Symmetric Vs Asymmetric Encryption Part 02 Understanding The

Symmetric Vs Asymmetric Encryption Which Is Better For Data Security Step 01: alice encrypts her secret message with the agreed symmetric encryption algorithm and key. step 02: then alice sends the cipher to bob through the unsecured network. Symmetric encryption offers speed and efficiency, making it suitable for bulk data encryption, while asymmetric encryption provides enhanced security for key exchange and authentication purposes.
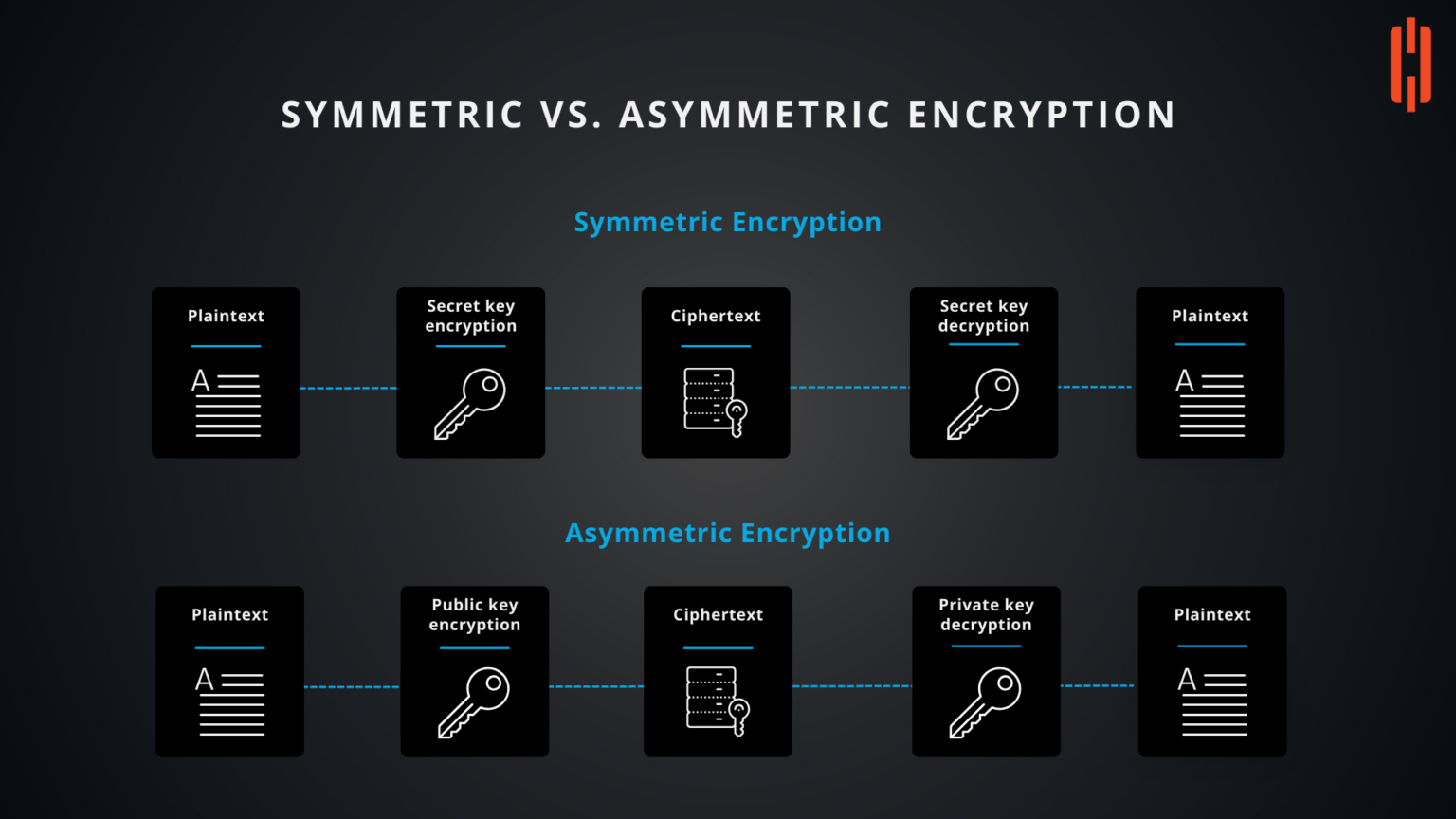
Symmetric Vs Asymmetric Encryption Part 02 Understanding The In part 2 of the encryption 101 series, we dive deeper into the two most important types of encryption: symmetric and asymmetric. Symmetric encryption requires a secure method for sharing keys between sender and receiver. asymmetric encryption simplifies key management as the public key can be shared openly while the private key remains secure. You'll learn how symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption employs a public and private key pair for secure key exchange. In a nutshell, symmetric encryption uses a single secret key, while asymmetric encryption involves a secret key pair. let's look at the two types of encryption, their pros and cons, use cases, and which to use when.
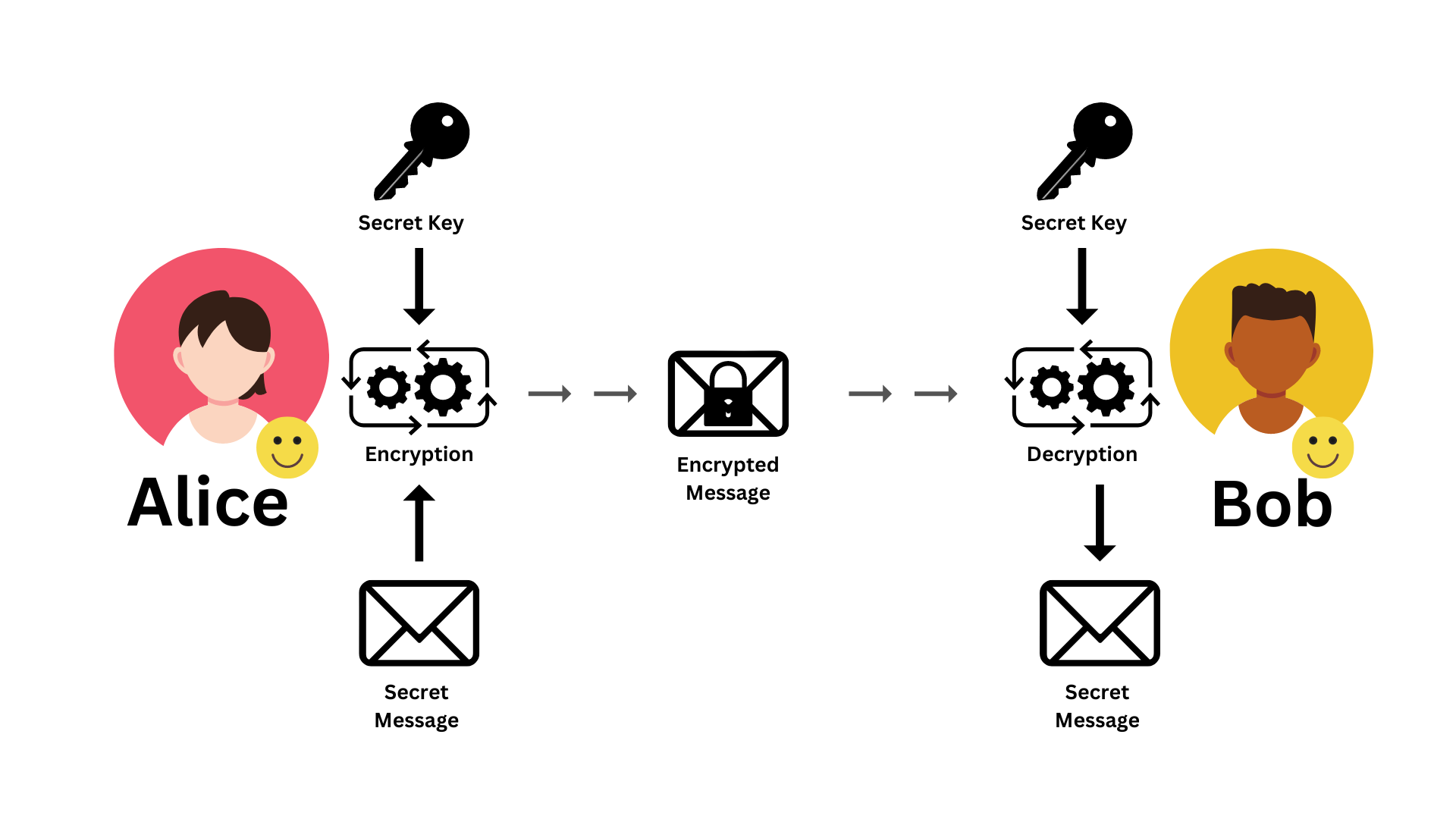
Symmetric Vs Asymmetric Encryption Part 02 Understanding The You'll learn how symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption employs a public and private key pair for secure key exchange. In a nutshell, symmetric encryption uses a single secret key, while asymmetric encryption involves a secret key pair. let's look at the two types of encryption, their pros and cons, use cases, and which to use when. Asymmetric or public key cryptography is the form of encryption that involves using public and private keys for encryption and decryption. in asymmetric encryption, the sender uses the. Two of the most widely used methods — symmetric encryption and asymmetric encryption — serve different purposes, yet they often work together in modern security systems. in this blog post, we’ll break down the key differences, real world uses, and how both encryption types form the bedrock of secure communication. In this article, we’ll get into the two primary types of encryption: symmetric and asymmetric. by the end, you’ll have a comprehensive understanding of their differences, strengths, and weaknesses. before diving into the specifics, let’s first establish a foundational understanding of encryption. Step 01: alice encrypts her secret message with the agreed symmetric encryption algorithm and key. step 02: then alice sends the cipher to bob through the unsecured network.

Symmetric Vs Asymmetric Encryption Byte Man Asymmetric or public key cryptography is the form of encryption that involves using public and private keys for encryption and decryption. in asymmetric encryption, the sender uses the. Two of the most widely used methods — symmetric encryption and asymmetric encryption — serve different purposes, yet they often work together in modern security systems. in this blog post, we’ll break down the key differences, real world uses, and how both encryption types form the bedrock of secure communication. In this article, we’ll get into the two primary types of encryption: symmetric and asymmetric. by the end, you’ll have a comprehensive understanding of their differences, strengths, and weaknesses. before diving into the specifics, let’s first establish a foundational understanding of encryption. Step 01: alice encrypts her secret message with the agreed symmetric encryption algorithm and key. step 02: then alice sends the cipher to bob through the unsecured network.
Symmetric Vs Asymmetric Encryption Understanding The Differences In this article, we’ll get into the two primary types of encryption: symmetric and asymmetric. by the end, you’ll have a comprehensive understanding of their differences, strengths, and weaknesses. before diving into the specifics, let’s first establish a foundational understanding of encryption. Step 01: alice encrypts her secret message with the agreed symmetric encryption algorithm and key. step 02: then alice sends the cipher to bob through the unsecured network.
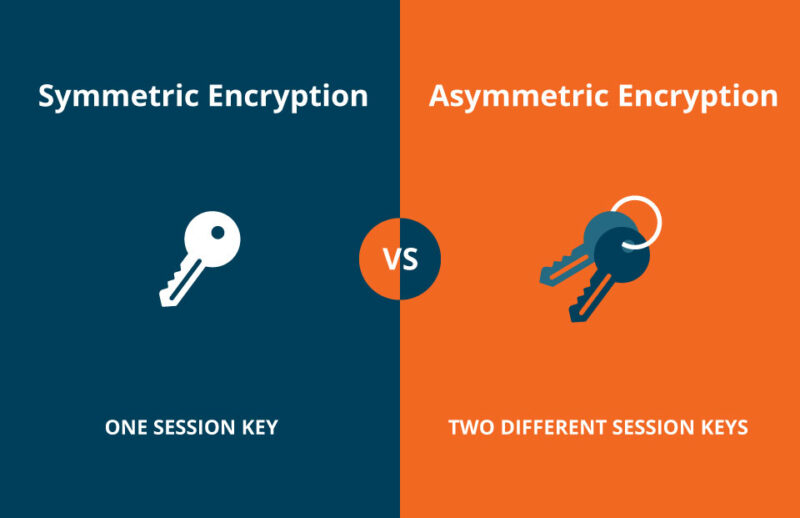
What Is The Difference Between Symmetric And Asymmetric Encryption
Comments are closed.