Solved Consider A One Way Authentication Technique Based On Chegg
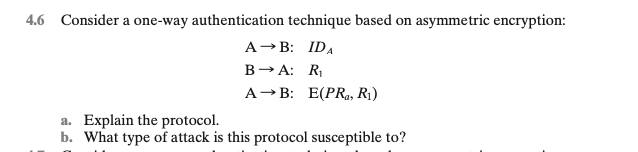
Solved 6 Consider A One Way Authentication Technique Based Chegg Consider a one way authentication technique based on asymmetric encryption: a. a → b: ida b → a: r1 a → b: e (pra, r1) b. a → b: ida b → a: e (pua, r2) a → b: r2 ida = a’s id r1 and r2 = a random number pra = a’s private key pua = a’s public key explain each protocol (a and b) and what type of attack each protocol is. The one way authentication protocol described uses asymmetric encryption and follows a three step process for validating the identity of a user. here’s how it works: step 1: entity a sends its identity (id a) to entity b. this initial step establishes the intent of a to authenticate itself to b.

Consider A One Way Authentication Technique Based On Chegg The text of x.509 states that checking timestamps ta and tb is optional for three way authentication. but consider the following example: suppose a and b have used the preceding protocol on some previous occasion, and that opponent c has intercepted the preceding three messages. Enhanced document preview: cse 565 computer security solution key for midterm 3 question 1: (5 2 2 2 4 points) (certificates and kerberos) a) consider a one way authentication technique based on asymmetric encryption where the symbols have their usual meaning (e.g., n1 is a nonce): a > b: ida b > a: e (pua, n1) a > b: n1 explain the. Our expert help has broken down your problem into an easy to learn solution you can count on. question: consider a one way authentication technique based on asymmetric encryption: a > b: ida b > a: r1 a > b: e (pra, r1) a. explain the protocol. b. what type of attack is this protocol susceptible to? a. explain the protocol. b. A. explain the protocol. b. what type of attack is this protocol susceptible to?.
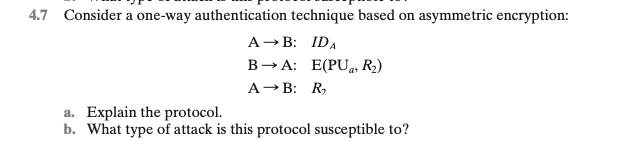
Solved 7 Consider A One Way Authentication Technique Based Chegg Our expert help has broken down your problem into an easy to learn solution you can count on. question: consider a one way authentication technique based on asymmetric encryption: a > b: ida b > a: r1 a > b: e (pra, r1) a. explain the protocol. b. what type of attack is this protocol susceptible to? a. explain the protocol. b. A. explain the protocol. b. what type of attack is this protocol susceptible to?. 1. consider a one way authentication technique based on asymmetric encryption: a s b: id a b s a: r 1 a s b: e (pr a , r 1 ) a. explain the protocol. b. what type of attack is this protocol susceptible to? 2. consider a one way authentication. Actually, this is become an issue i f a uses its public or private key both for authentication and signatures. reference: xia, h., zhang, s. s., li, y., pan, z. k., peng, x., & cheng, x. z. (2019). an attack resistant trust inference model for securing routing in vehicular ad hoc networks. ieee transactions on vehicular technology, 68 (7), 7108. A → b: a sends its identifier (id a) to b to start the authentication process. b → a: b responds by sending a random number (r1) to a. this randomness acts as a nonce that ensures freshness in the authentication process. For a mac based scheme, alice would have to establish a shared key with each potential recipient. with digital signatures, she uses the same digital signature for each recipient; the digital signature is created by signing the hash of the message with her private key.

Solved Consider A One Way Authentication Technique Based On Chegg 1. consider a one way authentication technique based on asymmetric encryption: a s b: id a b s a: r 1 a s b: e (pr a , r 1 ) a. explain the protocol. b. what type of attack is this protocol susceptible to? 2. consider a one way authentication. Actually, this is become an issue i f a uses its public or private key both for authentication and signatures. reference: xia, h., zhang, s. s., li, y., pan, z. k., peng, x., & cheng, x. z. (2019). an attack resistant trust inference model for securing routing in vehicular ad hoc networks. ieee transactions on vehicular technology, 68 (7), 7108. A → b: a sends its identifier (id a) to b to start the authentication process. b → a: b responds by sending a random number (r1) to a. this randomness acts as a nonce that ensures freshness in the authentication process. For a mac based scheme, alice would have to establish a shared key with each potential recipient. with digital signatures, she uses the same digital signature for each recipient; the digital signature is created by signing the hash of the message with her private key.

Solved Consider A One Way Authentication Technique Based On Chegg A → b: a sends its identifier (id a) to b to start the authentication process. b → a: b responds by sending a random number (r1) to a. this randomness acts as a nonce that ensures freshness in the authentication process. For a mac based scheme, alice would have to establish a shared key with each potential recipient. with digital signatures, she uses the same digital signature for each recipient; the digital signature is created by signing the hash of the message with her private key.
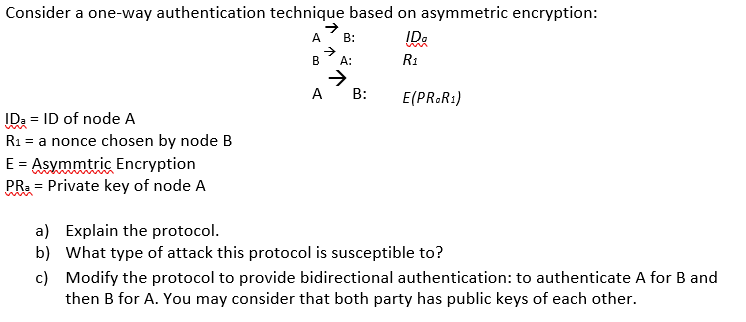
Solved Consider A One Way Authentication Technique Based On Chegg
Comments are closed.