Rsa Algorithm Public Key Cryptography
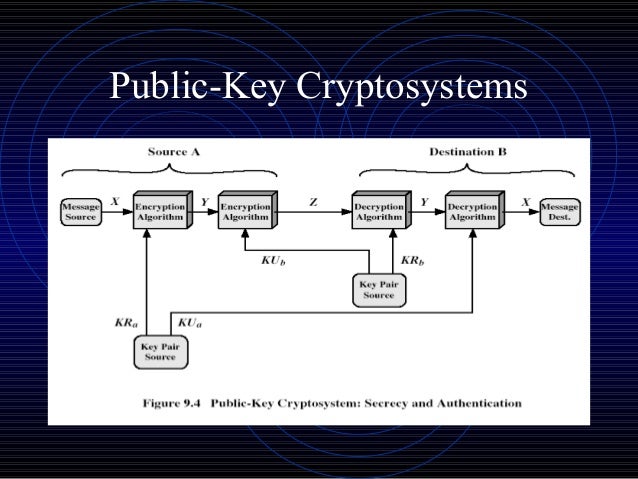
Rsa Algorithm Public Key Cryptography In a public key cryptosystem, the encryption key is public and distinct from the decryption key, which is kept secret (private). an rsa user creates and publishes a public key based on two large prime numbers, along with an auxiliary value. Goals: to review public key cryptography to demonstrate that confidentiality and sender authentication can be achieved simultaneously with public key cryptography to review the rsa algorithm for public key cryptography to present the proof of the rsa algorithm.

Rsa Algorithm Public Key Cryptography The two parties use the rsa approach to generate a public private key pair. the sender creates a symmetric key, encrypts it using the recipient's public key, and transmits the encrypted key to the recipient. Rsa encryption is a public key cryptosystem technology that employs the rsa algorithm. find out more about it here. Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures. Learn about the rsa algorithm, a crucial public key encryption method. discover how it secures data, its workings, and its applications in modern cryptography.

Rsa Algorithm Public Key Cryptography Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures. Learn about the rsa algorithm, a crucial public key encryption method. discover how it secures data, its workings, and its applications in modern cryptography. What is the rsa algorithm? the rsa algorithm (rivest shamir adleman) is a public key cryptosystem that uses a pair of keys to secure digital communication and transactions over insecure networks, such as the internet. The rsa algorithm is a foundational public key cryptography system that enables secure data transmission using a pair of keys: a public key for encryption and a private key for decryption. Key pair generation: generate random private key (typically of size 1024 4096 bits) and corresponding public key. encryption: encrypt a secret message (integer in the range [0 key length]) using the public key and decrypt it back using the secret key.
Comments are closed.