Solved Cryptography Is That Symmetric Key Cryptography Uses Chegg

Solved Uses Symmetric Key Cryptography To Encrypt And Chegg Cryptography is that symmetric key cryptography uses the same key for encryption and decryption, while public key cryptography uses a pair of keys a public key for encryption and a private key for decryption. Symmetrical key cryptography also known as conventional or single key encryption was the primary method of encryption before the introduction of public key cryptography in the 1970s. in symmetric key algorithms, the same keys are used for data encryption and decryption.

Solved Cryptography Is That Symmetric Key Cryptography Uses Chegg Symmetric key algorithms require both the sender and the recipient of a message to have the same secret key. all early cryptographic systems required either the sender or the recipient to somehow receive a copy of that secret key over a physically secure channel. What is secure encryption? the symmetric key is stored encrypted or in tamperproof hardware. the password is used to unlock the key so the data can be decrypted. “was this the original message that was sent?” “did alice really send this message?” how do you know an encryption scheme is secure against a passive eavesdropper?. Which of the following statements about asymmetric key cryptography is true? a) asymmetric key cryptography uses one shared key. b) asymmetric key cryptography is also called private key cryptography. c) asymmetric key cryptography uses two keys called public keys. d) asymmetric key cryptography is also called public key cryptography. Asymmetric encryption uses two keys—a public key and a private key—to encrypt and decrypt data, whereas symmetric encryption uses one. having two different keys generally makes asymmetric encryption (also known as public key cryptography and public key encryption) more secure and versatile.
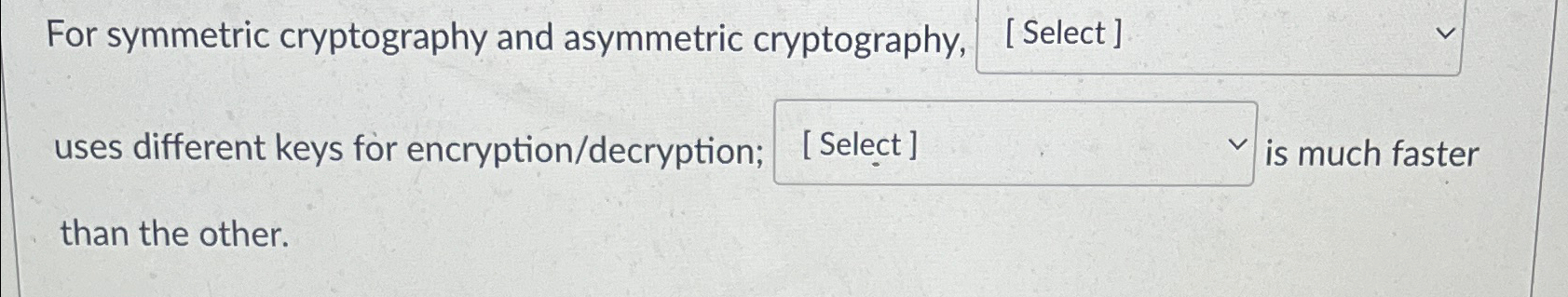
Solved For Symmetric Cryptography And Asymmetric Chegg Which of the following statements about asymmetric key cryptography is true? a) asymmetric key cryptography uses one shared key. b) asymmetric key cryptography is also called private key cryptography. c) asymmetric key cryptography uses two keys called public keys. d) asymmetric key cryptography is also called public key cryptography. Asymmetric encryption uses two keys—a public key and a private key—to encrypt and decrypt data, whereas symmetric encryption uses one. having two different keys generally makes asymmetric encryption (also known as public key cryptography and public key encryption) more secure and versatile. We can leverage this property to build symmetric key encryption schemes where there is no effective way to decrypt any ciphertext, even if it’s the encryption of a message we’ve seen before. Here’s the best way to solve it. in symmetric key cryptography, the same key is used by both the sender and the receiver for encrypti not the question you’re looking for? post any question and get expert help quickly. Approved for use since the 1970s, symmetric key encryption algorithms are just one way to keep confidential data secure. take a look at the different algorithms, from des to aes and their spinoffs, and learn the math behind the crucial cryptography functionality. Bob encrypts a message using a key and sends it to alice. alice decrypts the message using the same key. which of the following types of encryption keys is being used? a. asymmetric b. digital signature c. symmetric d. block cipher b. uses a 168 bit key.
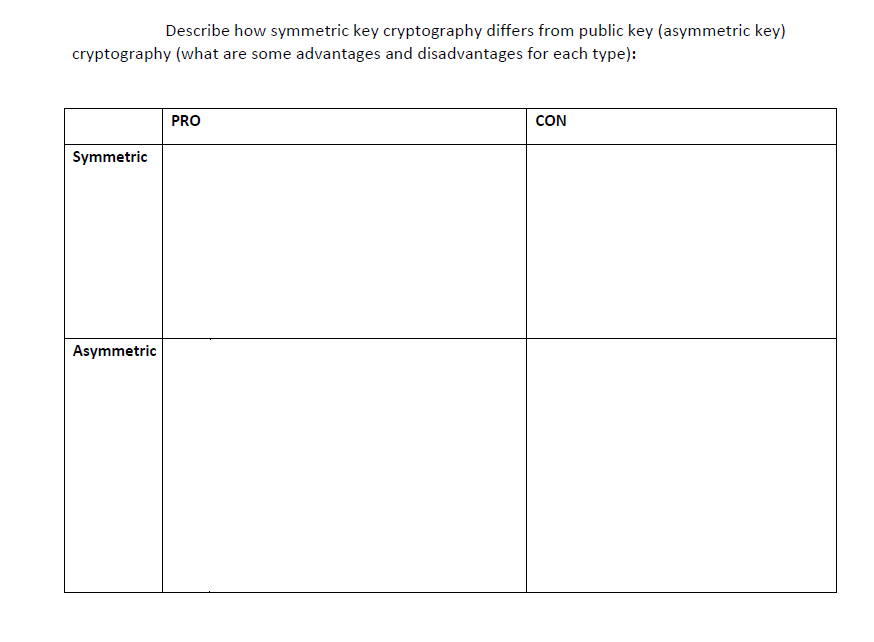
Solved Describe How Symmetric Key Cryptography Differs From Chegg We can leverage this property to build symmetric key encryption schemes where there is no effective way to decrypt any ciphertext, even if it’s the encryption of a message we’ve seen before. Here’s the best way to solve it. in symmetric key cryptography, the same key is used by both the sender and the receiver for encrypti not the question you’re looking for? post any question and get expert help quickly. Approved for use since the 1970s, symmetric key encryption algorithms are just one way to keep confidential data secure. take a look at the different algorithms, from des to aes and their spinoffs, and learn the math behind the crucial cryptography functionality. Bob encrypts a message using a key and sends it to alice. alice decrypts the message using the same key. which of the following types of encryption keys is being used? a. asymmetric b. digital signature c. symmetric d. block cipher b. uses a 168 bit key.

Symmetric Key Cryptography Is More Efficient Than Chegg Approved for use since the 1970s, symmetric key encryption algorithms are just one way to keep confidential data secure. take a look at the different algorithms, from des to aes and their spinoffs, and learn the math behind the crucial cryptography functionality. Bob encrypts a message using a key and sends it to alice. alice decrypts the message using the same key. which of the following types of encryption keys is being used? a. asymmetric b. digital signature c. symmetric d. block cipher b. uses a 168 bit key.

Solved Symmetric Or Private Key Cryptography Uses O A Chegg
Comments are closed.