Saas Security Checklist Best Practices To Protect Your Saas Application

Saas Security Checklist Pdf Cloud Computing Security This guide presents a step by step solution to securing your saas application, including the most important saas security best practices such as strong authentication procedures, data encryption, network security, monitoring at regular intervals, regulation compliance, user authentication, and periodic security scanning. Available for download in both pdf and excel formats, this checklist empowers your team to solidify security controls and enhance web application security to effectively shield against emerging threats and security breaches.
Saas Security Checklist Best Practices To Protect Saas App Protect your saas data with 9 essential saas security best practices. learn how to identify and mitigate saas security risks and ensure data security. Are saas security concerns boggling your mind? eliminate them with our full fledged saas security checklist, packed with expert insights and best practices. Here’s a sample checklist to get you started: proactive saas discovery and risk assessment: continuously monitor and evaluate all saas applications in use across your organization. identifying potential vulnerabilities early on is crucial to minimizing risks. In this article, we will overview why it is so important, mention common challenges as well as list some of the best practices to protect the solution. why is saas security important? since all of the data needed for it to operate is stored on cloud servers, saas security standards are the primary concern.

Saas Security Tips And Checklists Best Practices To Protect Your Saas Here’s a sample checklist to get you started: proactive saas discovery and risk assessment: continuously monitor and evaluate all saas applications in use across your organization. identifying potential vulnerabilities early on is crucial to minimizing risks. In this article, we will overview why it is so important, mention common challenges as well as list some of the best practices to protect the solution. why is saas security important? since all of the data needed for it to operate is stored on cloud servers, saas security standards are the primary concern. Key takeaways: a saas security checklist can help you look at potential vulnerabilities and also examine your security principles. it is highly recommended to brainstorm within your organization and curate a checklist that best suits your organizational security needs. Securing saas applications is paramount in today’s digitally driven business environment. tackling prevalent security concerns associated with saas apps helps protect your valuable assets, preserves customer trust, and steers clear of the expensive repercussions of a data breach. Saas security checklist is a step by step guide to helping you build user trust and improve the security of your saas application at a low cost. this review of best practices in saas security comes from our expert team who has worked on many saas projects. Protecting saas data requires a shared responsibility model and robust security practices. this checklist outlines key strategies for securing sensitive data in saas environments, emphasizing proactive measures, advanced technologies, and continuous monitoring to prevent breaches and ensure compliance.
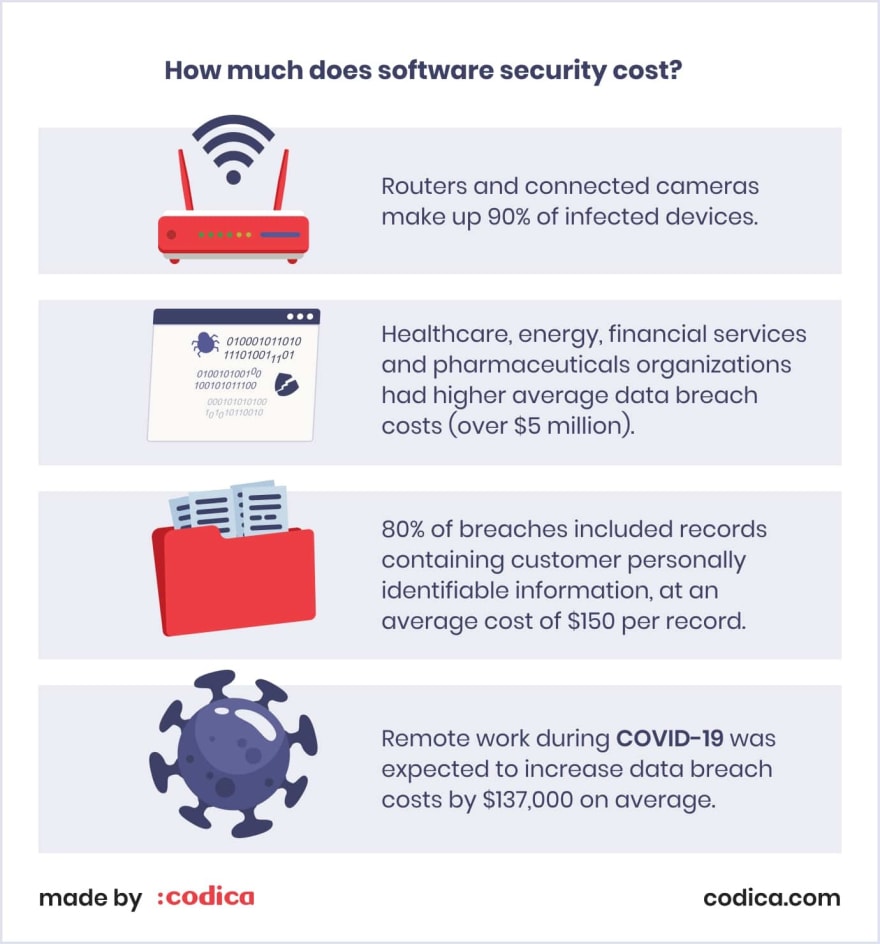
Saas Security Checklist Best Practices For Protecting Saas Apps Dev Key takeaways: a saas security checklist can help you look at potential vulnerabilities and also examine your security principles. it is highly recommended to brainstorm within your organization and curate a checklist that best suits your organizational security needs. Securing saas applications is paramount in today’s digitally driven business environment. tackling prevalent security concerns associated with saas apps helps protect your valuable assets, preserves customer trust, and steers clear of the expensive repercussions of a data breach. Saas security checklist is a step by step guide to helping you build user trust and improve the security of your saas application at a low cost. this review of best practices in saas security comes from our expert team who has worked on many saas projects. Protecting saas data requires a shared responsibility model and robust security practices. this checklist outlines key strategies for securing sensitive data in saas environments, emphasizing proactive measures, advanced technologies, and continuous monitoring to prevent breaches and ensure compliance.
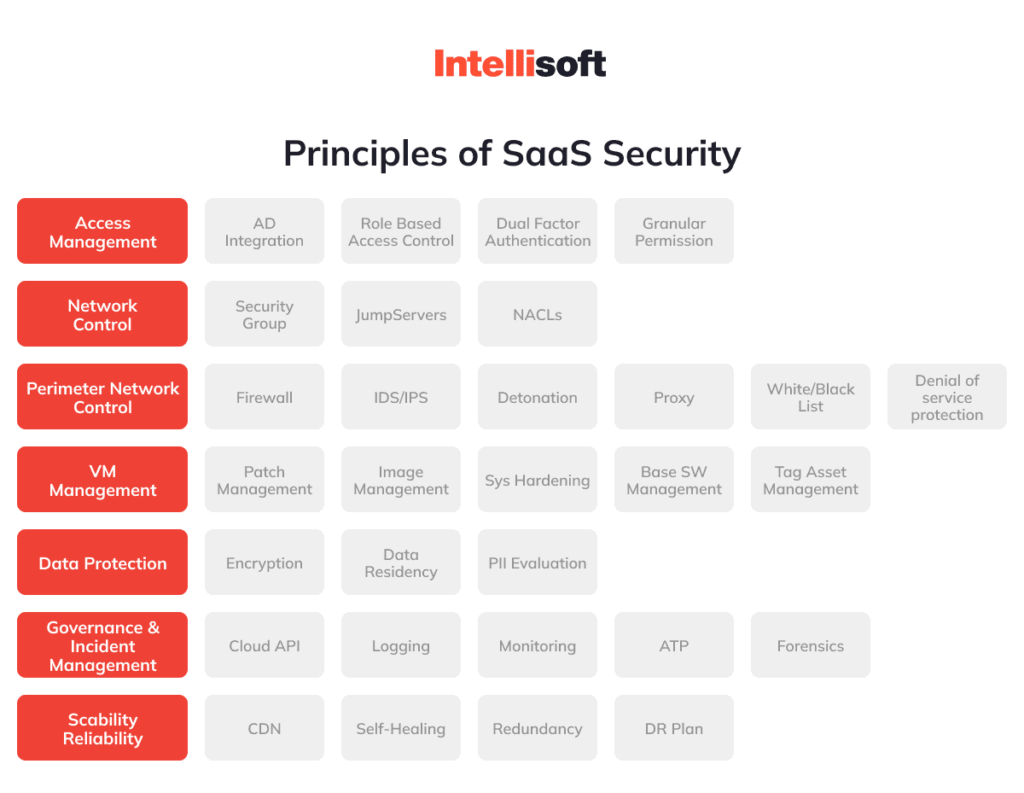
Saas Security Guide Tips And Checklists For A Secure Environment Saas security checklist is a step by step guide to helping you build user trust and improve the security of your saas application at a low cost. this review of best practices in saas security comes from our expert team who has worked on many saas projects. Protecting saas data requires a shared responsibility model and robust security practices. this checklist outlines key strategies for securing sensitive data in saas environments, emphasizing proactive measures, advanced technologies, and continuous monitoring to prevent breaches and ensure compliance.
Saas Security Guide Tips And Checklists For A Secure Environment
Comments are closed.