permissions amongst other dangerous actions.

Shell C99 Php For Opmdata Iemtab.gob.mx intro website hack (defacement) with shell c99. a simple example of how to use in a government website server: estado de tabasco, méx. The c99 shell type used in most attacks can be detected by a significant number of antivirus software. experts also can identify it by its common file name and url, pagat.txt. I uploaded a shell on the site. this site saves files without extension. when i want to use the shell, suddenly the download page comes to me and i can’t use it. example: domain uploads 1nsd2k233kjk56f. The c99 shell lets the attacker take control of the processes of the internet server, allowing him or her give commands on the server as the account under which the threat is operating.
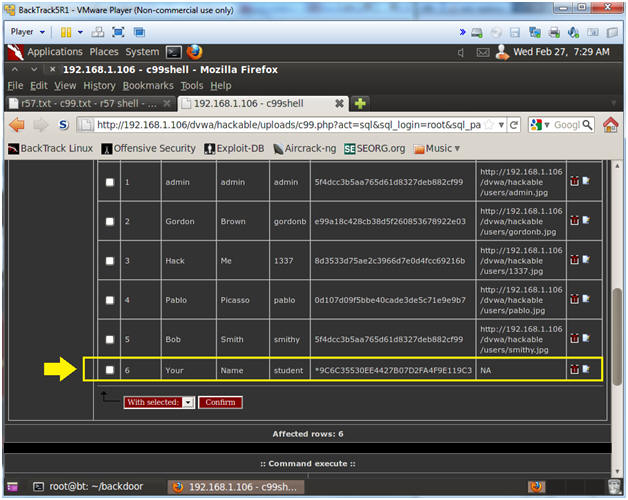
Shell C99 Php For Plmcampus I uploaded a shell on the site. this site saves files without extension. when i want to use the shell, suddenly the download page comes to me and i can’t use it. example: domain uploads 1nsd2k233kjk56f. The c99 shell lets the attacker take control of the processes of the internet server, allowing him or her give commands on the server as the account under which the threat is operating. What is c99 ? the c99 php utility provides functionality for listing files, brute forcing ftp passwords, updating itself, executing shell commands and php code. it also provides for connecting to mysql databases, and initiating a connect back shell session. The c99 variant is a php based web shell, often considered as malware, that hackers upload to vulnerable web applications to gain control of the internet server. by exploiting the vulnerability, attackers can use the c99 shell to access the server processes, issue commands, and operate as the account under which the threat is operating. About c99 php web shell for ethical hacking and penetration testing — file manager, command execution, and server control in one script. The c99 shell script is a php script. it would normally be uploaded as a file and then it gets browsed to in order to execute it. it would only be possible to execute it on your server if the file extension that it was uploaded as was one that the server has been configured to parse as php code.
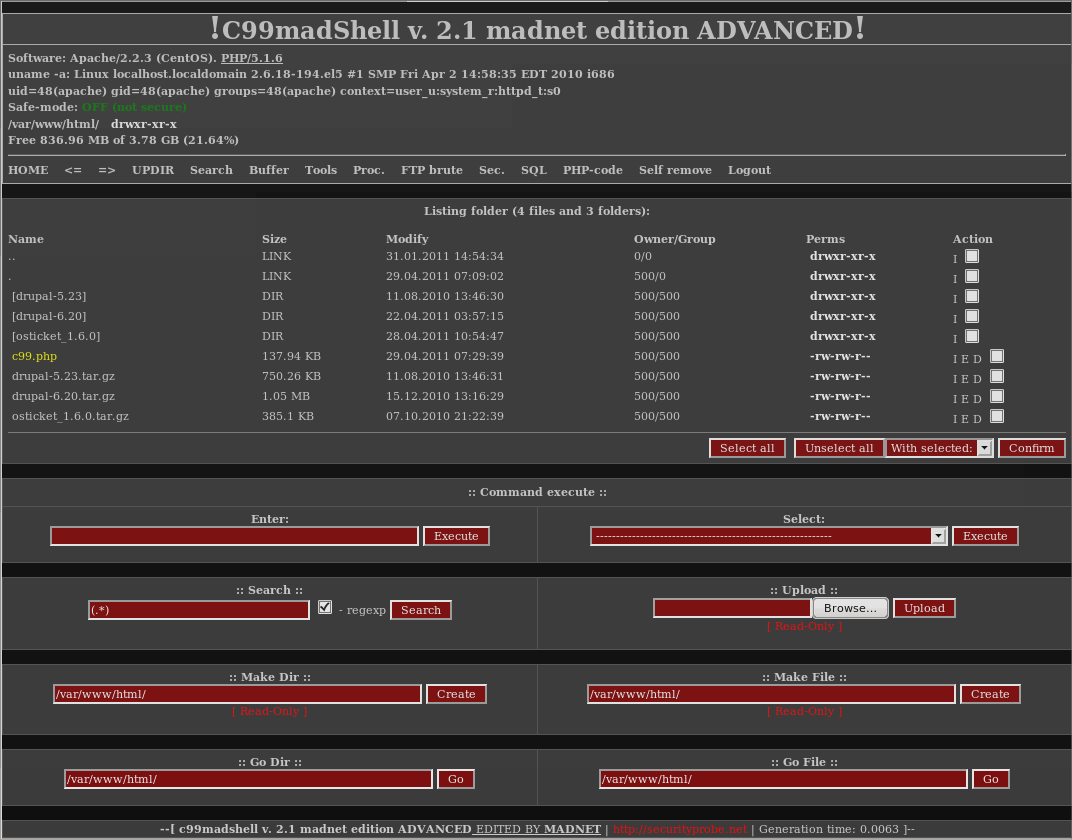
Shell C99 Php For Lasopabell What is c99 ? the c99 php utility provides functionality for listing files, brute forcing ftp passwords, updating itself, executing shell commands and php code. it also provides for connecting to mysql databases, and initiating a connect back shell session. The c99 variant is a php based web shell, often considered as malware, that hackers upload to vulnerable web applications to gain control of the internet server. by exploiting the vulnerability, attackers can use the c99 shell to access the server processes, issue commands, and operate as the account under which the threat is operating. About c99 php web shell for ethical hacking and penetration testing — file manager, command execution, and server control in one script. The c99 shell script is a php script. it would normally be uploaded as a file and then it gets browsed to in order to execute it. it would only be possible to execute it on your server if the file extension that it was uploaded as was one that the server has been configured to parse as php code.
Comments are closed.