Ppt Public Key Cryptography And Rsa Algorithm Dokumen Tips

Ppt Public Key Cryptography And Rsa Algorithm Dokumen Tips • to this day the rsa together with the aes algorithm is the mostly used algorithm in commercial systems. it is used: to protect web traffic, in the ssl protocol (security socket layer), to guarantee email privacy and authenticity in pgp (pretty good privacy) to guarantee remote connection in ssh (secure shell). The document presents an overview of cryptography, focusing on the rsa algorithm, which is a widely used public key cryptographic method for secure data transmission. it explains private key (symmetric) and public key (asymmetric) cryptography, along with the steps for key generation, encryption, and decryption in rsa.
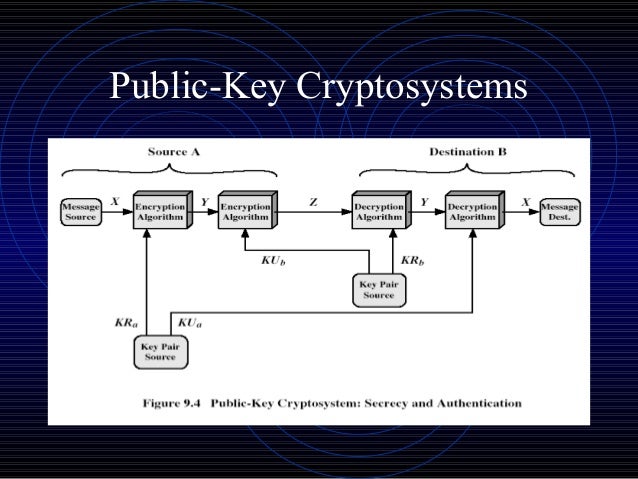
Rsa Algorithm Public Key Cryptography User a has published its public key, kue, n. b calculates c me (mod n) and transmits c. then, user a decrypts by calculating m cd (mod n). (use krd, n) 29 description of the rsa algorithm rsa algorithm (example) the keys generating select two prime number, p 17 and q 11. calculate n pq 17 x 11 187. calculate f (n) (p 1) (q 1) 16 x 10 160. Setting up an rsa cryptosystem • a user wishing to set up an rsa cryptosystem will: • choose a pair of public private keys: (pu, pr). • publish the public (encryption) key. • keep secret the private (decryption) key. Why public key cryptography? developed to address two key issues: key distribution – how to have secure communications in general without having to trust a kdc with your key digital signatures – how to verify a message comes intact from the claimed sender public invention due to whitfield diffie & martin hellman at stanford uni in 1976. The document explains the principles of public key cryptography, focusing on rsa (rivest shamir adleman), a widely used method based on number theoretic concepts, which involves a public and a private key for secure communications.

Rsa Algorithm Public Key Cryptography Why public key cryptography? developed to address two key issues: key distribution – how to have secure communications in general without having to trust a kdc with your key digital signatures – how to verify a message comes intact from the claimed sender public invention due to whitfield diffie & martin hellman at stanford uni in 1976. The document explains the principles of public key cryptography, focusing on rsa (rivest shamir adleman), a widely used method based on number theoretic concepts, which involves a public and a private key for secure communications. Rsa algorithm.ppt free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. public key cryptography uses two keys: a public key to encrypt messages and verify signatures, and a private key for decryption and signing. Public key cryptography • public key two key asymmetric cryptography involves the use of two keys: • a public key, which may be known by anybody, and can be used to encrypt messages, and verify signatures • a private key, known only to the recipient, used to decrypt messages, and sign (create) signatures • is asymmetric because. Public key cryptography uses two keys: a public key to encrypt messages and a private key to decrypt them. the rsa algorithm is based on the difficulty of factoring large prime numbers. it works by having users generate a public private key pair and publishing their public key. to encrypt a message, the sender uses the recipient's public key. Algorithms used to implement rsa, public key operations take o (k2) steps, private key operations take o (k3) steps, and key generation takes o (k4) steps, where k is the number of bits in the modulus. fast multiplication techniques, such as fft based methods, require asymptotically fewer steps. in practice, however, they are not.

Rsa Algorithm Public Key Cryptography Rsa algorithm.ppt free download as powerpoint presentation (.ppt), pdf file (.pdf), text file (.txt) or view presentation slides online. public key cryptography uses two keys: a public key to encrypt messages and verify signatures, and a private key for decryption and signing. Public key cryptography • public key two key asymmetric cryptography involves the use of two keys: • a public key, which may be known by anybody, and can be used to encrypt messages, and verify signatures • a private key, known only to the recipient, used to decrypt messages, and sign (create) signatures • is asymmetric because. Public key cryptography uses two keys: a public key to encrypt messages and a private key to decrypt them. the rsa algorithm is based on the difficulty of factoring large prime numbers. it works by having users generate a public private key pair and publishing their public key. to encrypt a message, the sender uses the recipient's public key. Algorithms used to implement rsa, public key operations take o (k2) steps, private key operations take o (k3) steps, and key generation takes o (k4) steps, where k is the number of bits in the modulus. fast multiplication techniques, such as fft based methods, require asymptotically fewer steps. in practice, however, they are not.

Rsa Algorithm Public Key Cryptography Public key cryptography uses two keys: a public key to encrypt messages and a private key to decrypt them. the rsa algorithm is based on the difficulty of factoring large prime numbers. it works by having users generate a public private key pair and publishing their public key. to encrypt a message, the sender uses the recipient's public key. Algorithms used to implement rsa, public key operations take o (k2) steps, private key operations take o (k3) steps, and key generation takes o (k4) steps, where k is the number of bits in the modulus. fast multiplication techniques, such as fft based methods, require asymptotically fewer steps. in practice, however, they are not.
Comments are closed.