Public Key Cryptography Introduction To Networks Lecture 18 Slides

Lecture 11 Public Key Cryptography Pdf Cryptography Public Key Why on earth is johnny moore’s rookie card from the 1986 87 fleer set the second most valuable card in that entire set?. Invest in stocks, bonds, options, crypto, etfs, treasuries, and more with ai powered fundamental data and custom analysis.

Lecture 06 Public Key Cryptography And Pki Pdf Public Key Looking to buy sevn stock? get the latest sevn quote, news, earnings, forecast, price targets, and market insights. start investing on public . Looking to buy afos etf? get the latest afos quote, news, earnings, forecast, price targets, and market insights. start investing on public . Investing for those who take it seriouslymulti asset investing. Looking to buy bitcoin (btc) instantly in the us? trade btc at $117,670.12 with as little as $1 on public and access 20 cryptos 24 7.

Cryptography Computer Networks Lecture Notes Download Free Pdf Investing for those who take it seriouslymulti asset investing. Looking to buy bitcoin (btc) instantly in the us? trade btc at $117,670.12 with as little as $1 on public and access 20 cryptos 24 7. Boost your savings with public 's high yield account offering an industry leading 4.1% apy. no hidden fees, no minimum balance, and fully fdic insured up to $5m. Invest in a portfolio of corporate bonds and earn a 7% yield with monthly interest payments, even if the fed cuts rates. Move your savings into a treasury account with public and build a custom ladder of government backed treasuries that can generate a higher yield compared to traditional savings accounts. Browse and search our complete list of stocks traded in the u.s. markets. join our investor community and see stock prices, performance over time, and recent news.
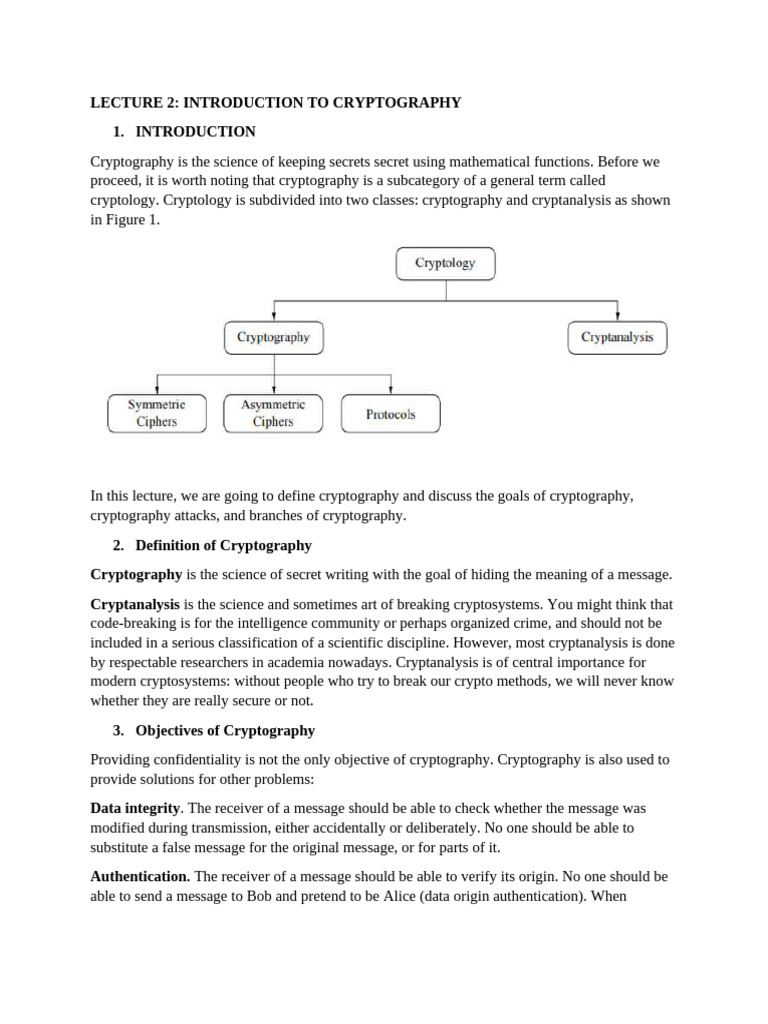
Lecture 2 Introduction Cryptography 1 Pdf Cryptography Public Boost your savings with public 's high yield account offering an industry leading 4.1% apy. no hidden fees, no minimum balance, and fully fdic insured up to $5m. Invest in a portfolio of corporate bonds and earn a 7% yield with monthly interest payments, even if the fed cuts rates. Move your savings into a treasury account with public and build a custom ladder of government backed treasuries that can generate a higher yield compared to traditional savings accounts. Browse and search our complete list of stocks traded in the u.s. markets. join our investor community and see stock prices, performance over time, and recent news.

Public Key Cryptography Introduction To Networks Lecture 18 Slides Move your savings into a treasury account with public and build a custom ladder of government backed treasuries that can generate a higher yield compared to traditional savings accounts. Browse and search our complete list of stocks traded in the u.s. markets. join our investor community and see stock prices, performance over time, and recent news.
Comments are closed.