Streamlining Kubernetes With Configmap And Secrets
Kubernetes 101 Configmap Secrets Master the art of using configmap & secrets in kubernetes. get insights on their crucial role and learn to manage them seamlessly with devtron. kubernetes configmap is an essential tool for managing configuration data within containerized applications. Secrets and configmaps are kubernetes resources designed to separate the configuration and sensitive information from the application code in a centralized manner. however, each of them has specific use cases and exhibits distinct behavior. in this tutorial, we’ll explore some prominent differences between configmaps and secrets in kubernetes. 2.

Understanding Kubernetes Configmap And Secrets With Examples In this blog, we’ll explore both — with hands on commands, yaml examples, and clear explanations to help you use them effectively in real world kubernetes clusters. 🧾 what is a configmap? a. In this article, we’ll explore how to effectively use configmaps and secrets in kubernetes to manage configurations and sensitive data while ensuring security and flexibility. what are configmaps in kubernetes? configmaps are kubernetes resources used to store non sensitive configuration data. Configmaps and secrets are vital tools in the kubernetes arsenal, helping you configure applications efficiently and keep sensitive data secure. by understanding their roles and following best practices, you can ensure that your kubernetes applications run smoothly and safely in any environment. Configmaps and secrets are essential components of kubernetes that streamline the management of configuration data and sensitive information. by using these resources and the provided commands, you can ensure your applications remain configurable, secure, and maintainable, even at scale. 🚢.

Exploration Of Kubernetes Configmap Secrets Configmaps and secrets are vital tools in the kubernetes arsenal, helping you configure applications efficiently and keep sensitive data secure. by understanding their roles and following best practices, you can ensure that your kubernetes applications run smoothly and safely in any environment. Configmaps and secrets are essential components of kubernetes that streamline the management of configuration data and sensitive information. by using these resources and the provided commands, you can ensure your applications remain configurable, secure, and maintainable, even at scale. 🚢. Use it for: environment settings (like log level, api base url) hostnames, ports, feature flags complete config files or cli arguments. secrets are also key value stores but for private data: kubernetes encodes all secret values in base64 (for transport, not real security). decode with echo c3vwzxjzzwnyzxq= | base64 d. Kubernetes configmaps and secrets play a vital role in application configuration and data security. they help streamline deployments, enforce separation of concerns, and protect your infrastructure against misconfiguration and data leaks. This post will guide you through creating and using both configmaps and secrets with practical examples, code blocks, and diagrams to help you master kubernetes configuration management. a. Configmaps in kubernetes provide a way to decouple configuration artifacts from container images, enabling better manageability and flexibility. here’s how you can use configmaps: you can create configmaps using yaml manifests or command line tools like kubectl. below is an example yaml manifest for creating a configmap:.
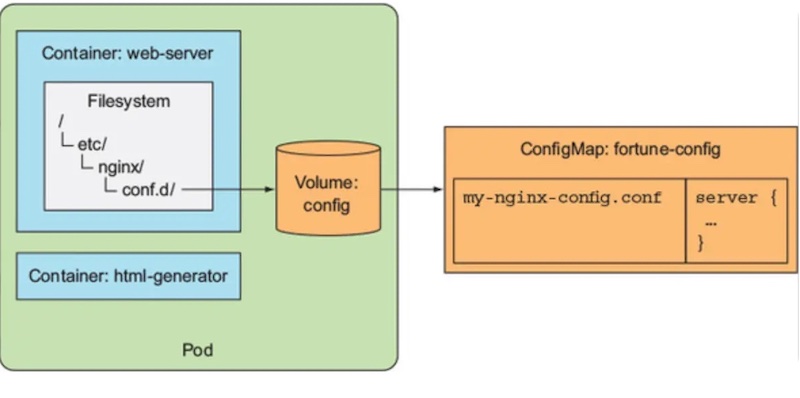
Kubernetes Configmap Guide Shaun Yuan Use it for: environment settings (like log level, api base url) hostnames, ports, feature flags complete config files or cli arguments. secrets are also key value stores but for private data: kubernetes encodes all secret values in base64 (for transport, not real security). decode with echo c3vwzxjzzwnyzxq= | base64 d. Kubernetes configmaps and secrets play a vital role in application configuration and data security. they help streamline deployments, enforce separation of concerns, and protect your infrastructure against misconfiguration and data leaks. This post will guide you through creating and using both configmaps and secrets with practical examples, code blocks, and diagrams to help you master kubernetes configuration management. a. Configmaps in kubernetes provide a way to decouple configuration artifacts from container images, enabling better manageability and flexibility. here’s how you can use configmaps: you can create configmaps using yaml manifests or command line tools like kubectl. below is an example yaml manifest for creating a configmap:.
Kubernetes Configmap How Configmap Works In Kubernetes This post will guide you through creating and using both configmaps and secrets with practical examples, code blocks, and diagrams to help you master kubernetes configuration management. a. Configmaps in kubernetes provide a way to decouple configuration artifacts from container images, enabling better manageability and flexibility. here’s how you can use configmaps: you can create configmaps using yaml manifests or command line tools like kubectl. below is an example yaml manifest for creating a configmap:.
Kubernetes Configmap Examples
Comments are closed.