Solved Public Key Cryptography Isasymmetricsymmetricbit Chegg

Lecture 4 Asymmetric Key Cryptography Part I Pdf Answer to public key cryptography isasymmetricsymmetricbityour solution’s ready to go! enhanced with ai, our expert help has broken down your problem into an easy to learn solution you can count on. see answer. Public key cryptography utilizes asymmetric encryp not the question you’re looking for? post any question and get expert help quickly.
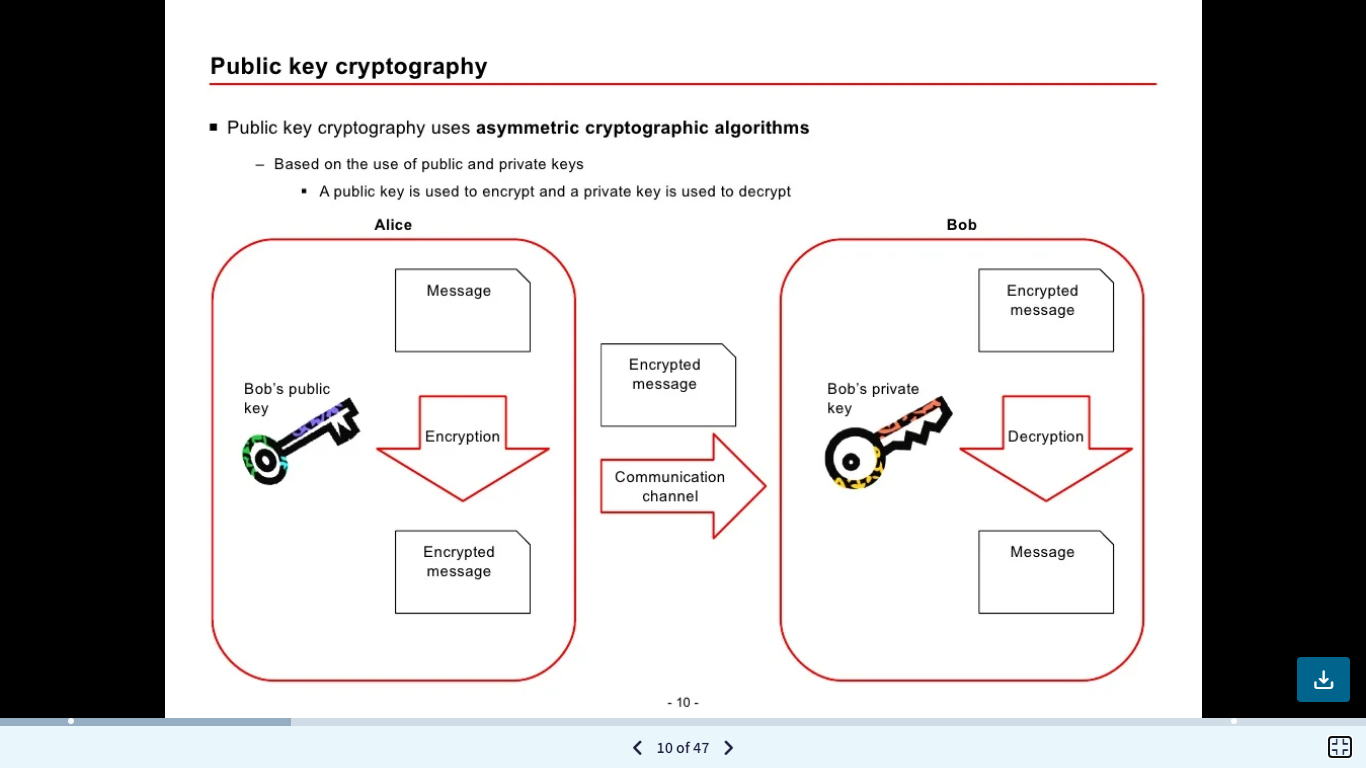
Solved Public Key Cryptography Public Key Cryptography Chegg Engineering computer science computer science questions and answers question 5 ( 0.5 points)public key cryptography is a cryptosystemsymmetricasymmetricsymmetric & asymmetric bothnone of these. Rsa (rivest shamir adleman) algorithm is used for public key cryptography, enabling secure data tran. Your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on. see answer question: public key cryptography • public key cryptography uses asymmetric cryptographic algorithms based on the use of public and private keys . There are 2 steps to solve this one. start by explaining that public key cryptography, also known as asymmetric cryptography, is a cryptographic system that uses two mathematically related keys for encryption and decryption. as per the chegg rules i answered the questions and explanation also public key cryptography:.
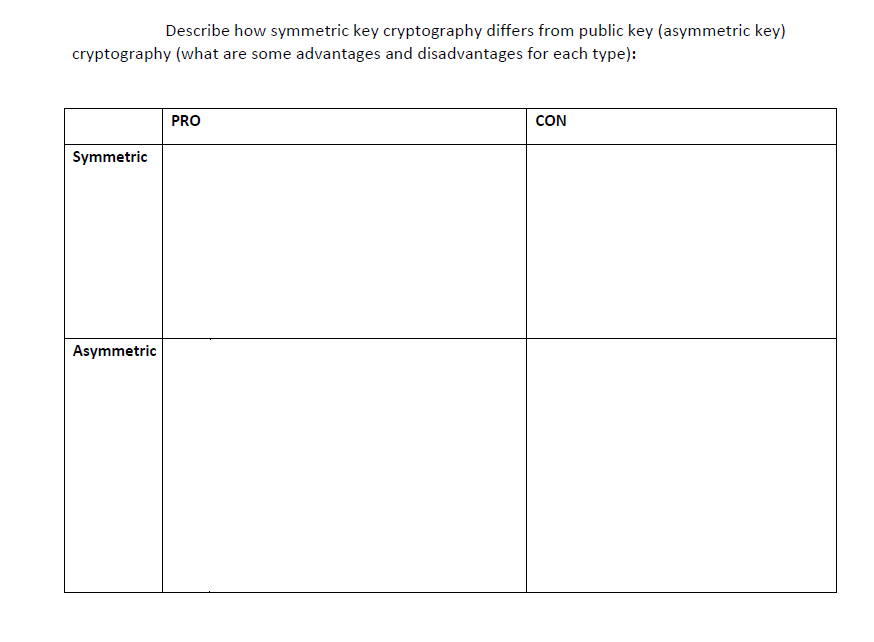
Solved Describe How Symmetric Key Cryptography Differs From Chegg Your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on. see answer question: public key cryptography • public key cryptography uses asymmetric cryptographic algorithms based on the use of public and private keys . There are 2 steps to solve this one. start by explaining that public key cryptography, also known as asymmetric cryptography, is a cryptographic system that uses two mathematically related keys for encryption and decryption. as per the chegg rules i answered the questions and explanation also public key cryptography:. Public key encryption, also known as asymmetric key encryption, uses a key forencryption and a different key for decryption (therefore the name “asymmetric”). an individual (person a) using public key encryption first needs to create a pair of keys, e (for encryption) and d (for decryption), using an algorithm such as the rsa algorithm. the 2. Integrity and authentication approach using symmetric key cryptography – integrity via macs (which use a shared secret key k) – authentication arises due to confidence that only alice & bob have k approach using public key cryptography – digital signatures provide both integrity & authentication together key building block. Symmetric encryption uses different keys for encryption and decryption, while asymmetric encryption uses the same key for both. symmetric encryption uses a public key to encrypt data, while asymmetric encryption uses a private key. Asymmetric hands on cryptography cryptography is the process of writing or reading secret messages or codes. – merriam webster midway story basic terminology plaintext message the original message to encrypt.

Solved Cryptography Is That Symmetric Key Cryptography Uses Chegg Public key encryption, also known as asymmetric key encryption, uses a key forencryption and a different key for decryption (therefore the name “asymmetric”). an individual (person a) using public key encryption first needs to create a pair of keys, e (for encryption) and d (for decryption), using an algorithm such as the rsa algorithm. the 2. Integrity and authentication approach using symmetric key cryptography – integrity via macs (which use a shared secret key k) – authentication arises due to confidence that only alice & bob have k approach using public key cryptography – digital signatures provide both integrity & authentication together key building block. Symmetric encryption uses different keys for encryption and decryption, while asymmetric encryption uses the same key for both. symmetric encryption uses a public key to encrypt data, while asymmetric encryption uses a private key. Asymmetric hands on cryptography cryptography is the process of writing or reading secret messages or codes. – merriam webster midway story basic terminology plaintext message the original message to encrypt.

Solved Question 1 The Asymmetric Key Cryptography It Also Chegg Symmetric encryption uses different keys for encryption and decryption, while asymmetric encryption uses the same key for both. symmetric encryption uses a public key to encrypt data, while asymmetric encryption uses a private key. Asymmetric hands on cryptography cryptography is the process of writing or reading secret messages or codes. – merriam webster midway story basic terminology plaintext message the original message to encrypt.
Comments are closed.