Secure Hashing Algorithm
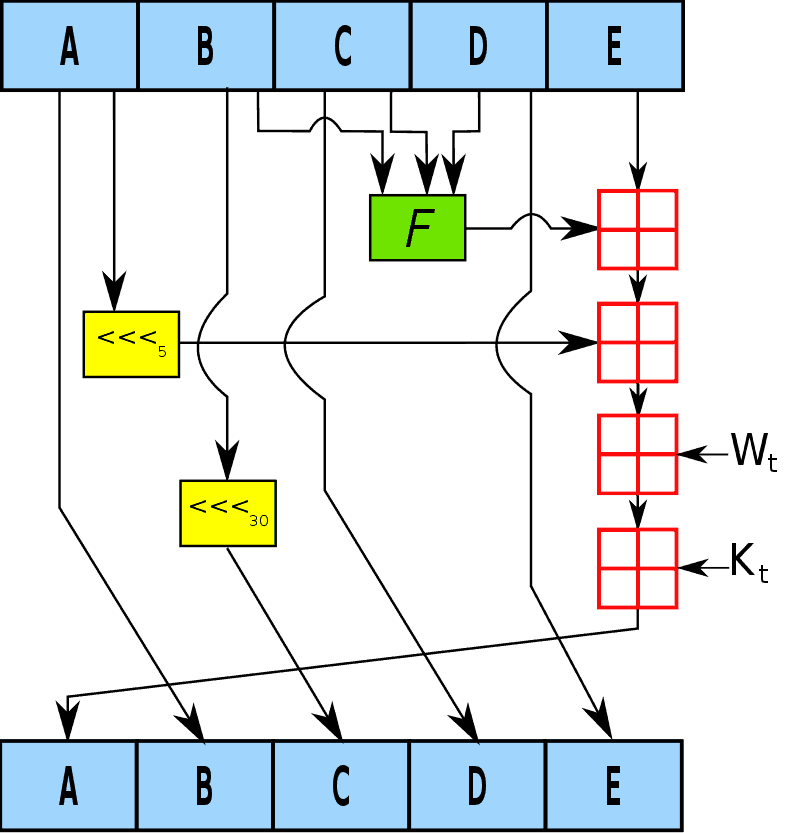
Hashing Algorithm Network Encyclopedia The secure hash algorithms are a family of cryptographic hash functions published by the national institute of standards and technology (nist) as a u.s. federal information processing standard (fips), including:. Secure hash algorithms (sha) is one of the cryptography technology and uses hashing for plaintext to message digest conversion. in this article, we will learn all about the sha like it's definition, difference between sha and aes, primary technology, key terms, practical examples, real life scenarios, pros, and cons etc.
Hashing Algorithm Network Encyclopedia A secure hashing algorithm, or sha, changes data by creating a hash digest unique to each plaintext message. the two main types of shas are sha 1 and sha 2. Modern cryptographic hash algorithms (like sha 3 and blake2) are considered secure enough for most applications. sha 2 is a family of strong cryptographic hash functions: sha 256 (256 bits hash), sha 384 (384 bits hash), sha 512 (512 bits hash), etc. Secure hash algorithms, also known as sha, are a family of cryptographic functions designed to keep data secured. it works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions. Sha stands for secure hashing algorithm. data and certificates are hashed using sha, a modified version of md5. a hashing algorithm compresses the input data into a smaller, incomprehensible form using bitwise operations, modular additions, and compression functions. you can be asking if hashing can be hacked or decoded.
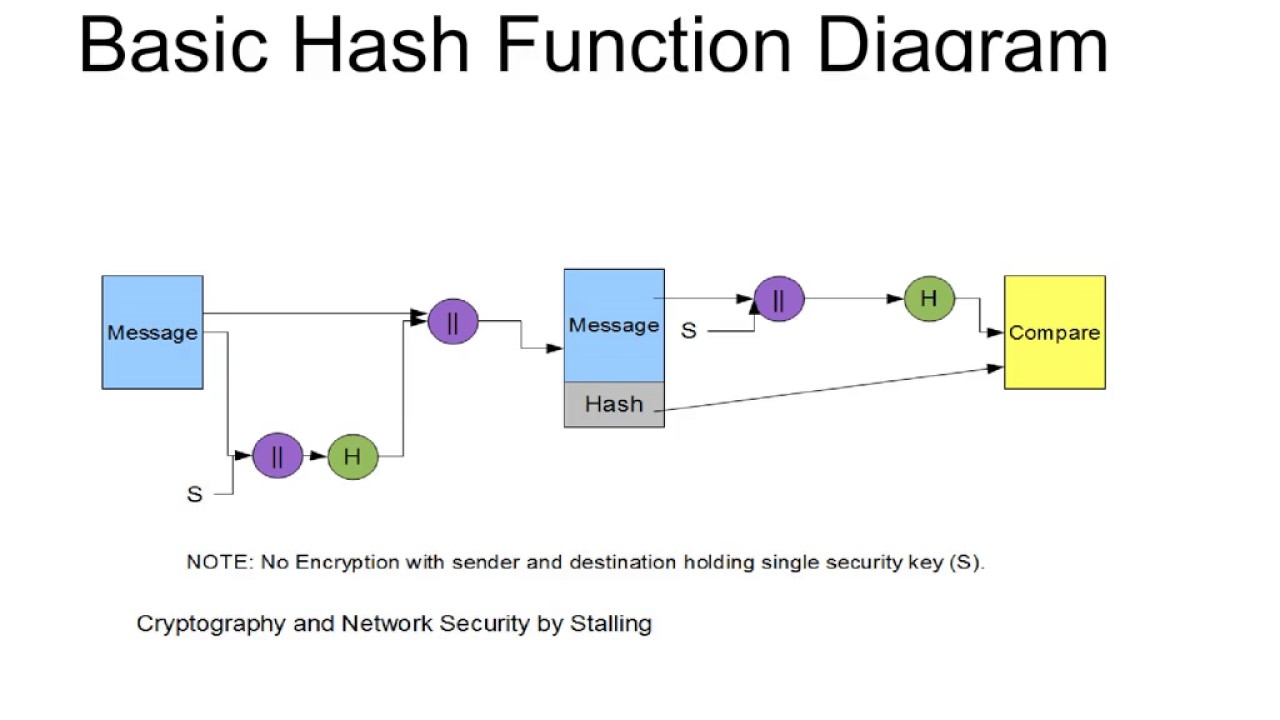
Secure Hashing Algorithm Bank2home Secure hash algorithms, also known as sha, are a family of cryptographic functions designed to keep data secured. it works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions. Sha stands for secure hashing algorithm. data and certificates are hashed using sha, a modified version of md5. a hashing algorithm compresses the input data into a smaller, incomprehensible form using bitwise operations, modular additions, and compression functions. you can be asking if hashing can be hacked or decoded. The sha (secure hash algorithm) family is a series of cryptographic hash functions designed for data integrity and security. developed by the national institute of standards and technology (nist), these algorithms are widely used in various applications such as digital signatures, certificates, and secure communication. Sha 256 is a part of the sha 2 family of algorithms, where sha stands for secure hash algorithm. published in 2001, it was a joint effort between the nsa and nist to introduce a successor to the sha 1 family, which was slowly losing strength against brute force attacks. Hash algorithm sha 256 ensures signatures authenticity in the most secure manner. password hashing – websites store user passwords in hashed format and most of the websites use sha 256 as the most secure way to protect user identity and privacy. ‘hashing’ is a cryptographic process that is used to determine the authenticity of various inputs. additionally, it is used to validate the integrity of your files, documents, and other types of data that floats all over the internet.

Secure Hashing Algorithm The sha (secure hash algorithm) family is a series of cryptographic hash functions designed for data integrity and security. developed by the national institute of standards and technology (nist), these algorithms are widely used in various applications such as digital signatures, certificates, and secure communication. Sha 256 is a part of the sha 2 family of algorithms, where sha stands for secure hash algorithm. published in 2001, it was a joint effort between the nsa and nist to introduce a successor to the sha 1 family, which was slowly losing strength against brute force attacks. Hash algorithm sha 256 ensures signatures authenticity in the most secure manner. password hashing – websites store user passwords in hashed format and most of the websites use sha 256 as the most secure way to protect user identity and privacy. ‘hashing’ is a cryptographic process that is used to determine the authenticity of various inputs. additionally, it is used to validate the integrity of your files, documents, and other types of data that floats all over the internet.
Comments are closed.