Solved Of The Encryption Algorithms Provided By Net Which Chegg

Solved Of The Encryption Algorithms Provided By Net Which Chegg The advent of public key encryption in the 1970s was a major breakthrough because it allowed parties who had never met to securely trade encrypted material that couldn’t be broken by an adversary A VPN can utilize different algorithms provided by the manufacturer to ensure secure communications by guaranteeing that only the appropriate recipient of the data can read it Another method allies
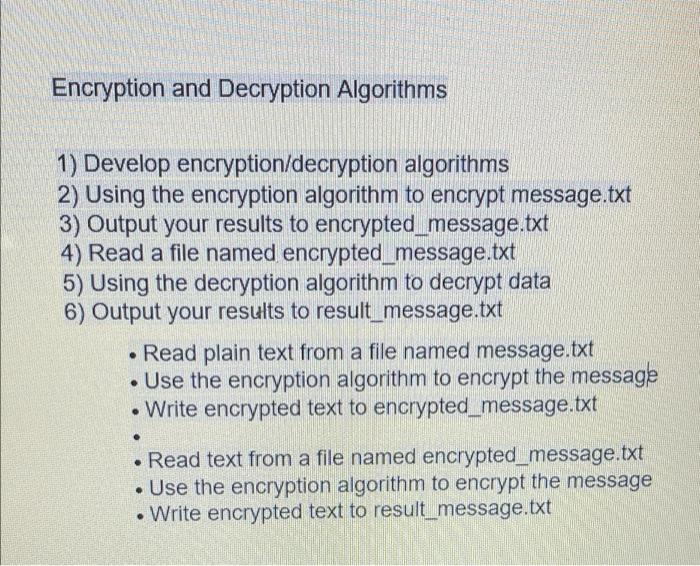
Solved Encryption And Decryption Algorithms 1 Develop Chegg Joyce’s comments raised some eyebrows in the cybersecurity community, given that a back door would benefit the NSA’s work to monitor communications of terrorism suspects and other targets This is now the critical time to become quantum safe, Osborne says, as quantum computers will likely become a danger to current encryption methods between 2030 and 2040, meaning we have around 5
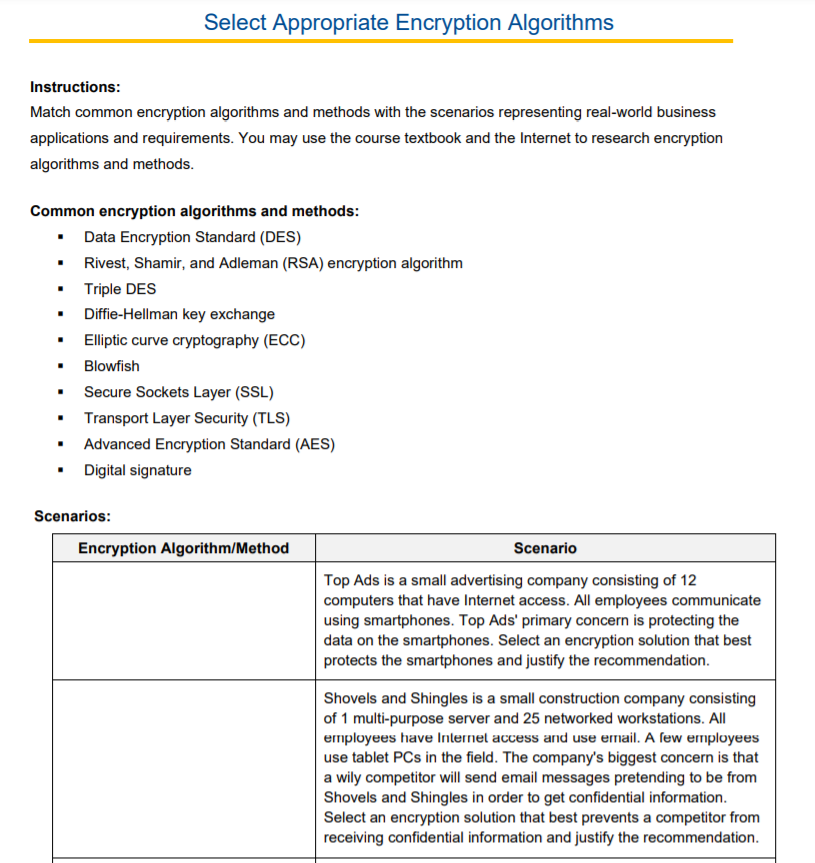
Select Appropriate Encryption Algorithms Chegg
Comments are closed.