Saas Security Tips And Checklists Best Practices To Protect Your Saas

Best Practices For Saas Security Pdf Software As A Service Cloud Protect your saas data with 9 essential saas security best practices. learn how to identify and mitigate saas security risks and ensure data security. Learn how to secure your saas environment with expert insights, best practices, and checklists, ensuring robust protection for your cloud applications.

Saas Security Tips And Checklists Best Practices To Protect Your Saas To protect your application data, following the latest saas security best practices is always a great strategy. but a solid security strategy needs to go beyond the basics, incorporating risk assessments for third party vendors, real time user activity monitoring, strong authentication protocols, and routine vulnerability scans. Securing saas platforms is critical to protecting sensitive data and ensuring uninterrupted business operations. below are the best practices every organization should follow to maintain robust saas security in 2025. 1. enable multi factor authentication (mfa). Are saas security concerns boggling your mind? eliminate them with our full fledged saas security checklist, packed with expert insights and best practices. Effective saas security relies on robust access controls, encryption, continuous monitoring, and collaboration with cloud service providers to protect sensitive data and ensure compliance.

Saas Security Guide Tips And Checklists For A Secure Environment Are saas security concerns boggling your mind? eliminate them with our full fledged saas security checklist, packed with expert insights and best practices. Effective saas security relies on robust access controls, encryption, continuous monitoring, and collaboration with cloud service providers to protect sensitive data and ensure compliance. Data encryption: secure data in transit and at rest. access controls: implement strong user authentication and authorization. regular security audits: conduct vulnerability assessments periodically. compliance standards adherence: follow relevant legal and industry standards like gdpr, hipaa. Robust security infrastructure protects your saas application from both external and internal attacks. this includes multiple layers of security like authentication controls, encryption practices, network security, and active monitoring. some of the key security advantages are:. Saas security checklist is a step by step guide to helping you build user trust and improve the security of your saas application at a low cost. this review of best practices in saas security comes from our expert team who has worked on many saas projects. Protecting saas data requires a shared responsibility model and robust security practices. this checklist outlines key strategies for securing sensitive data in saas environments, emphasizing proactive measures, advanced technologies, and continuous monitoring to prevent breaches and ensure compliance.
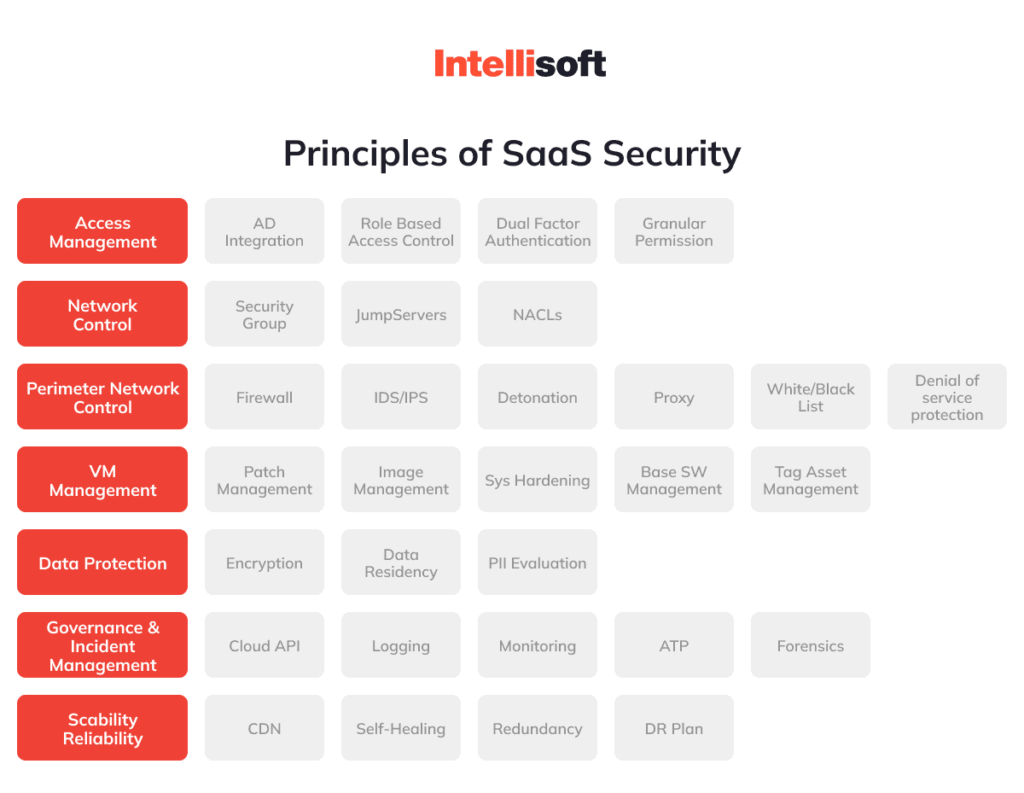
Saas Security Guide Tips And Checklists For A Secure Environment Data encryption: secure data in transit and at rest. access controls: implement strong user authentication and authorization. regular security audits: conduct vulnerability assessments periodically. compliance standards adherence: follow relevant legal and industry standards like gdpr, hipaa. Robust security infrastructure protects your saas application from both external and internal attacks. this includes multiple layers of security like authentication controls, encryption practices, network security, and active monitoring. some of the key security advantages are:. Saas security checklist is a step by step guide to helping you build user trust and improve the security of your saas application at a low cost. this review of best practices in saas security comes from our expert team who has worked on many saas projects. Protecting saas data requires a shared responsibility model and robust security practices. this checklist outlines key strategies for securing sensitive data in saas environments, emphasizing proactive measures, advanced technologies, and continuous monitoring to prevent breaches and ensure compliance.
Comments are closed.