Solved Lab Applying Encryption And Hashing Algorithms For Chegg
Solved Lab Applying Encryption And Hashing Algorithms For Chegg Our expert help has broken down your problem into an easy to learn solution you can count on. question: lab: applying encryption and hashing algorithms for secure communications upon completion of the lab, you are required to provide a lab report and other deliverables to your instructor. When a hashing algorithm is applied to data, a unique one way (non reversible) hash value, or checksum, is created. as long as the content within a file does not change, the checksum will calculate the same value every time. if the content of the file changes, the algorithm will produce a different checksum.
Solved Lab Applying Encryption And Hashing Algorithms For Chegg What is the difference between md5sum and sha1sum hashing calculations? which is better and why? the difference between md5sum and sha1sum is that md5: 128 bit 16 byte digest. somewhat faster than sha and sha: 160 bit 20 byte digest. sha1 is more complex than md5sum 6. name the cryptographic algorithms used in this lab. sha1sum, md5sum. Introduction the overall purpose of this lab is to learn how to create files and share them between two people. moreover adding encryption to these files and being able to decrypt them is what this lab was trying to teach its user. section 1: hands on demonstration part 2: create a md5sum and a sha1sum hash string. The paper explores practical applications of encryption and hashing algorithms, specifically focusing on secure communications. it covers the behavior of hash values in relation to file modifications, the significance of consistent hash outcomes for authentication, and alternative security measures like digital signatures to uphold message. In this part, you are tasked with recommending the best encryption and authentication algorithms to implement on the cisco isr 4321using ios xe 17. to do so, you will research various protocols supported by ipsec vpns.

Lecture 9 2024 Searching And Hashing Algorithms Pdf Computing The paper explores practical applications of encryption and hashing algorithms, specifically focusing on secure communications. it covers the behavior of hash values in relation to file modifications, the significance of consistent hash outcomes for authentication, and alternative security measures like digital signatures to uphold message. In this part, you are tasked with recommending the best encryption and authentication algorithms to implement on the cisco isr 4321using ios xe 17. to do so, you will research various protocols supported by ipsec vpns. In this lab, you applied common cryptographic and hashing techniques to ensure message and fi le transfer integrity and maximize confi dentiality. you also created an md5sum and sha1 hash on a sample fi le on the linux virtual machine and compared the hash values of the original fi les with those generated after the fi le had been modifi ed. Our expert help has broken down your problem into an easy to learn solution you can count on. 1. compare the hash values calculated for example.txt that you documented during this lab. explain in your own words why the hash values will change when the data is modified. 2. I will create md5 checksum and sha 1 hashes on simple text files on a linux virtual machine (vm) and compare the hash values of the original files with those generated after the file has been modified. then, i will use gnupg (gnu privacy guard) to generate an encryption key pair and encrypt a message. We will now have a look at a different variety of algorithms in a direct comparison and using hash calc which is a calculator that computes message digests, checksums, and hmacs for files, as well as for text and hex strings.
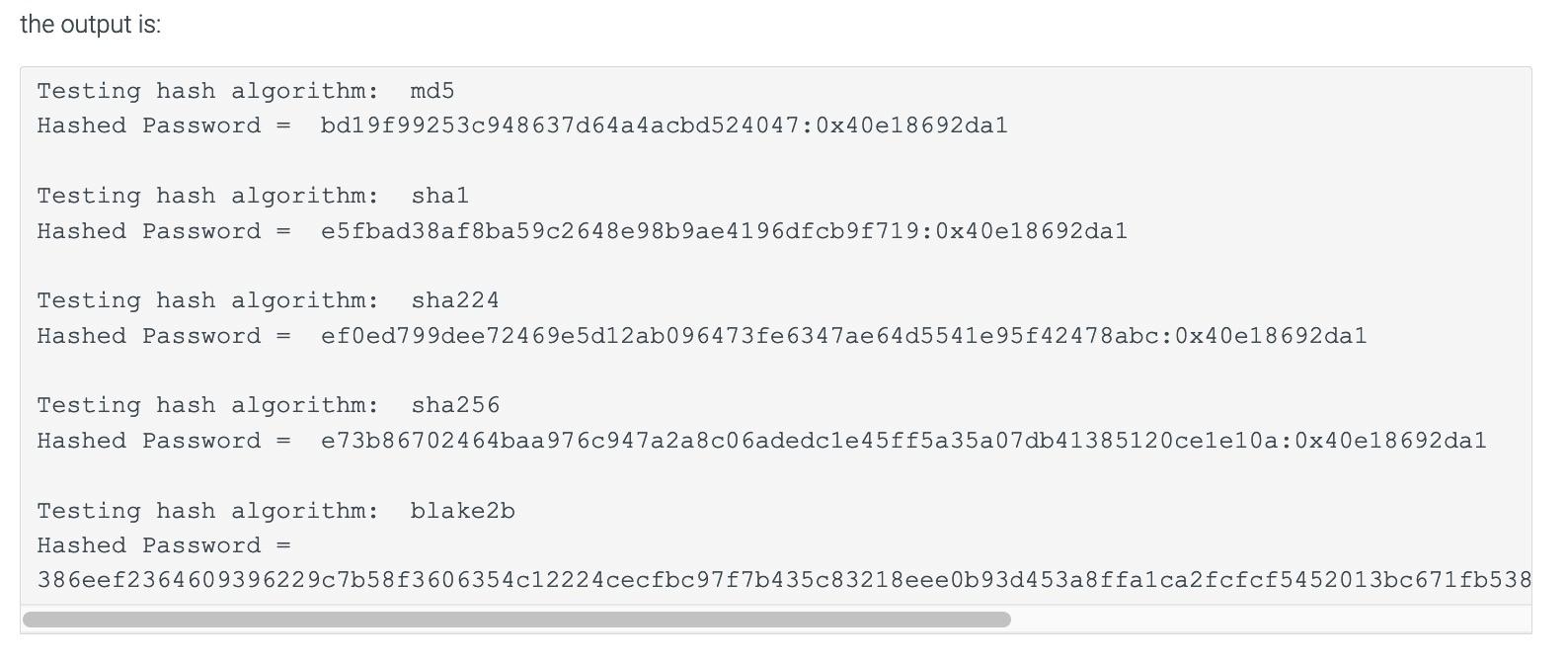
Solved 5 16 Lab Cryptographic Hashing Chegg In this lab, you applied common cryptographic and hashing techniques to ensure message and fi le transfer integrity and maximize confi dentiality. you also created an md5sum and sha1 hash on a sample fi le on the linux virtual machine and compared the hash values of the original fi les with those generated after the fi le had been modifi ed. Our expert help has broken down your problem into an easy to learn solution you can count on. 1. compare the hash values calculated for example.txt that you documented during this lab. explain in your own words why the hash values will change when the data is modified. 2. I will create md5 checksum and sha 1 hashes on simple text files on a linux virtual machine (vm) and compare the hash values of the original files with those generated after the file has been modified. then, i will use gnupg (gnu privacy guard) to generate an encryption key pair and encrypt a message. We will now have a look at a different variety of algorithms in a direct comparison and using hash calc which is a calculator that computes message digests, checksums, and hmacs for files, as well as for text and hex strings.
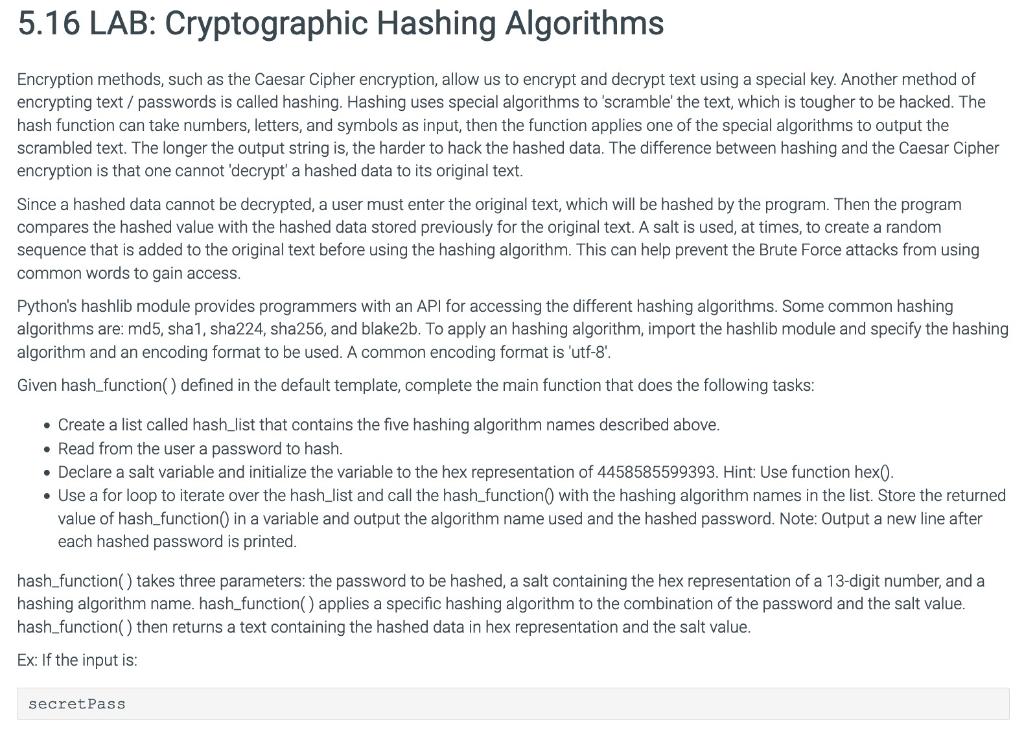
Solved 5 16 Lab Cryptographic Hashing Chegg I will create md5 checksum and sha 1 hashes on simple text files on a linux virtual machine (vm) and compare the hash values of the original files with those generated after the file has been modified. then, i will use gnupg (gnu privacy guard) to generate an encryption key pair and encrypt a message. We will now have a look at a different variety of algorithms in a direct comparison and using hash calc which is a calculator that computes message digests, checksums, and hmacs for files, as well as for text and hex strings.

Doc Lab 2 Applying Encryption And Hashing Algorithms For Secure
Comments are closed.