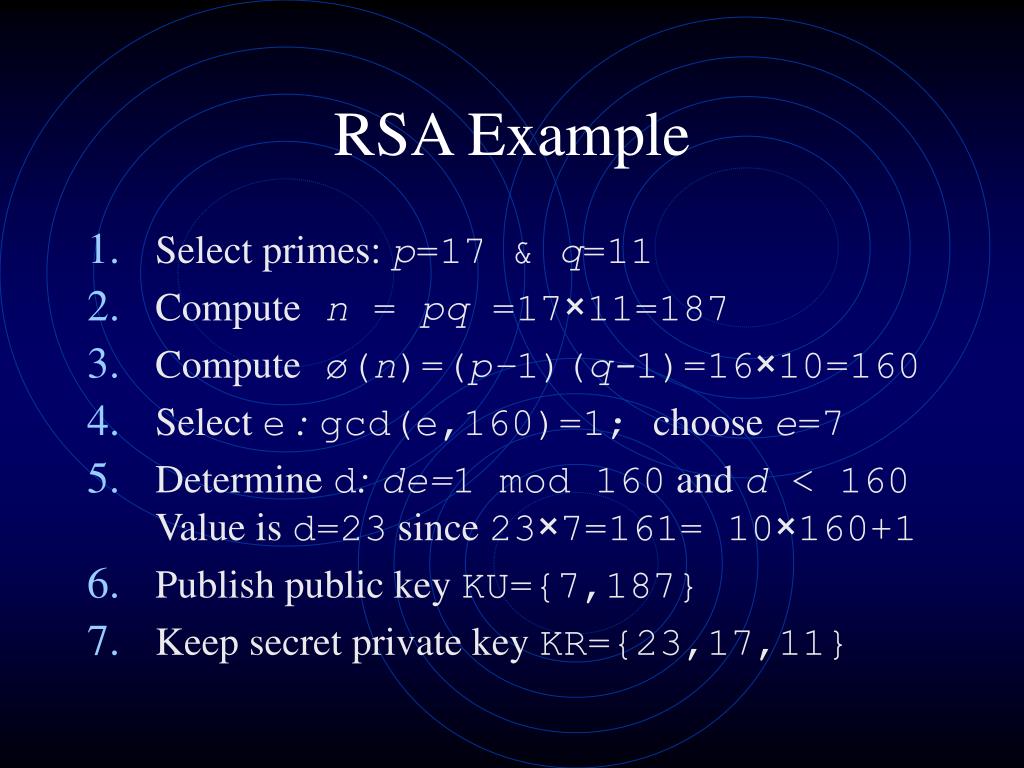
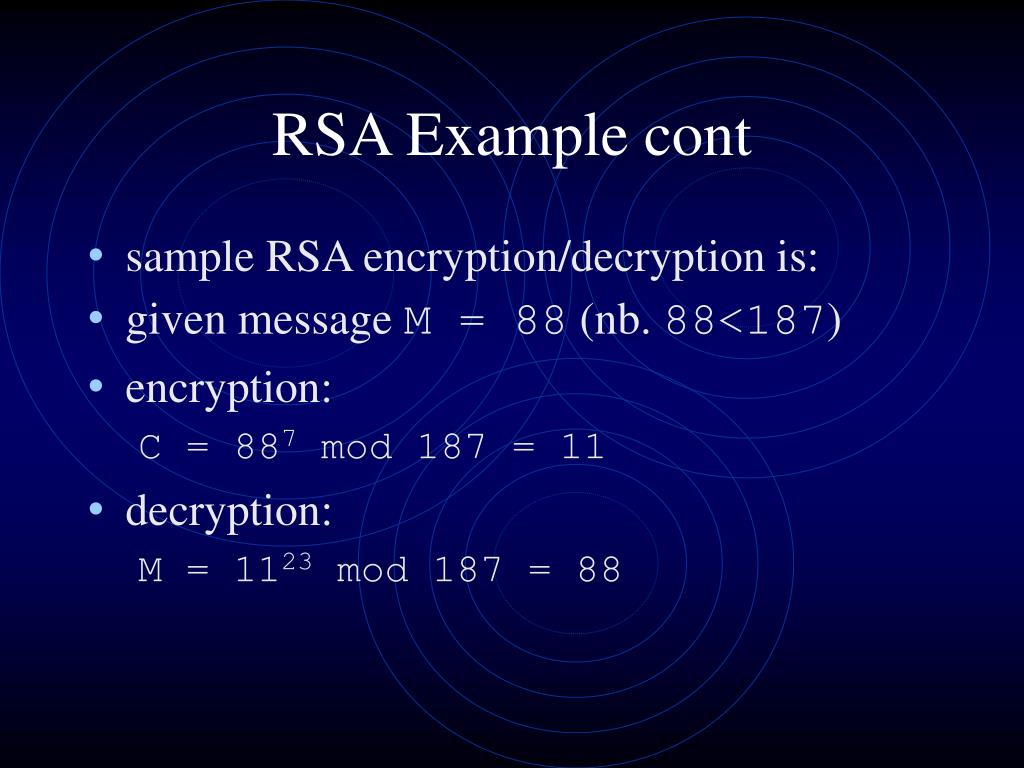
Rsa Algorithm Cryptography And Network Security Ppt Rsa Key Setup Example
Ppt Public Key Cryptography And The Rsa Algorithm Powerpoint Let’s follow the RSA algorithm step by step, with an example Let’s say Bob wants to send a private message to Alice The first step is for Alice to generate the keys, both public and private Staying on top of the global quantum game The National Security Memorandum 10 contents were highlighted as especially important, as outlining the future and is worthy of CISO’s approbationWith

Ppt Public Key Cryptography And The Rsa Algorithm Powerpoint Until 1996, in fact, the company existed almost solely to exploit public-key cryptography Even after RSA Data Security was acquired by Security Dynamics, which later changed the name to the The algorithm allows a message sender to generate a public keys to encrypt the message and the receiver is sent a generated private key using a secured database RSA Security this week announced Key Manager, server-based software for managing encryption keys used in business applications Topics Spotlight: Advancing IT Leadership Prime numbers are whole numbers greater than 1 that are not divisible by any whole number other than 1 and itself The first few are 2, 3, 5, 7, 11, 13 …
Ppt Public Key Cryptography And The Rsa Algorithm Powerpoint RSA Security this week announced Key Manager, server-based software for managing encryption keys used in business applications Topics Spotlight: Advancing IT Leadership Prime numbers are whole numbers greater than 1 that are not divisible by any whole number other than 1 and itself The first few are 2, 3, 5, 7, 11, 13 … There has been a lot of news lately about nefarious-sounding backdoors being inserted into cryptographic standards and toolkits One algorithm, a pseudo-random bit generator, Dual_EC_DRBG, was Security firm RSA publicly released its encryption algorithm Wednesday, allowing any company to freely develop solutions based on its prevalent technology The algorithm is used by both Netscape
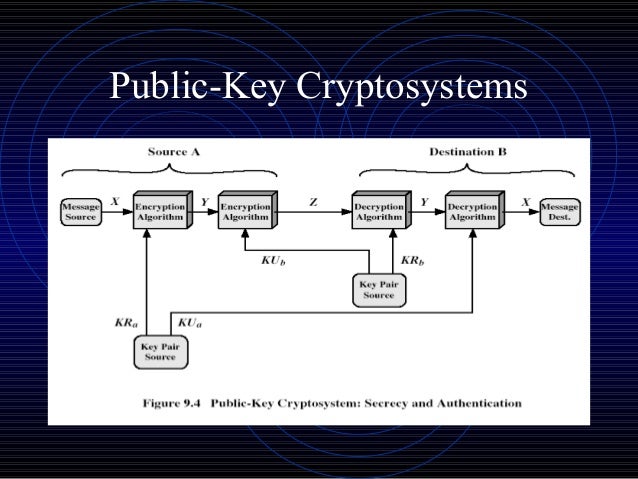
Rsa Algorithm Public Key Cryptography There has been a lot of news lately about nefarious-sounding backdoors being inserted into cryptographic standards and toolkits One algorithm, a pseudo-random bit generator, Dual_EC_DRBG, was Security firm RSA publicly released its encryption algorithm Wednesday, allowing any company to freely develop solutions based on its prevalent technology The algorithm is used by both Netscape
Comments are closed.