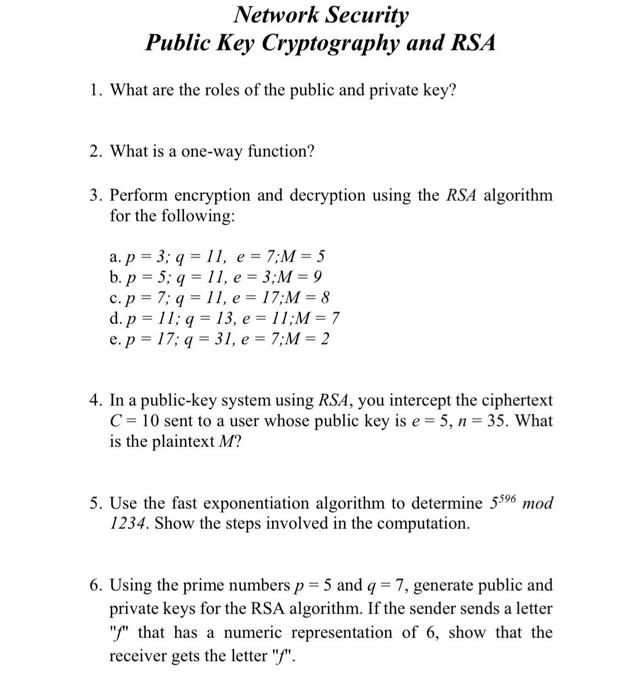
Solved Network Security Public Key Cryptography And Rsa 1 Chegg
Solved Network Security Public Key Cryptography And Rsa 1 Chegg What does public key cryptography actually mean? Find out inside PCMag's comprehensive tech and computer-related encyclopedia Description Basic concepts and techniques of computer network security; data encryption algorithms; public-key cryptography and key management; data authentication; network security protocols in

Network Security 1 0 Modules 15 17 Cryptography Group Exam Answers Asymmetric (public-key) encryption: Distributing a single key for all users in a network can be difficult, which led to the more recent creation of asymmetric (or public-key) cryptography How Public Key Cryptography Really Works, Using Only Simple Math The security system that underlies the internet makes use of a curious fact: You can broadcast part of your encryption to make your Next: The OSI Security Architecture Cryptography and Network Security: Principles and Practice, 6th Edition, by William Stallings, published March 6, 2013 by Prentice Hall, Part of the Pearson Custom Unfortunately, RSA and other public-key algorithms are extremely slow, requiring hardware assistance on many platforms—not just small embedded systems However, these algorithms are essential to

Solved 1 In Rsa Cryptography If The Public Key 25 551 Chegg Next: The OSI Security Architecture Cryptography and Network Security: Principles and Practice, 6th Edition, by William Stallings, published March 6, 2013 by Prentice Hall, Part of the Pearson Custom Unfortunately, RSA and other public-key algorithms are extremely slow, requiring hardware assistance on many platforms—not just small embedded systems However, these algorithms are essential to NIST standards for quantum-safe encryption are due out this summer As quantum computing advances, enterprises need to consider their encryption infrastructure and post-quantum security strategies An astonishing four out of every 1,000 public keys protecting webmail, online banking, and other sensitive online services provide no cryptographic security, a team of mathematicians has found Performing these tasks requires a quantum computer, which have the immense computing power to encrypt and decrypt data A quantum computer could quickly crack current public-key cryptography
Comments are closed.