Solved Program A Program That Performs The Encryption And Chegg

Solved Program A Program That Performs The Encryption And Chegg Question: program a program that performs the encryption and decryption process using the caesar cipher algorithm, with the addition of the letter order based on the user's input (with compensation). in java. After reading through the source code for the program, alice discovered that it does so by calling srand to seed the pseudorandom num ber generator with a combination of the current time and process id, then repeatedly calling rand to generate the bytes of the key.

Solved Program A Program That Performs The Encryption And Chegg The server will encrypt the file using caesar cipher and send it back to the client using the same tcp socket. your task will be to write the two programs – one program corresponding to the server process and another program corresponding to the client process. Write a program that performs text encryption and decryption on a certain input string. first, ask the user to input a string. then, ask the user for an encryption parameter, between 1 and 30. write a separate class named "encryptionhelper". this class has a static function called "encrypt". Your task is to perform and document encryption of data at rest and of an image using gnupg or veracrypto for the data and steghide for the image. True or false? an encryption application program, from a user's point of view, protects a file with a memorized password.

Solved Write A Program That Performs Text Encryption And Chegg Your task is to perform and document encryption of data at rest and of an image using gnupg or veracrypto for the data and steghide for the image. True or false? an encryption application program, from a user's point of view, protects a file with a memorized password. Your job is to write a program that performs different types of encryption or description. first, you need to ask the user to see if the user wants to do encryption or decryption. if the user wants to do encryption, you should find out if the user wants to use “rot” method or cryptogram method. A university assignment from a computer science course focused on cryptography. the assignment includes various exercises on topics such as rsa encryption and decryption, gcd calculation, and diffie hellman key exchange. students are expected to solve true or false questions, perform calculations, and apply concepts from the textbooks 'singh' and 'stinson'. typology: assignments pre 2010. Engineering computer science computer science questions and answers 10 29 using compare instructions, write a program to perform the following:turn on pl1 (o:20) if the value of input word i:1 is 50.turn on pl2 (o:21) if the value of input word i:1 is 56 .> turn on pl3 (o:22) if the value of input word i:1 is not equal to 176.turn on pl4 (o:23) if the value of. Write a java, c# or c c program (the choice is yours) for file directory processing according to the following rules. the program requested for this project must have a text menu like this: 0 – exit 1 – select directory 2 – list directory content (first level) 3 – list directory content (all levels) 4 – delete file 5 – display file (hexadecimal view) 6 – encrypt file (xor with.
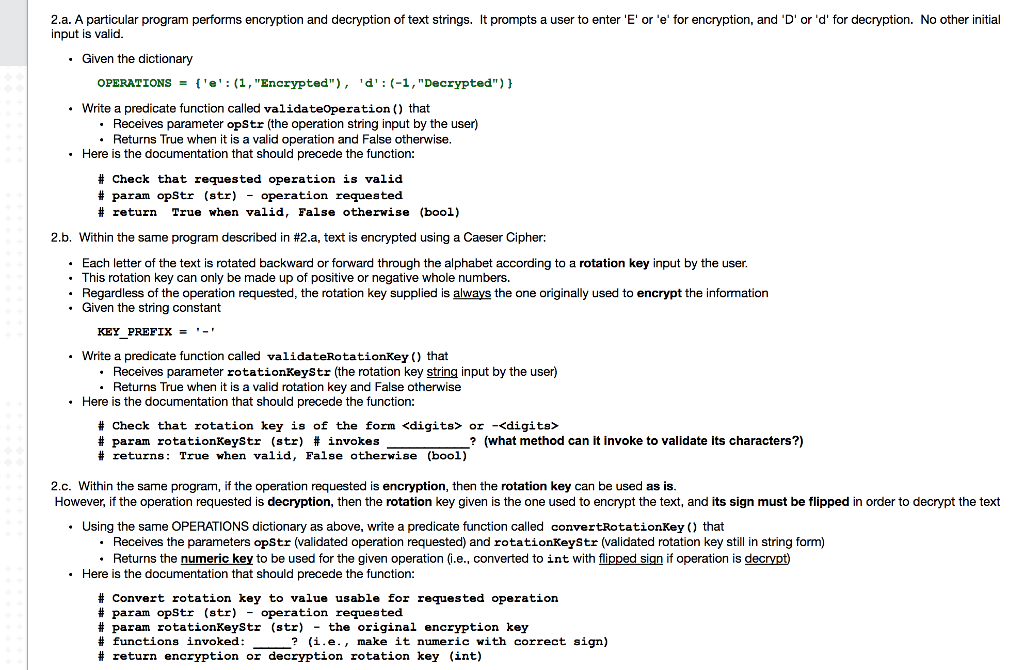
Solved 2 A A Particular Program Performs Encryption And Chegg Your job is to write a program that performs different types of encryption or description. first, you need to ask the user to see if the user wants to do encryption or decryption. if the user wants to do encryption, you should find out if the user wants to use “rot” method or cryptogram method. A university assignment from a computer science course focused on cryptography. the assignment includes various exercises on topics such as rsa encryption and decryption, gcd calculation, and diffie hellman key exchange. students are expected to solve true or false questions, perform calculations, and apply concepts from the textbooks 'singh' and 'stinson'. typology: assignments pre 2010. Engineering computer science computer science questions and answers 10 29 using compare instructions, write a program to perform the following:turn on pl1 (o:20) if the value of input word i:1 is 50.turn on pl2 (o:21) if the value of input word i:1 is 56 .> turn on pl3 (o:22) if the value of input word i:1 is not equal to 176.turn on pl4 (o:23) if the value of. Write a java, c# or c c program (the choice is yours) for file directory processing according to the following rules. the program requested for this project must have a text menu like this: 0 – exit 1 – select directory 2 – list directory content (first level) 3 – list directory content (all levels) 4 – delete file 5 – display file (hexadecimal view) 6 – encrypt file (xor with.

Solved In This Assignment You Will Write A Program That Chegg Engineering computer science computer science questions and answers 10 29 using compare instructions, write a program to perform the following:turn on pl1 (o:20) if the value of input word i:1 is 50.turn on pl2 (o:21) if the value of input word i:1 is 56 .> turn on pl3 (o:22) if the value of input word i:1 is not equal to 176.turn on pl4 (o:23) if the value of. Write a java, c# or c c program (the choice is yours) for file directory processing according to the following rules. the program requested for this project must have a text menu like this: 0 – exit 1 – select directory 2 – list directory content (first level) 3 – list directory content (all levels) 4 – delete file 5 – display file (hexadecimal view) 6 – encrypt file (xor with.
Comments are closed.