Symmetric Key Cryptography Stream Cipher Block Cipher Explained Network Security Simplilearn
Symmetric Key Cryptography Stream Cipher Block Cipher Explained Here, we take a small recap into cryptography, the working and applications of symmetric key cryptography, and its advantages. we also have stream cipher and block cipher. Block cipher and stream cipher are the types of symmetric key cipher. these two block ciphers are used to transform plain text into ciphertext. the difference between a block cipher and a stream cipher is that the block cipher transforms the plain text into cipher text by taking the plain text block by block.
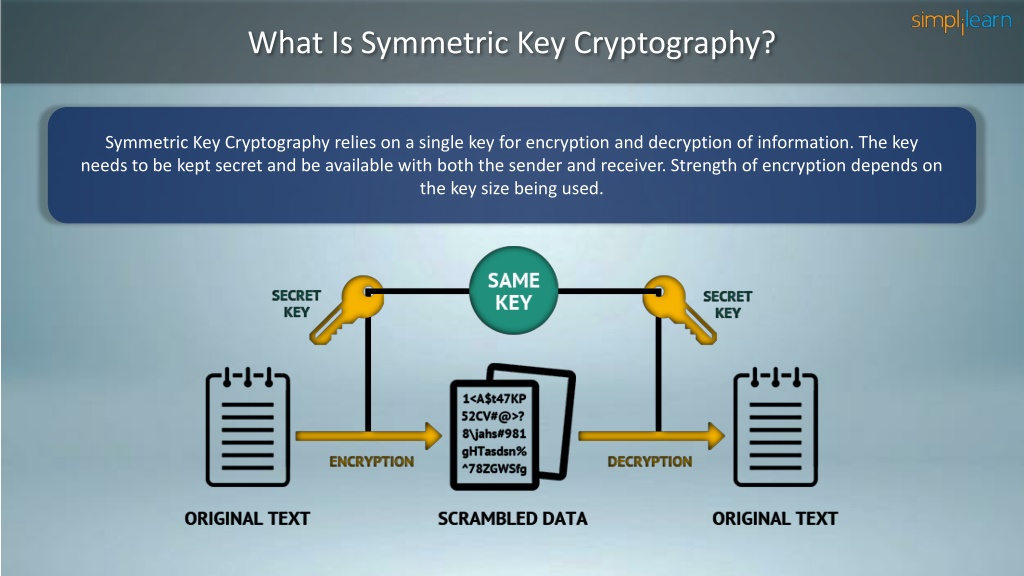
Ppt Symmetric Key Cryptography Stream Cipher Block Cipher This presentation on symmetric key cryptography will acquaint you with the the process of symmetric encryption and decryption. here, we take a small recap into cryptography, the working and applications of symmetric key cryptography, and it's advantages. we also have stream ciphers and block. Approved for use since the 1970s, symmetric key encryption algorithms are just one way to keep confidential data secure. take a look at the different algorithms, from des to aes and their spinoffs, and learn the math behind the crucial cryptography functionality. Secret (symmetric) key functions: one key shared secret key is used for both encryption and decryption. Explain the importance and application of each of confidentiality, integrity, authentication and availability and to understand various cryptographic algorithms. generate and distribute a pgp key pair and use the pgp package to send an encrypted e mail message. unit i.
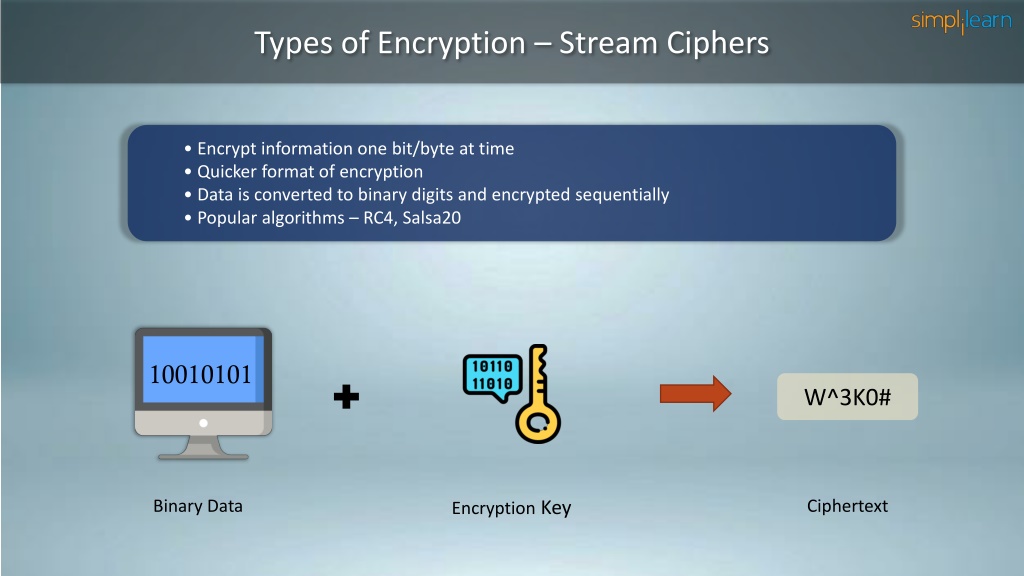
Ppt Symmetric Key Cryptography Stream Cipher Block Cipher Secret (symmetric) key functions: one key shared secret key is used for both encryption and decryption. Explain the importance and application of each of confidentiality, integrity, authentication and availability and to understand various cryptographic algorithms. generate and distribute a pgp key pair and use the pgp package to send an encrypted e mail message. unit i. Stream ciphers can be classified as either synchronous or self synchronising. in a synchronous stream cipher, depicted in figure 7, the keystream output is a function of a key, and is generated independently of the plaintext and the ciphertext. Although block ciphers are not ind cpa secure, they have a desirable security property that will help us build ind cpa secure symmetric encryption schemes: namely, a block cipher is computationally indistinguishable from a random permutation. Based on using a random looking permutation. 8 16 machine operations per output byte. very long cipher period (over 10100). widely believed to be secure. used for encryption in ssl web protocol. Symmetric key cryptography is a method used in cybersecurity to protect information. it’s like having a secret code that only the sender and receiver know. this code, called a “key”, and used to both lock (encrypt) and unlock (decrypt) the information. imagine sending a locked box through the mail.
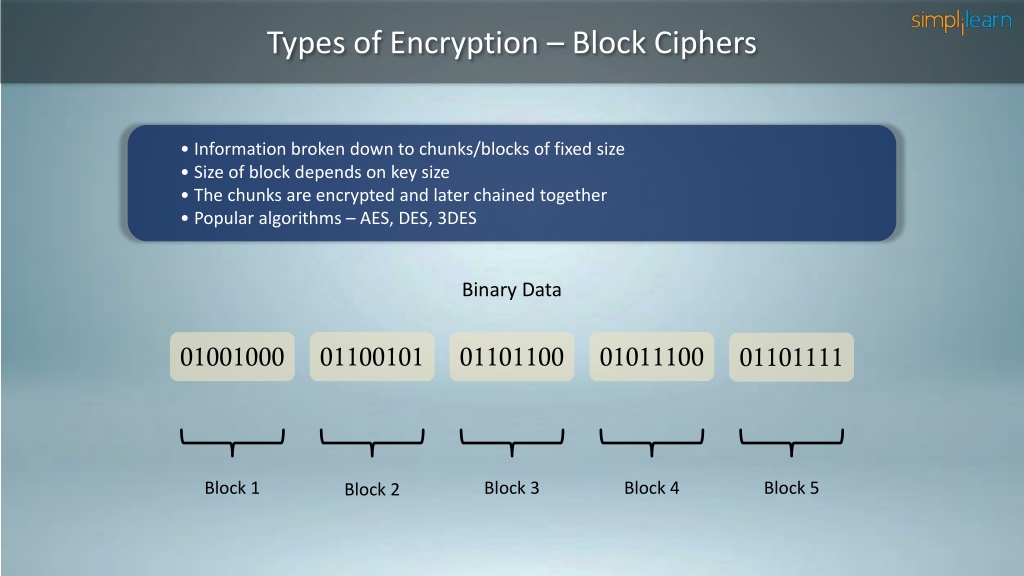
Ppt Symmetric Key Cryptography Stream Cipher Block Cipher Stream ciphers can be classified as either synchronous or self synchronising. in a synchronous stream cipher, depicted in figure 7, the keystream output is a function of a key, and is generated independently of the plaintext and the ciphertext. Although block ciphers are not ind cpa secure, they have a desirable security property that will help us build ind cpa secure symmetric encryption schemes: namely, a block cipher is computationally indistinguishable from a random permutation. Based on using a random looking permutation. 8 16 machine operations per output byte. very long cipher period (over 10100). widely believed to be secure. used for encryption in ssl web protocol. Symmetric key cryptography is a method used in cybersecurity to protect information. it’s like having a secret code that only the sender and receiver know. this code, called a “key”, and used to both lock (encrypt) and unlock (decrypt) the information. imagine sending a locked box through the mail.

Stream Cipher And Block Cipher 1 Stream Cipher Based on using a random looking permutation. 8 16 machine operations per output byte. very long cipher period (over 10100). widely believed to be secure. used for encryption in ssl web protocol. Symmetric key cryptography is a method used in cybersecurity to protect information. it’s like having a secret code that only the sender and receiver know. this code, called a “key”, and used to both lock (encrypt) and unlock (decrypt) the information. imagine sending a locked box through the mail.
Comments are closed.