Rsa Asymmetric Encryption With Python

Rsa Asymmetric Encryption With Python Securid products are part of the ai powered rsa unified identity platform combining automated identity intelligence, authentication, access, governance. Rely on multi factor authentication for an extra layer of security that protects your users, systems, and data from cyberattacks.
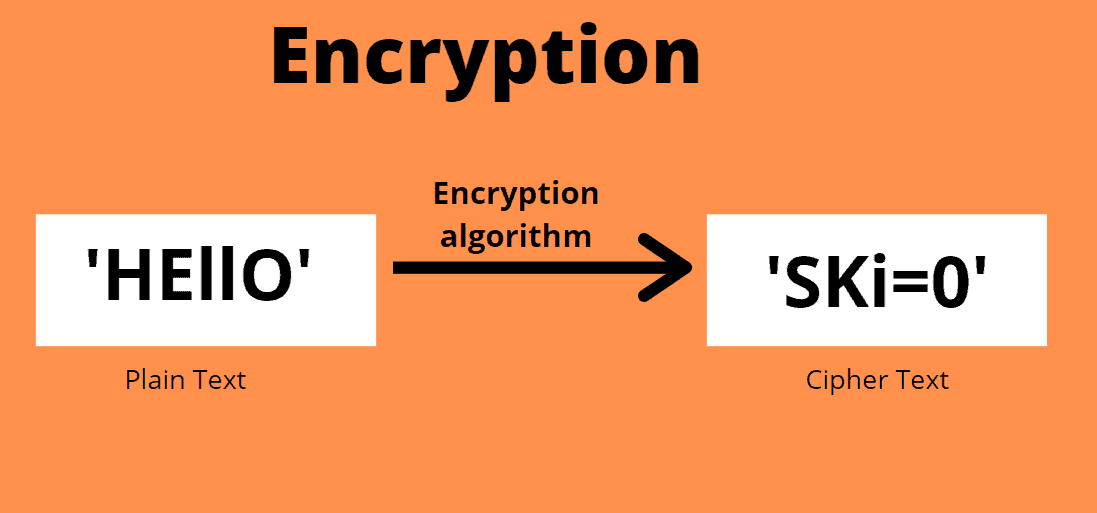
Rsa Encryption Implementation In Python Python Pool Rsa self service automates the authenticator deployment process and provides a self service console. the self service console is a web based interface that you configure to provide a variety of services to authentication manager users. Securid technical support includes a 24 7 global team, designated support engineer option and online community of product experts and customers. The rsa ishield key 2 series meets the highest security standards. begin your pre order now to fulfill eo14028, m 22 09, and m 24 14. The ai powered rsa unified identity platform protects the world's most secure organizations from today's and tomorrow's highest risk cyberattacks. rsa provides the identity intelligence, authentication, access, governance, and lifecycle capabilities needed to prevent threats, secure access, and enable compliance. more than 9,000 security first organizations trust rsa to manage 60 million.

Rsa Encryption Implementation In Python Python Pool The rsa ishield key 2 series meets the highest security standards. begin your pre order now to fulfill eo14028, m 22 09, and m 24 14. The ai powered rsa unified identity platform protects the world's most secure organizations from today's and tomorrow's highest risk cyberattacks. rsa provides the identity intelligence, authentication, access, governance, and lifecycle capabilities needed to prevent threats, secure access, and enable compliance. more than 9,000 security first organizations trust rsa to manage 60 million. Powerful cloud solutions to support your digital transformation at your own pace — tailored to fit every identity and access management requirement. Rsa helps manage your digital risk with a range of capabilities and expertise including integrated risk management, threat detection and response and more. Full iga capabilities that improve compliance, reduce risk, and optimize operations in cloud, hybrid, and on premises deployments. Rsa encryption is still commonly used for certificate signing and to establish the tls 1.2 handshake. rsa continues to review the state of quantum computing and its relation to the rsa encryption algorithms in our products and environments. rsa also continues to follow nist guidance regarding encryption and quantum computing.
Github Rnlewis Rsa Asymmetric Key Encryption Asymmetric Key Powerful cloud solutions to support your digital transformation at your own pace — tailored to fit every identity and access management requirement. Rsa helps manage your digital risk with a range of capabilities and expertise including integrated risk management, threat detection and response and more. Full iga capabilities that improve compliance, reduce risk, and optimize operations in cloud, hybrid, and on premises deployments. Rsa encryption is still commonly used for certificate signing and to establish the tls 1.2 handshake. rsa continues to review the state of quantum computing and its relation to the rsa encryption algorithms in our products and environments. rsa also continues to follow nist guidance regarding encryption and quantum computing.
Github Parthnan Rsa Encryption In Python Exercises In Python Full iga capabilities that improve compliance, reduce risk, and optimize operations in cloud, hybrid, and on premises deployments. Rsa encryption is still commonly used for certificate signing and to establish the tls 1.2 handshake. rsa continues to review the state of quantum computing and its relation to the rsa encryption algorithms in our products and environments. rsa also continues to follow nist guidance regarding encryption and quantum computing.
Github Renzycode Encryption Python Like Rsa Encryption Python Like Rsa
Comments are closed.