Terraform Plan For Azure Actions Github Marketplace Github
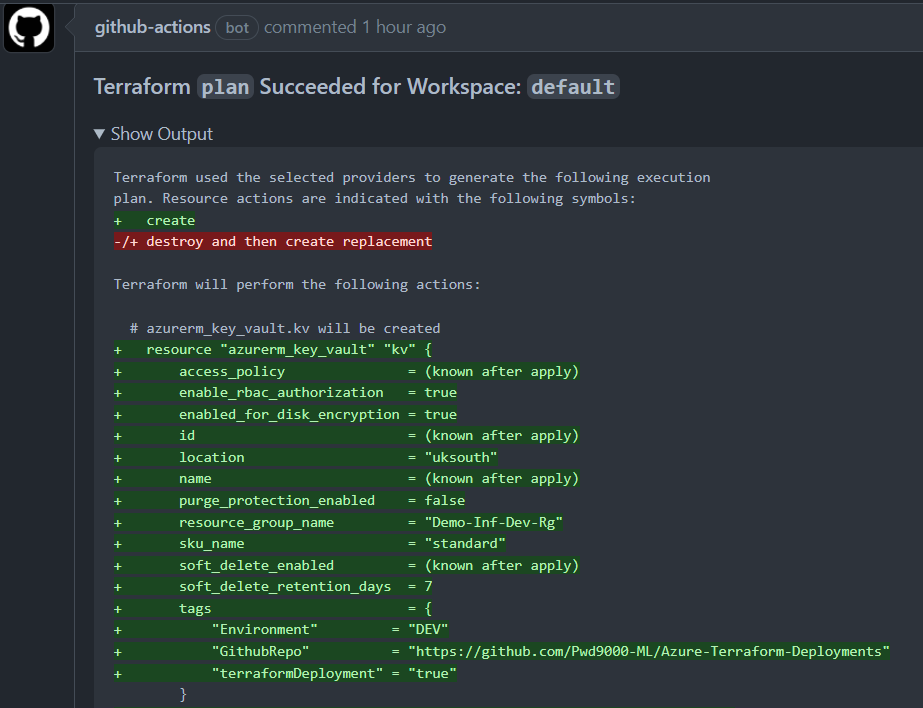
Terraform Plan For Azure Actions Github Marketplace Github Forgot password? sign in with terraform sso. need to sign up? create your free account. view terraform offerings to find out which one is right for you. Registryplease enable javascript to use this application.
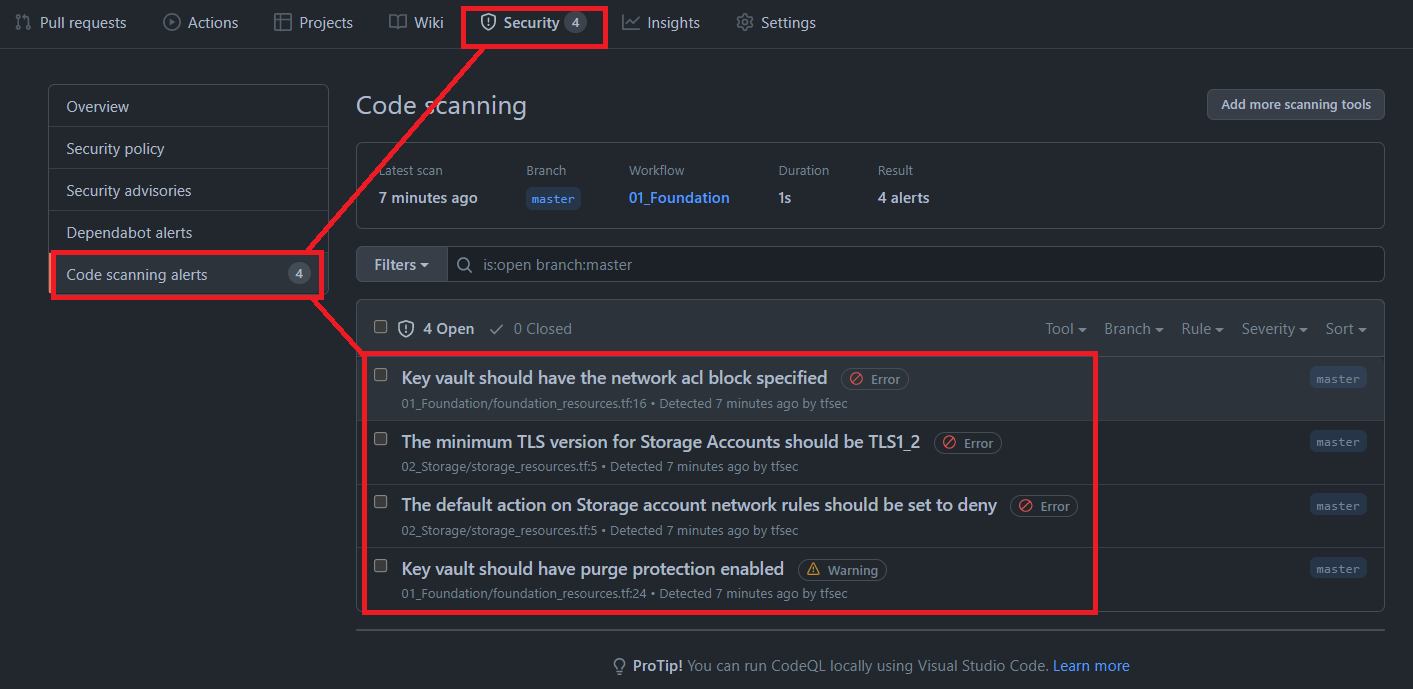
Terraform Plan For Azure Actions Github Marketplace Github To learn the basics of terraform using this provider, follow the hands on get started tutorials. interact with aws services, including lambda, rds, and iam by following the aws services tutorials. Providers providers are a logical abstraction of an upstream api. they are responsible for understanding api interactions and exposing resources. If you use ebs block device on an aws instance, terraform will assume management over the full set of non root ebs block devices for the instance, treating additional block devices as drift. Terraform currently provides both a standalone subnet resource, and allows for subnets to be defined in line within the virtual network resource. at this time you cannot use a virtual network with in line subnets in conjunction with any subnet resources.
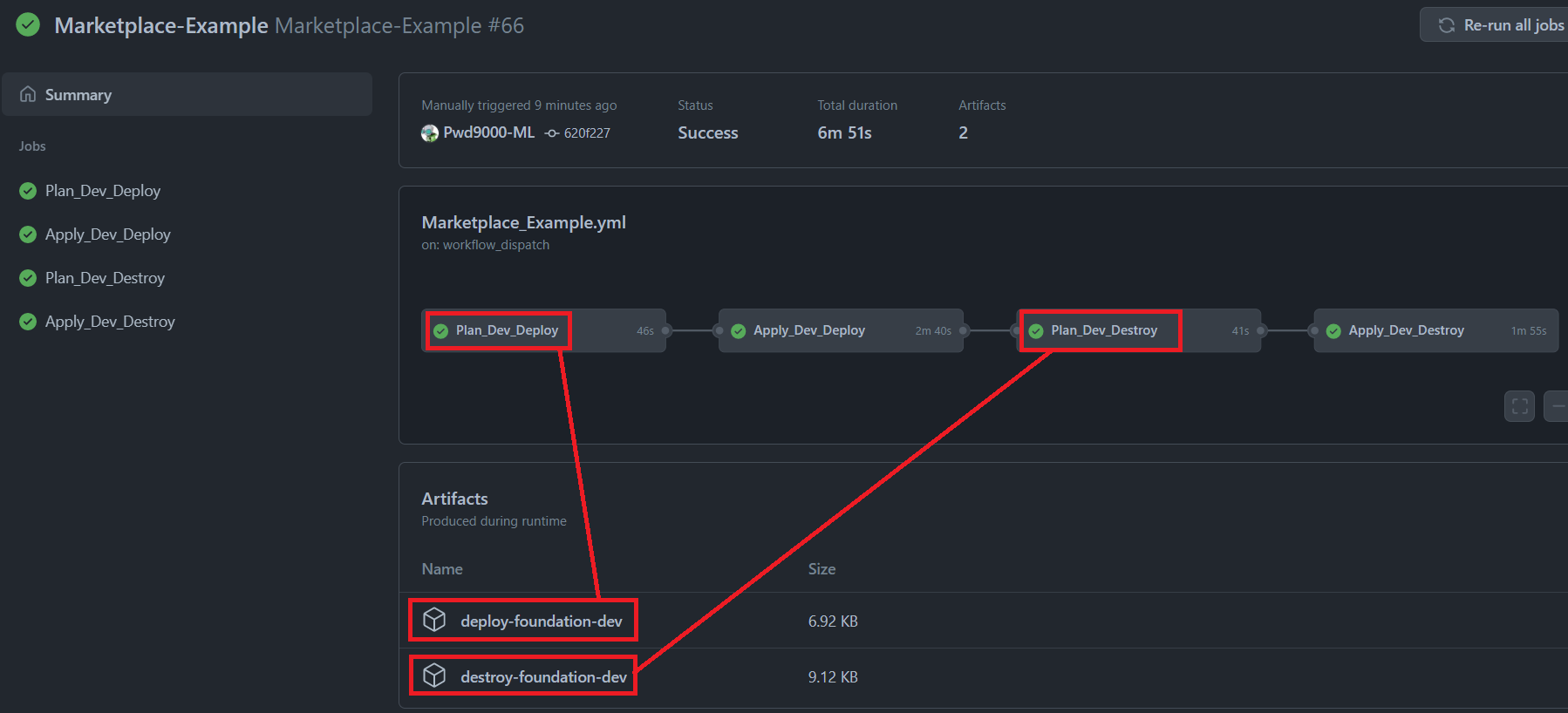
Terraform Plan For Azure Actions Github Marketplace Github If you use ebs block device on an aws instance, terraform will assume management over the full set of non root ebs block devices for the instance, treating additional block devices as drift. Terraform currently provides both a standalone subnet resource, and allows for subnets to be defined in line within the virtual network resource. at this time you cannot use a virtual network with in line subnets in conjunction with any subnet resources. If you're new to the azuread provider, check out our learn tutorial, which guides practitioners through learning the terraform configuration language and the azuread provider, with an example workflow for managing users and groups. If you use logging on an aws s3 bucket, terraform will assume management over the full set of logging parameters for the s3 bucket, treating additional logging parameters as drift. You can utilize the generic terraform resource lifecycle configuration block with ignore changes to create an eks node group with an initial size of running instances, then ignore any changes to that count caused externally (e.g., application autoscaling). Terraform providers for various cloud providers feature resources to spin up managed kubernetes clusters on services such as eks, aks and gke. such resources (or data sources) will have attributes that expose the credentials needed for the kubernetes provider to connect to these clusters.
Terraform Plan For Azure Actions Github Marketplace Github If you're new to the azuread provider, check out our learn tutorial, which guides practitioners through learning the terraform configuration language and the azuread provider, with an example workflow for managing users and groups. If you use logging on an aws s3 bucket, terraform will assume management over the full set of logging parameters for the s3 bucket, treating additional logging parameters as drift. You can utilize the generic terraform resource lifecycle configuration block with ignore changes to create an eks node group with an initial size of running instances, then ignore any changes to that count caused externally (e.g., application autoscaling). Terraform providers for various cloud providers feature resources to spin up managed kubernetes clusters on services such as eks, aks and gke. such resources (or data sources) will have attributes that expose the credentials needed for the kubernetes provider to connect to these clusters.
Workflow Runs Azure Samples Terraform Github Actions Github You can utilize the generic terraform resource lifecycle configuration block with ignore changes to create an eks node group with an initial size of running instances, then ignore any changes to that count caused externally (e.g., application autoscaling). Terraform providers for various cloud providers feature resources to spin up managed kubernetes clusters on services such as eks, aks and gke. such resources (or data sources) will have attributes that expose the credentials needed for the kubernetes provider to connect to these clusters.
Github Pliyo Terraform Azure Github Actions Deploying To Azure Using
Comments are closed.