Solved Cryptography Is Often Used For Long Messages Chegg
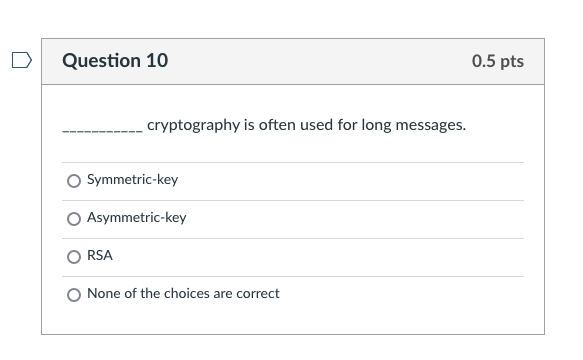
Solved Cryptography Is Often Used For Long Messages Chegg There are 3 steps to solve this one. cryptography: cryptography is the process of hiding or coding informat cryptography is often used for long messages. symmetric key asymmetric key rsa none of the choices are correct. not the question you’re looking for? post any question and get expert help quickly. Symmetric key cryptography is typically used for long messages because it is faster and more efficient due to the use of a single secret key for both encryption and decryption. this method supports the quick processing of large amounts of data.

Solved Cryptography Chegg Cryptography is often used for long messages. cryptography is often used for short messages. means that the sender and the receiver expect confidentiality. means that the data must arrive at the receiver exactly as they were sent. Cryptography is often used for long messages. a) symmetric key b) asymmetric key c) public key d) open key correct answer: verified show answer view this answer and more for free by performing one of the following actions. In cryptography, the same key is used in both directions. a packet filter firewall filters at the or layer. in cryptography, everyone has access to everyone’s public key. was invented by phil zimmermann to provide all four aspects of security in the sending of email. I have read about long message attacks on some cryptographic hash functions. however, i don't quite understand what is being referred to as a "long message". also, do long message attacks only apply for such "long" messages or can they also be used (any exceptions?) with "normal" messages? ("normal" as opposed to "long", i mean) thank you.
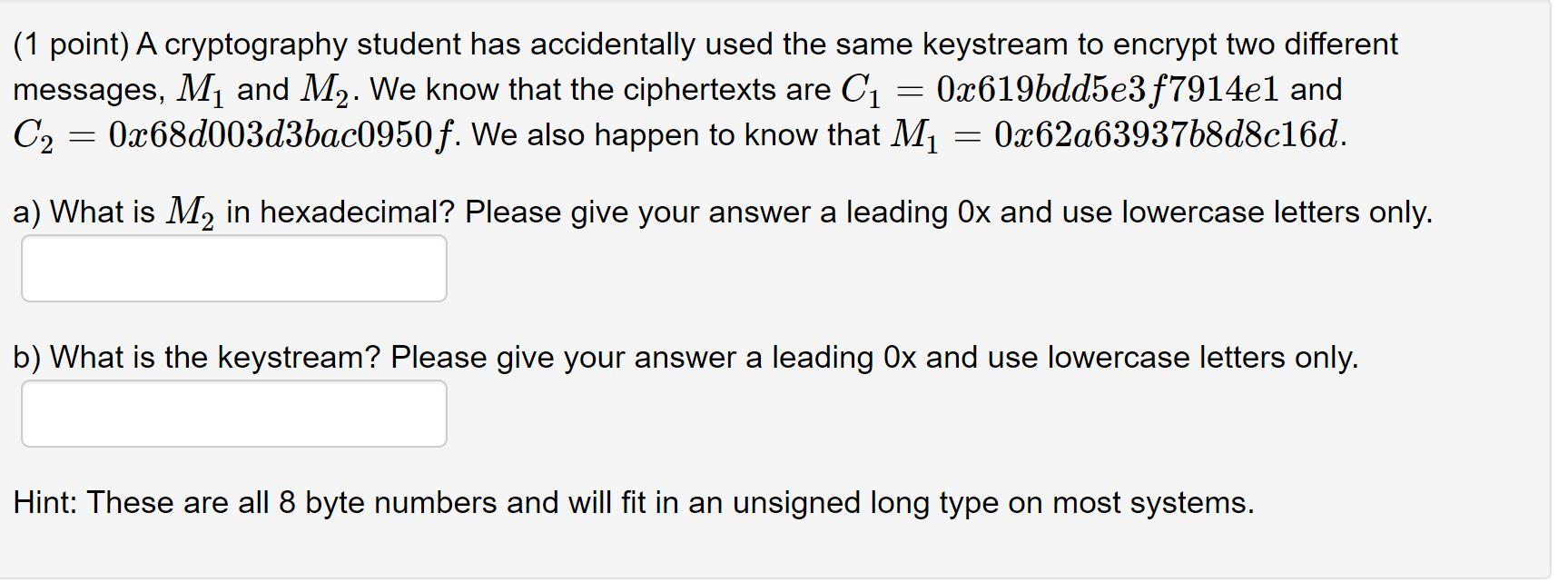
Solved 1 Point A Cryptography Student Has Accidentally Chegg In cryptography, the same key is used in both directions. a packet filter firewall filters at the or layer. in cryptography, everyone has access to everyone’s public key. was invented by phil zimmermann to provide all four aspects of security in the sending of email. I have read about long message attacks on some cryptographic hash functions. however, i don't quite understand what is being referred to as a "long message". also, do long message attacks only apply for such "long" messages or can they also be used (any exceptions?) with "normal" messages? ("normal" as opposed to "long", i mean) thank you. In asymmetric algorithm that use different keys for encryption and decryptio …. In cryptography, the same key is used in both directions. we have an expert written solution to this problem! cryptography is often used for long messages. a. symmetric key. b. asymmetric key. d. open key. cryptography is often used for short messages. a. symmetric key. b. asymmetric key. d. open key. The strength of a cryptosystem lies not only in long keys but in the algorithm, initialization vector or method, the proper use of the keyspace, and the protection and management of keys. Pgp is an encryption technique used to encrypt and decrypt these types of communications. in this slp assignment, you will learn how pgp works and how it can be used to protect. your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on.
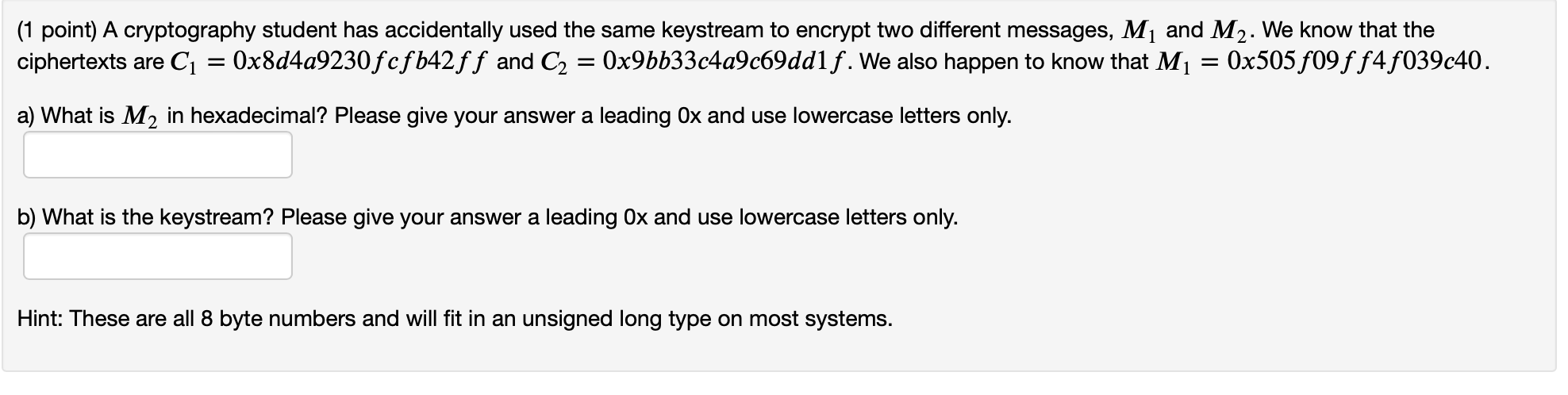
Solved 1 Point A Cryptography Student Has Accidentally Chegg In asymmetric algorithm that use different keys for encryption and decryptio …. In cryptography, the same key is used in both directions. we have an expert written solution to this problem! cryptography is often used for long messages. a. symmetric key. b. asymmetric key. d. open key. cryptography is often used for short messages. a. symmetric key. b. asymmetric key. d. open key. The strength of a cryptosystem lies not only in long keys but in the algorithm, initialization vector or method, the proper use of the keyspace, and the protection and management of keys. Pgp is an encryption technique used to encrypt and decrypt these types of communications. in this slp assignment, you will learn how pgp works and how it can be used to protect. your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on.
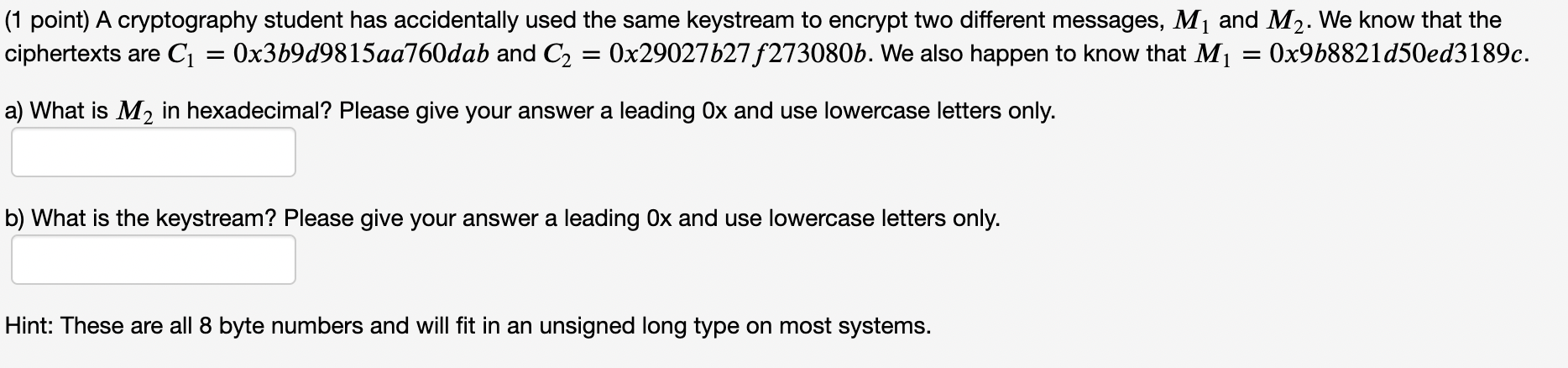
Solved 1 Point A Cryptography Student Has Accidentally Chegg The strength of a cryptosystem lies not only in long keys but in the algorithm, initialization vector or method, the proper use of the keyspace, and the protection and management of keys. Pgp is an encryption technique used to encrypt and decrypt these types of communications. in this slp assignment, you will learn how pgp works and how it can be used to protect. your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on.
Comments are closed.