Solved 1 In The Use Of Rsa Cryptography If The Public Key Chegg

Solved 1 In The Use Of Rsa Cryptography If The Public Key Chegg In the use of rsa cryptography, if the public key under rsa cryptography is (13, 119), find the private key you must show all the detailed steps. (15 marks) 2. find x such that 431" = x (mod 39), 0. here’s the best way to solve it. for problem 1, start by expressing 119 as a product of prime numbers, i.e., find p and q such that 119 = p q. 1. Our rsa calculator is a comprehensive tool to guide you in discovering the fundamental public key cryptosystem. in this article, you will learn: the operating principles of the rsa cryptography system; how to generate the rsa key (public and private); and how to calculate the decryption in the rsa algorithm.

Solved 1 In Rsa Cryptography If The Public Key 25 551 Chegg Goals: to review public key cryptography to demonstrate that confidentiality and sender authentication can be achieved simultaneously with public key cryptography to review the rsa algorithm for public key cryptography to present the proof of the rsa algorithm. In a rsa cryptosystem, a participant a uses two prime numbers p = 13 and q = 17 to generate her public and private keys. if the public key of a is 35, then the private key of a is . A user of the rsa cryptosystem may reasonably wish to use a public expo nent e that is relatively short: common choices are e = 3 or e = 216 1 = 65537. using a short public exponent results in faster public key encryption and faster public key signature verification. In 1978 1978, ron rivest, adi shamir, and leonard adleman described ([rsa78]) the following public key cryptosystem based on this one way function: bob starts by picking two very large primes p p and q q.

Solved Assigment 1 Public Key Cryptography And Rsa Q1 Chegg A user of the rsa cryptosystem may reasonably wish to use a public expo nent e that is relatively short: common choices are e = 3 or e = 216 1 = 65537. using a short public exponent results in faster public key encryption and faster public key signature verification. In 1978 1978, ron rivest, adi shamir, and leonard adleman described ([rsa78]) the following public key cryptosystem based on this one way function: bob starts by picking two very large primes p p and q q. Cribe how to nd a pair of public key and private key for rsa encryption system. solution: find two distinct large prime numbers p and q, calculate n = pq, calculate (n) = (p 1)(q 1), and determin. e; d such that ed 1(mod (n)). publi. key is (e; n), and (d; n) is private key. (b) what is the encryption. function? solution: suppose m is the. Anyone can verify signature by ‘decrypting’ with alice’s public key why it works? only alice, who owns the private key could have signed. The receiver can then decrypt the received message using their closely held private key. the use of such a public key cryptography system allows you and amazon, for example, to engage in a secure transaction without meeting up beforehand in a dark alley to exchange a key. 1. when using the public key encryption algorithm (such as rsa), plaintext must be divided into blocks of equal size. if you decide to encrypt plaintext one character at a time and transmit the encrypted character one at a time (i.e. sort of using it as a stream cipher). is this still secure? why or why not?.
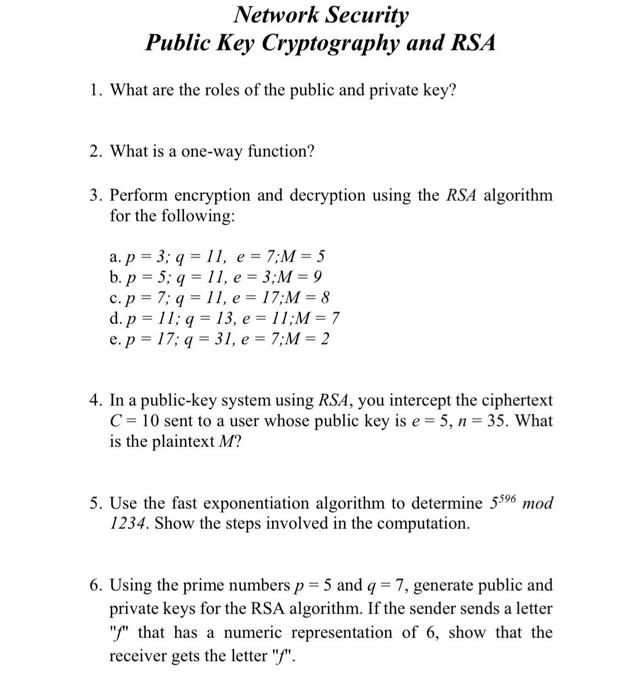
Solved Network Security Public Key Cryptography And Rsa 1 Chegg Cribe how to nd a pair of public key and private key for rsa encryption system. solution: find two distinct large prime numbers p and q, calculate n = pq, calculate (n) = (p 1)(q 1), and determin. e; d such that ed 1(mod (n)). publi. key is (e; n), and (d; n) is private key. (b) what is the encryption. function? solution: suppose m is the. Anyone can verify signature by ‘decrypting’ with alice’s public key why it works? only alice, who owns the private key could have signed. The receiver can then decrypt the received message using their closely held private key. the use of such a public key cryptography system allows you and amazon, for example, to engage in a secure transaction without meeting up beforehand in a dark alley to exchange a key. 1. when using the public key encryption algorithm (such as rsa), plaintext must be divided into blocks of equal size. if you decide to encrypt plaintext one character at a time and transmit the encrypted character one at a time (i.e. sort of using it as a stream cipher). is this still secure? why or why not?.
Comments are closed.