Solved Question 3 A Cryptography Involves Two Basic Chegg

Solved Question 3 A Cryptography Involves Two Basic Chegg Question 3 (a) cryptography involves two basic techniques. explain and give examples for each. (b) compare the following four factors between rsa and aes algorithms: number of keys key size protection of keys speed of the algorithm (c) amy and bill want to exchange a symmetric key. Answer cipher text what are the two most basic cryptography functions? answer 1) integrity checks 2) ciphering how can cryptographic functions be implemented?.
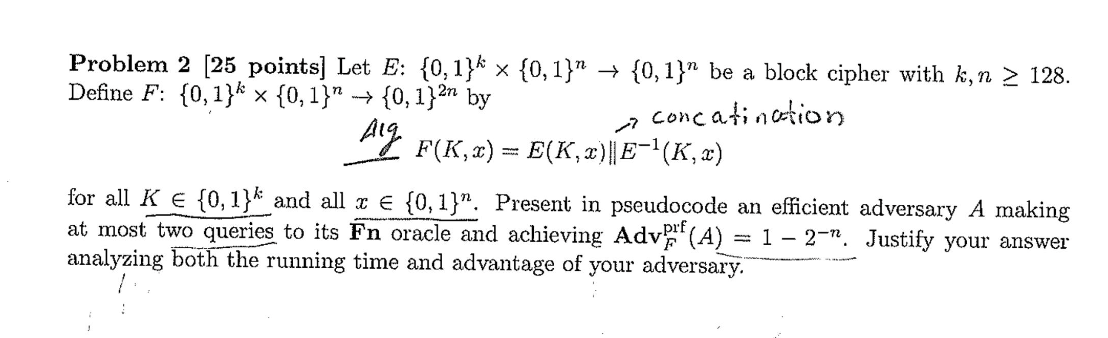
Solved This Is A Cryptography Question Chegg What type of cryptography uses two keys instead of just one, generating both a private and a public key? which of the following is not one of the functions of a digital signature? what cryptographic method, first proposed in the mid 1980s, makes use of sloping curves instead of large prime numbers?. To protect sensitive data and conversations, cryptography uses complex algorithms. these mathematical formulas enable the encryption, decryption, signature, and verification processes that protect secret data during transmission and storage. This article lists 100 cryptography mcqs for engineering students. all the cryptography questions & answers given below include a hint and a link wherever possible to the relevant topic. Computer science expert step 1 cryptography, the art of secure communication, involves several fundamental operations to ensure dat.

Solved Assignment Basic Cryptography I Short Answer Chegg This article lists 100 cryptography mcqs for engineering students. all the cryptography questions & answers given below include a hint and a link wherever possible to the relevant topic. Computer science expert step 1 cryptography, the art of secure communication, involves several fundamental operations to ensure dat. A) a key transport protocol involves the transmission of keys using a secure channel while a key agreement protocol involves the independent generation of a key by multiple parties. 1. cryptography involves the way toward producing and utilizing cyphers to get data. cryptanalysis involves the way toward acquiring the plaintext communication from a ciphertext memo without realizing the solutions used to play out the encryption. Study with quizlet and memorize flashcards containing terms like which of the following terms means a cryptography mechanism that hides secret communications within various forms of data? answer cryptanalysis ciphertext steganography algorithm, which of the following algorithms are used in asymmetric encryption?. Enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. question: cryptography involves two basic techniques, namely select one: a. replacing and addition. b. replacing and shuffling. c. shuffling and the mean. d. addition and subtraction.
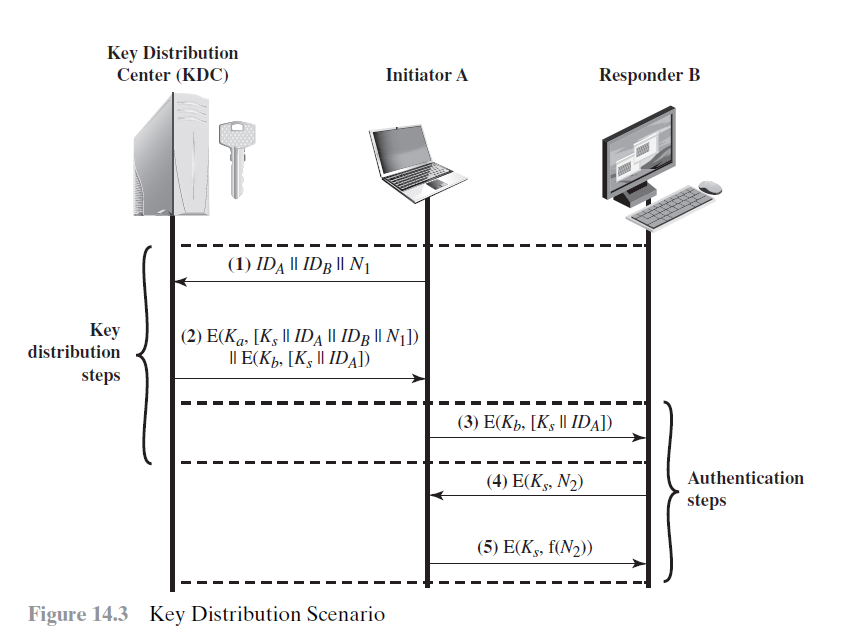
Solved This Question Is From Applied Cryptography Chegg A) a key transport protocol involves the transmission of keys using a secure channel while a key agreement protocol involves the independent generation of a key by multiple parties. 1. cryptography involves the way toward producing and utilizing cyphers to get data. cryptanalysis involves the way toward acquiring the plaintext communication from a ciphertext memo without realizing the solutions used to play out the encryption. Study with quizlet and memorize flashcards containing terms like which of the following terms means a cryptography mechanism that hides secret communications within various forms of data? answer cryptanalysis ciphertext steganography algorithm, which of the following algorithms are used in asymmetric encryption?. Enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. question: cryptography involves two basic techniques, namely select one: a. replacing and addition. b. replacing and shuffling. c. shuffling and the mean. d. addition and subtraction.
Comments are closed.