Secure Hashing Algorithm Bank2home

Secure Hashing Algorithm Pdf Secrecy Algorithms Secure hash algorithm (sha) is a versatile and useful cryptography technique and can ensure the data integration and verification, digital signature generation for documents and email and also secured and safe password storage and management. Sha 3: a hash function formerly called keccak, chosen in 2012 after a public competition among non nsa designers. it supports the same hash lengths as sha 2, and its internal structure differs significantly from the rest of the sha family.
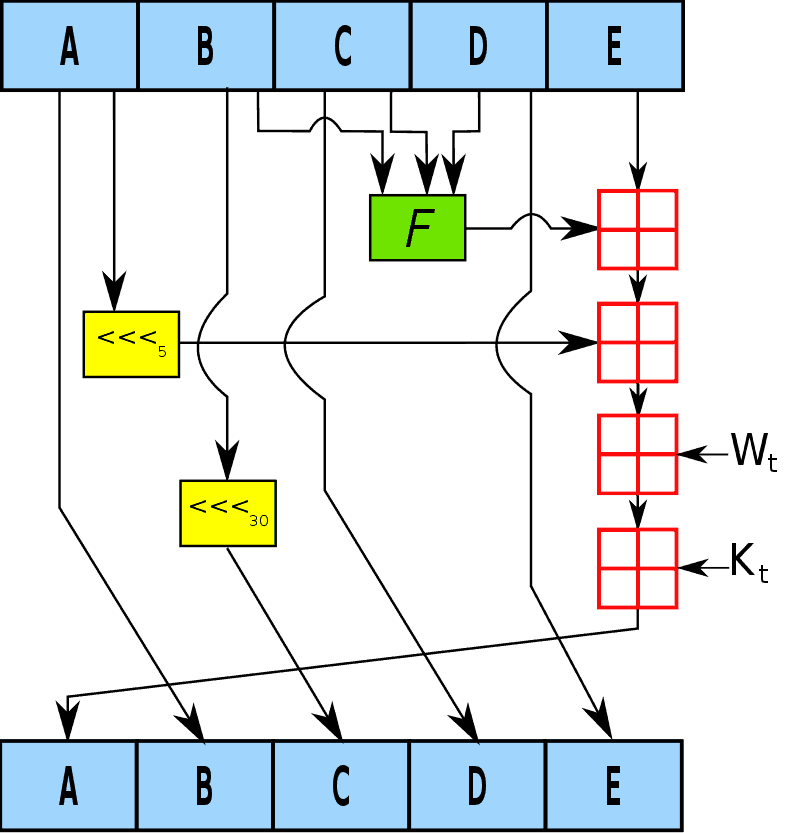
Hashing Algorithm Network Encyclopedia Modern cryptographic hash algorithms (like sha 3 and blake2) are considered secure enough for most applications. sha 2 is a family of strong cryptographic hash functions: sha 256 (256 bits hash), sha 384 (384 bits hash), sha 512 (512 bits hash), etc. A secure hashing algorithm, or sha, changes data by creating a hash digest unique to each plaintext message. the two main types of shas are sha 1 and sha 2. Secure hash algorithms, also known as sha, are a family of cryptographic functions designed to keep data secured. it works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions. Learn about the sha algorithm in cryptography, its types, applications, and how it ensures data integrity and security.

Hashing Algorithm Network Encyclopedia Secure hash algorithms, also known as sha, are a family of cryptographic functions designed to keep data secured. it works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions. Learn about the sha algorithm in cryptography, its types, applications, and how it ensures data integrity and security. Secure hash algorithm is a family of cryptographic hashing algorithms. described in rfc 3174. given an input message of arbitrary length, the algorithm generates a 160 bit hash digest, also called the message digest, which is typically displayed as a 40 digit hexadecimal number. This user friendly secure hash algorithm tutorial will guide you through the ins and outs of this essential tool in the world of cybersecurity. let's break it down together, step by step. These algorithms are specifically designed to be secure against various types of cryptographic attacks, providing robust protection for sensitive data. they also verify data integrity by generating a unique hash value that changes if the data is altered, ensuring that tampering is easily detected. Learn about sha (secure hash algorithms) encryption, its types (sha 1, sha 2, sha 3), and how they secure data. understand why sha 256 is widely used and how to protect your data.
Hashing Algorithm Network Encyclopedia Secure hash algorithm is a family of cryptographic hashing algorithms. described in rfc 3174. given an input message of arbitrary length, the algorithm generates a 160 bit hash digest, also called the message digest, which is typically displayed as a 40 digit hexadecimal number. This user friendly secure hash algorithm tutorial will guide you through the ins and outs of this essential tool in the world of cybersecurity. let's break it down together, step by step. These algorithms are specifically designed to be secure against various types of cryptographic attacks, providing robust protection for sensitive data. they also verify data integrity by generating a unique hash value that changes if the data is altered, ensuring that tampering is easily detected. Learn about sha (secure hash algorithms) encryption, its types (sha 1, sha 2, sha 3), and how they secure data. understand why sha 256 is widely used and how to protect your data.
Comments are closed.