Solved 6 Consider A One Way Authentication Technique Based Chegg
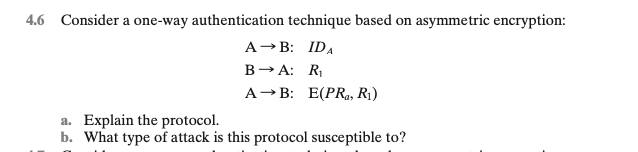
Solved 6 Consider A One Way Authentication Technique Based Chegg Question: 6 consider a one way authentication technique based on asymmetric encryption: a→b: b→a: a→b:idar1e (pra,r1) a. explain the protocol. b. what type of attack is this protocol susceptible to? show transcribed image text. The text of x.509 states that checking timestamps ta and tb is optional for three way authentication. but consider the following example: suppose a and b have used the preceding protocol on some previous occasion, and that opponent c has intercepted the preceding three messages.

Consider A One Way Authentication Technique Based On Chegg The one way authentication protocol described uses asymmetric encryption and follows a three step process for validating the identity of a user. here’s how it works: step 1: entity a sends its identity (id a) to entity b. this initial step establishes the intent of a to authenticate itself to b. Actually, this is become an issue i f a uses its public or private key both for authentication and signatures. reference: xia, h., zhang, s. s., li, y., pan, z. k., peng, x., & cheng, x. z. (2019). an attack resistant trust inference model for securing routing in vehicular ad hoc networks. ieee transactions on vehicular technology, 68 (7), 7108. Answer:a primary amine has the general formula r. nh2; a secondary amine has the general formula r. nh. r', where r and r' are alkyl or aryl groups. a primary a…. A. the protocol is a one way authentication technique based on asymmetric encryption. the goal of the protocol is for party a to authenticate their identity to party b. the protocol proceeds as follows: party a sends their identity (ida) to party b in plain text. party b.
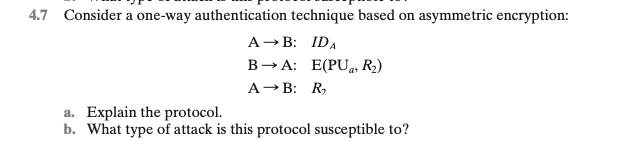
Solved 7 Consider A One Way Authentication Technique Based Chegg Answer:a primary amine has the general formula r. nh2; a secondary amine has the general formula r. nh. r', where r and r' are alkyl or aryl groups. a primary a…. A. the protocol is a one way authentication technique based on asymmetric encryption. the goal of the protocol is for party a to authenticate their identity to party b. the protocol proceeds as follows: party a sends their identity (ida) to party b in plain text. party b. 4.6 consider a one way authentication technique based on asymmetric encryption: a b: ida ba: r₁ a b: e (pr, r₁). One very common technique to attack a system is to deliver an e mail or web page that contains a malicious piece of code called a (n) . many people consider keylogger to be a kind of . a (n) is an application of tunneling protocol. is a way to increase the security of authentication tasks. [1 pt] consider a one way authentication technique based on asymmetric encryption: a. a b a→b:i da →a:r1 →b:e(p ra,r1) b. a→b:i da b→a:e(p u a,r2) a→b:r2 i da=a ’s id r1 and r2 = a random number p ra = a's private key p u a = a's public key explain each protocol (a and b) and what type of attack each protocol is susceptible to. . [1 pt] consider a one way authentication technique based on asymmetric encryption: a. a > b: ida b a: r1 a answered step by step solved by verified expert university of north georgia, dahlonega.
Comments are closed.