Unlocking Quantum Safe Security Post Quantum Cryptography Explained

Quantum Cryptography Explained Quantum Garage PQC is a field of cryptography that uses complex mathematics to protect data and systems from quantum computing attacks Post-quantum cryptography represents a fundamental shift in how digital security will be implemented across all computing platforms
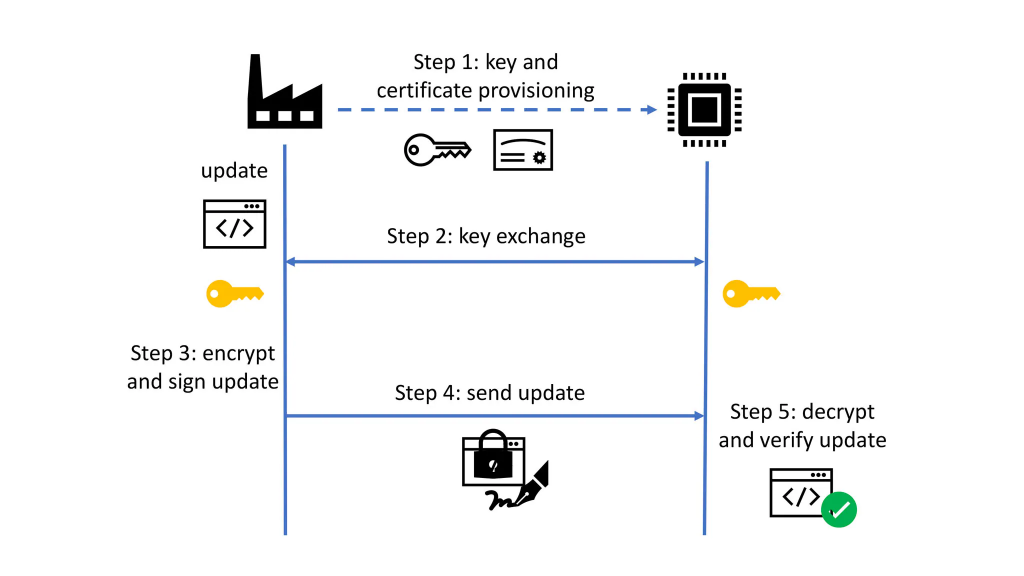
Quantum Cryptography Vs Post Quantum Cryptography Major Difference Google announced on Thursday the development of quantum-safe digital signatures (FIPS 204/FIPS 205) in Google Cloud Key Management Service (Cloud KMS) for software-based keys This is available in With the release today, F5 is looking to simplify the shift to quantum-safe protections through an integrated, scalable platform for application delivery and security Enhance your cyber resilience with Commvault's expanded post-quantum cryptography capabilities, safeguarding sensitive data from quantum threats with cutting-edge, cryptographic solutions Discover These approaches typically layer quantum-safe algorithms alongside traditional cryptography, ensuring protection against both conventional and quantum threats while minimizing disruption

Quantum Cryptography Vs Post Quantum Cryptography Major Difference Enhance your cyber resilience with Commvault's expanded post-quantum cryptography capabilities, safeguarding sensitive data from quantum threats with cutting-edge, cryptographic solutions Discover These approaches typically layer quantum-safe algorithms alongside traditional cryptography, ensuring protection against both conventional and quantum threats while minimizing disruption Post-quantum cryptography algorithms, such as ML-KEM, which is based on the mathematical properties of structured lattices, are able to withstand attacks from both classical and quantum computers For World Quantum Day, we talked with Tuta Mail about the threats that quantum computers pose to encryption, the need to switch to quantum-resistant cryptography today, and the company's work in Download the PQC Migration Roadmap to gain insights into how your organization can prepare for the future of quantum-safe security IBM's Quantum Safe platform aims to protect organizations from future quantum threats to classical cryptography
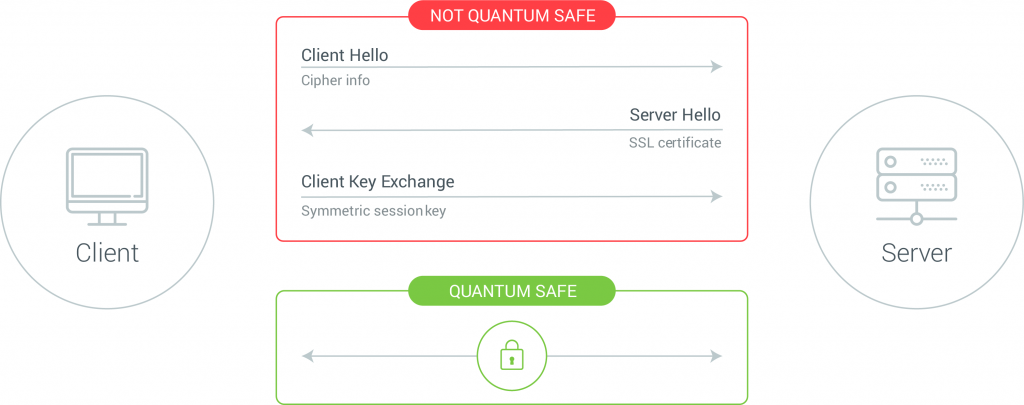
Quantum Cryptography Vs Post Quantum Cryptography Major Difference Post-quantum cryptography algorithms, such as ML-KEM, which is based on the mathematical properties of structured lattices, are able to withstand attacks from both classical and quantum computers For World Quantum Day, we talked with Tuta Mail about the threats that quantum computers pose to encryption, the need to switch to quantum-resistant cryptography today, and the company's work in Download the PQC Migration Roadmap to gain insights into how your organization can prepare for the future of quantum-safe security IBM's Quantum Safe platform aims to protect organizations from future quantum threats to classical cryptography The world’s first post-quantum cryptography standards have been formalized by the US National Institute of Standards & Technology (NIST) The standards provide organizations with a framework to secure

Ibm Launches Free Online Course On Quantum Safe Cryptography For Developers Download the PQC Migration Roadmap to gain insights into how your organization can prepare for the future of quantum-safe security IBM's Quantum Safe platform aims to protect organizations from future quantum threats to classical cryptography The world’s first post-quantum cryptography standards have been formalized by the US National Institute of Standards & Technology (NIST) The standards provide organizations with a framework to secure
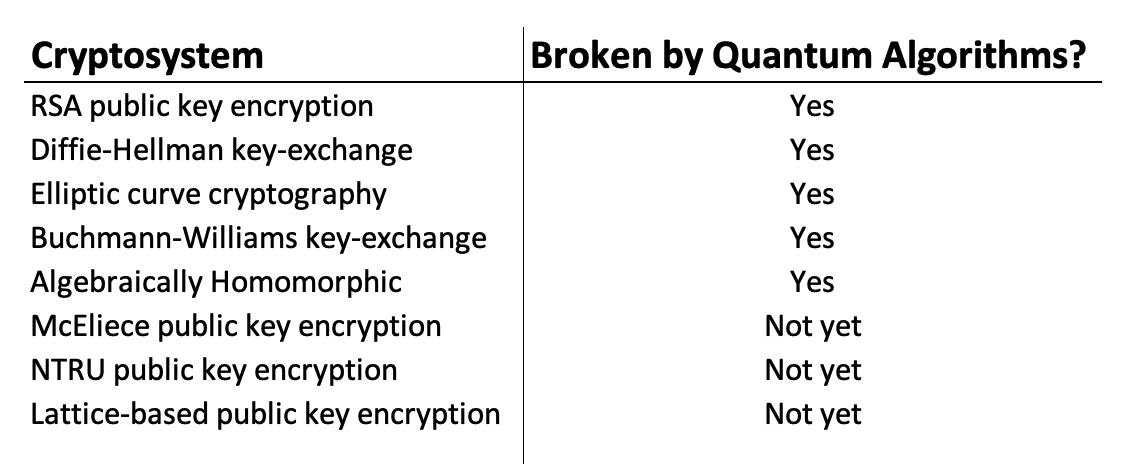
Post Quantum Cryptography Quantumeon The world’s first post-quantum cryptography standards have been formalized by the US National Institute of Standards & Technology (NIST) The standards provide organizations with a framework to secure
Comments are closed.