Some Tricks Of Symmetric Cryptography

Unit 2 Symmetric Key Techniques Part 1 Pdf Cryptography Cipher Cryptography is the art of keeping information secret and safe by transforming it into form that unintended recipients cannot understand It makes secure data transmission over the internet possible Engineers and technologists must adapt to larger key sizes and novel cryptographic methods and actively contribute to the development of quantum-resistant systems
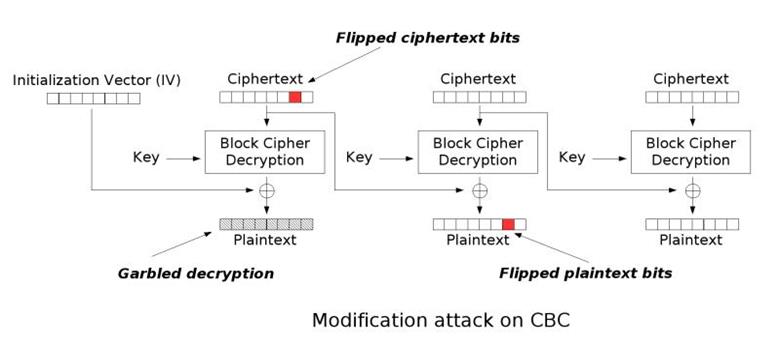
Some Tricks Of Symmetric Cryptography In every cryptography scheme, the origin of this asymmetry is a mathematical object called a one-way function, which transforms input bit strings into output strings of the same length Given an input Some of the commonly used ciphers include AES, DES, triple-DES and so on Symmetric cryptography is generally fast and suited well for large chunks of data However, the vulnerability of symmetric In the case of HTTPS, for instance, web browsers use public-key cryptography to check websites’ validity and then establish a symmetric key to encrypt communications There’s little doubt that some of the most important pillars of modern cryptography will tumble spectacularly once quantum computing, now in its infancy, matures sufficiently Some experts say
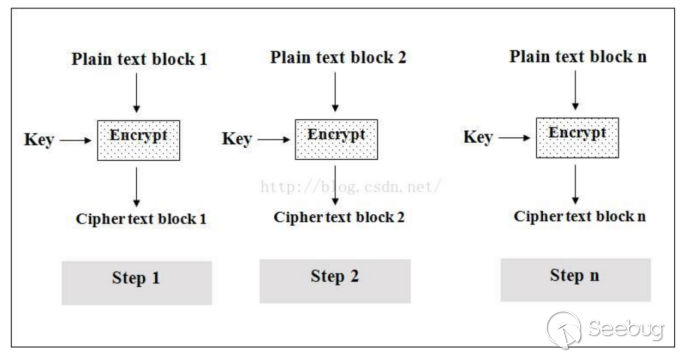
Some Tricks Of Symmetric Cryptography In the case of HTTPS, for instance, web browsers use public-key cryptography to check websites’ validity and then establish a symmetric key to encrypt communications There’s little doubt that some of the most important pillars of modern cryptography will tumble spectacularly once quantum computing, now in its infancy, matures sufficiently Some experts say Classical computers aren't capable of solving the equation in any useful time frame; add some quantum compute power, though, and all of this carefully encoded data could turn into crystal-clear Some of the biggest names in cryptography and computer science just released an open letter condemning the surveillance practices of the US government "Media reports since last June have
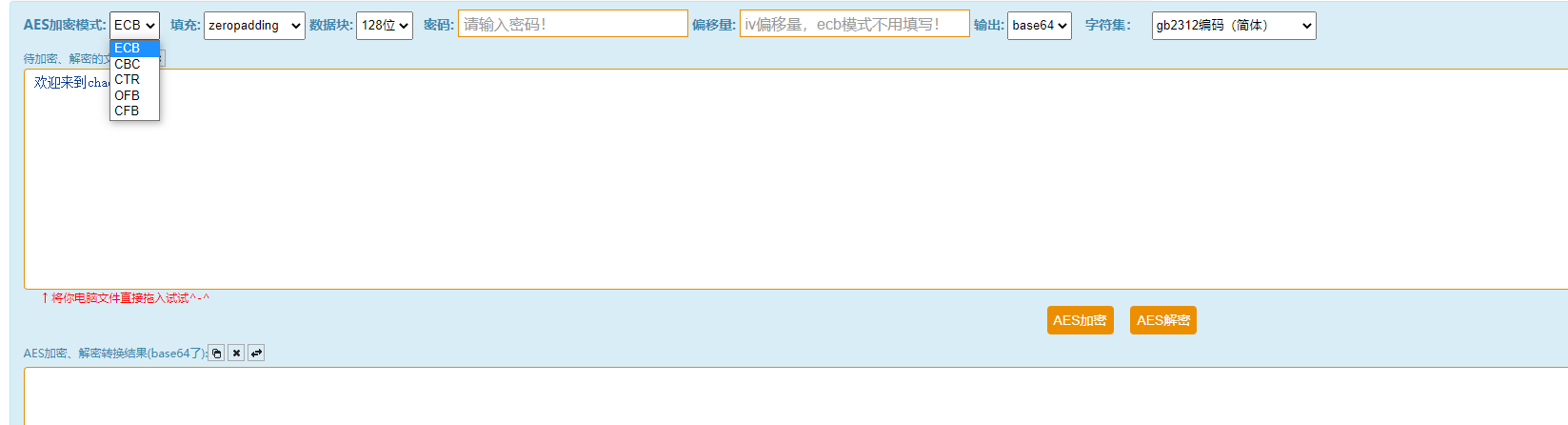
Some Tricks Of Symmetric Cryptography Classical computers aren't capable of solving the equation in any useful time frame; add some quantum compute power, though, and all of this carefully encoded data could turn into crystal-clear Some of the biggest names in cryptography and computer science just released an open letter condemning the surveillance practices of the US government "Media reports since last June have
Some Tricks Of Symmetric Cryptography
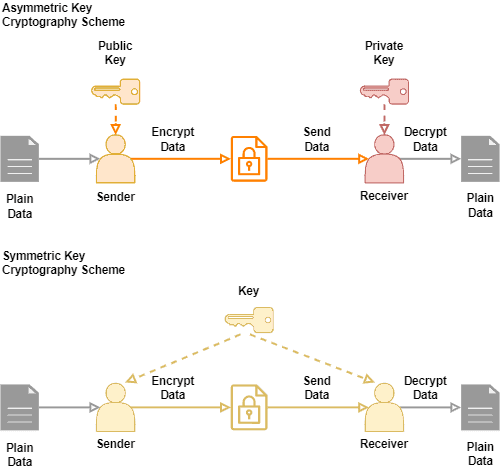
How To Share A Key In Symmetric Cryptography Baeldung On Computer
Comments are closed.