Solved Rsa Encryption And Decryption Algorithm For All Chegg
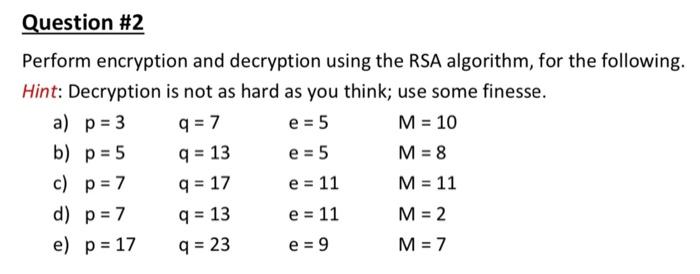
Solved Perform Encryption And Decryption Using The Rsa Chegg Some cryptographers are looking for RSA replacements because the algorithm is just one encryption algorithm that may be vulnerable to new machines that exploit quantum effects in electronics RSA’s demise is greatly exaggerated At the Enigma 2023 Conference in Santa Clara, California, on Tuesday, computer scientist and security and privacy expert Simson Garfinkel assured researchers

Solved Rsa Cryptography Perform Encryption And Decryption Chegg The strength of an RSA encryption relates to the length of the integer — which defines how big the problem is For example, a 50-bit integer has 967 x 10^16 possible values RELATED STORIES • AES (Advanced Encryption Standard): AES is a symmetric encryption algorithm widely used in government and industry It offers key lengths of 128, 192 and 256 bits, providing strong security As if it wasn't enough that the NSA paid RSA $10 million to adopt an algorithm that wasn't entirely secure, researchers have now demonstrated that they can break even RSA 4096 bit encryption with The first public key encryption algorithm: RSA The first algorithms using asymmetric keys were devised in secret by the British government's SIGINT agency, GCHQ, in 1973

Solved In This Question We Will Work With Rsa Encryption Chegg As if it wasn't enough that the NSA paid RSA $10 million to adopt an algorithm that wasn't entirely secure, researchers have now demonstrated that they can break even RSA 4096 bit encryption with The first public key encryption algorithm: RSA The first algorithms using asymmetric keys were devised in secret by the British government's SIGINT agency, GCHQ, in 1973 A 25-year-old vulnerability that enables RSA decryption has been presented at the 28th European Symposium on Research in Computer Security The paper, Everlasting robot: the Marvin attack
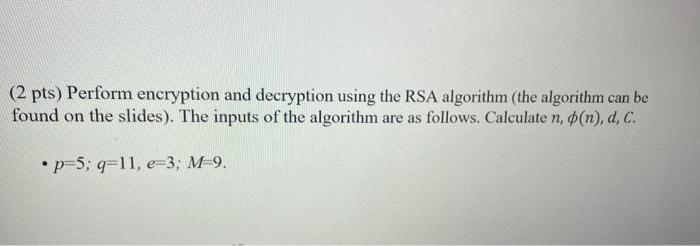
Solved 2 Pts Perform Encryption And Decryption Using The Chegg A 25-year-old vulnerability that enables RSA decryption has been presented at the 28th European Symposium on Research in Computer Security The paper, Everlasting robot: the Marvin attack

Solved The Encryption Algorithm Of Rsa Is Defined As Chegg

Solved Perform Encryption And Decryption Using The Rsa Chegg
Comments are closed.