Symmetric Algorithms Types Of Symmetric Algorithms

Symmetric Key Algorithm Pdf Guide to symmetric algorithms. we discuss the introduction and types of symmetric algorithms along with des & triple des. Symmetric key algorithms require both the sender and the recipient of a message to have the same secret key. all early cryptographic systems required either the sender or the recipient to somehow receive a copy of that secret key over a physically secure channel.
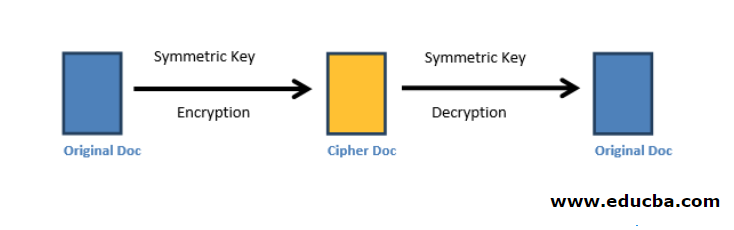
Symmetric Algorithms Types Of Symmetric Algorithms In this article, we will cover the techniques used in symmetric key cryptography, its applications, principles on which it works, its types and limitations as well as what type of attacks in the digital world it gets to face. Some popular symmetric encryption algorithms are: aes, chacha20, cast, twofish, idea, serpent, rc5, rc6, camellia and aria. all these algorithms are considered secure (when configured and used correctly). There are two types of symmetric algorithms (or ciphers): stream and block. a block cipher divides the data into blocks (often 64 bit blocks, but newer algorithms sometimes use 128 bit blocks) and encrypts the data one block at a time. What is symmetric key algorithms? symmetric key algorithms are a type of cryptographic technique that uses a shared secret key for both encryption and decryption. this means that the same key is used to encode and decode the message.
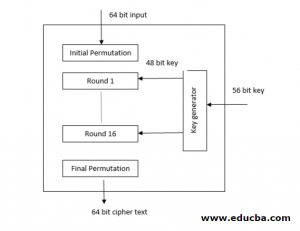
Symmetric Algorithms Types Of Symmetric Algorithms There are two types of symmetric algorithms (or ciphers): stream and block. a block cipher divides the data into blocks (often 64 bit blocks, but newer algorithms sometimes use 128 bit blocks) and encrypts the data one block at a time. What is symmetric key algorithms? symmetric key algorithms are a type of cryptographic technique that uses a shared secret key for both encryption and decryption. this means that the same key is used to encode and decode the message. There are two basic types of cryptography: symmetric key and asymmetric key. symmetric key algorithms are the quickest and most commonly used type of encryption. here, a single key is used for both encryption and decryption. there are few well known symmetric key algorithms i.e. des, rc2, rc4, idea etc. Defines the structure and operations that an algorithm can perform, its characteristics and how they are implemented. it also determines that the algorithm is symmetric or asymmetric that is whether it makes use of secret key or public key for encryption and decryption. Applying the symmetric key algorithms is divided into six simple steps, which gets followed by a myriad of the same type of algorithms. often the most crucial task is to decide on an. Symmetric key algorithms: are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. the keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link.
Comments are closed.