Solved Question7 I Of 8which Of The Following Is A Secure Chegg
Solved Question Chegg Enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. which of the following is a secure connection with encryption and authentication that encapsulates packets and creates tunnels? here’s the best way to solve it. Study with quizlet and memorize flashcards containing terms like which of the following is the most secure way to store passwords on a website? keep a hash of the password, salted with a randomly selected number that is used only once. encrypt the password with a secret key known only to the website administrator.
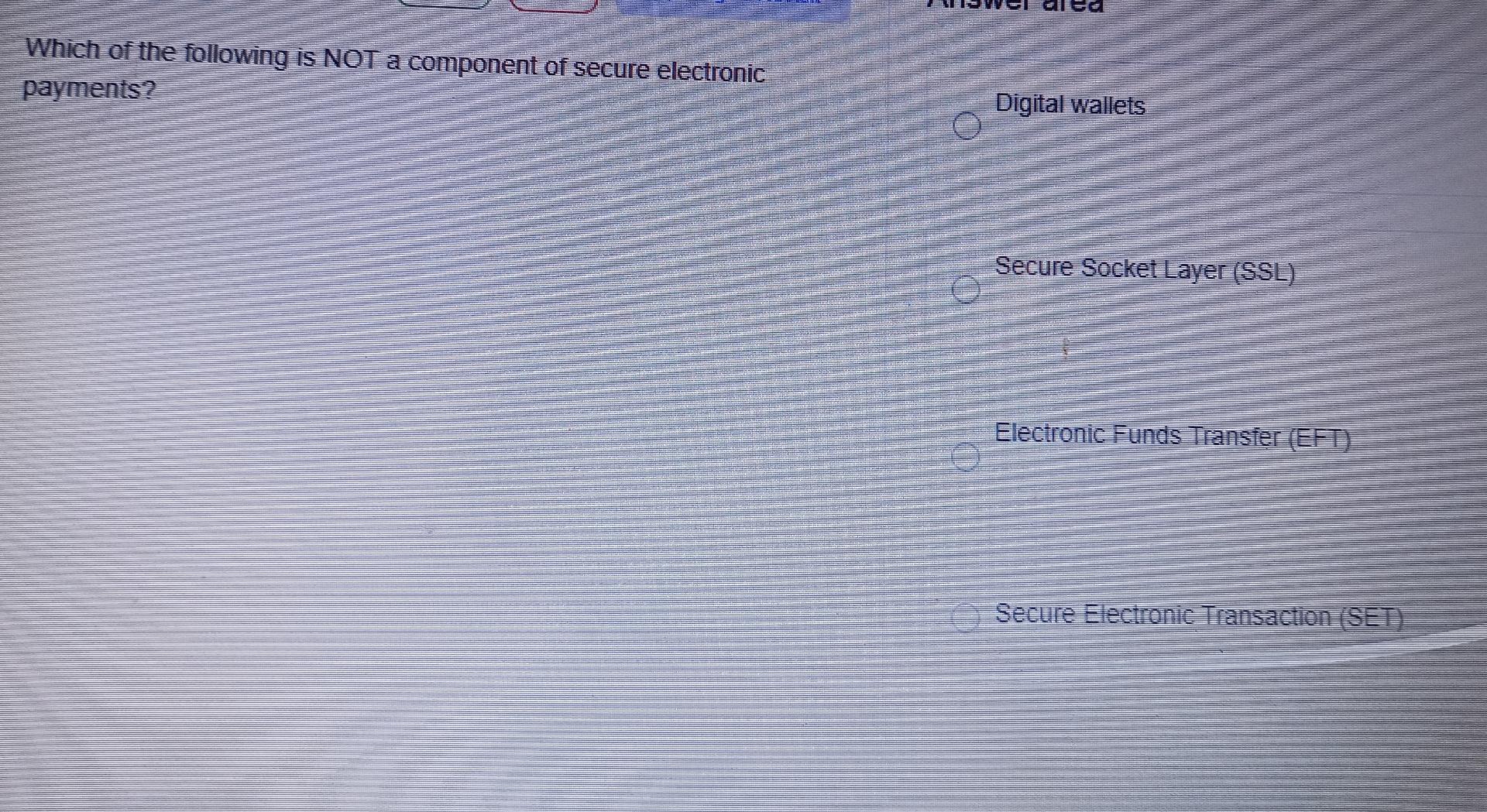
Solved Which Of The Following Is Not A Component Of Secure Chegg Which requirement of secure communications is ensured by the implementation of md5 or sha hash generating algorithms? explanation: integrity is ensured by implementing either md5 or sha hash generating algorithms. many modern networks ensure authentication with protocols, such as hmac. Here’s the best way to solve it. let me analyze each option for password storage secur not the question you’re looking for? post any question and get expert help quickly. Study with quizlet and memorize flashcards containing terms like which of the following most accurately defines encryption?, which of the following is the oldest encryption method discussed in this text?, what is the main problem with simple substitution? and more. Which of the following is the most secure way of storing passwords? question options: password is stored using strong encryption, like aes. password and random salt are run through a slow cryptographic hash algorithm. password is stored in plain text in a secure database.
Solved I Need Help With Question 1 2 The Following Chegg Chegg Study with quizlet and memorize flashcards containing terms like which of the following most accurately defines encryption?, which of the following is the oldest encryption method discussed in this text?, what is the main problem with simple substitution? and more. Which of the following is the most secure way of storing passwords? question options: password is stored using strong encryption, like aes. password and random salt are run through a slow cryptographic hash algorithm. password is stored in plain text in a secure database. Encrypting passwords using a symmetric encryption algorithm is not a secure way to store passwords because symmetric encryption requires the same key to encrypt and decrypt the data, which can be vulnerable if the key is compromised. Which of the following are secure programming guidelines? b . choose the correct option from . through a successful format string attack against a web application, an attacker is able to execute which of . it is a good programming practice to prevent caching of sensitive data at client or proxies, by implementing which of the following?. Engineering computer science computer science questions and answers question8 of 8which of the following statements are true about a generation 2 virtual machine?. Enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. which of the following is a secure coding practice? select the correct option (s) and click submit. here’s the best way to solve it. limit access to your classes, methods, and varia not the question you’re looking for?.
Comments are closed.