Pdf A Survey On Symmetric And Asymmetric Cryptography Algorithms In

Lec 7 Symmetric And Asymmetric Cryptography Download Free Pdf This paper discusses several important algorithms used for the encryption and decryption of data in all fields, to make a comparative study for most important algorithms in terms of speed. Abstract this paper discusses several important algorithms used for the encryption and decryption of data in all fields, to make a comparative study for most important algorithms in terms of speed (implementation) and security (special keys) determine whether an encryption algorithm is good.
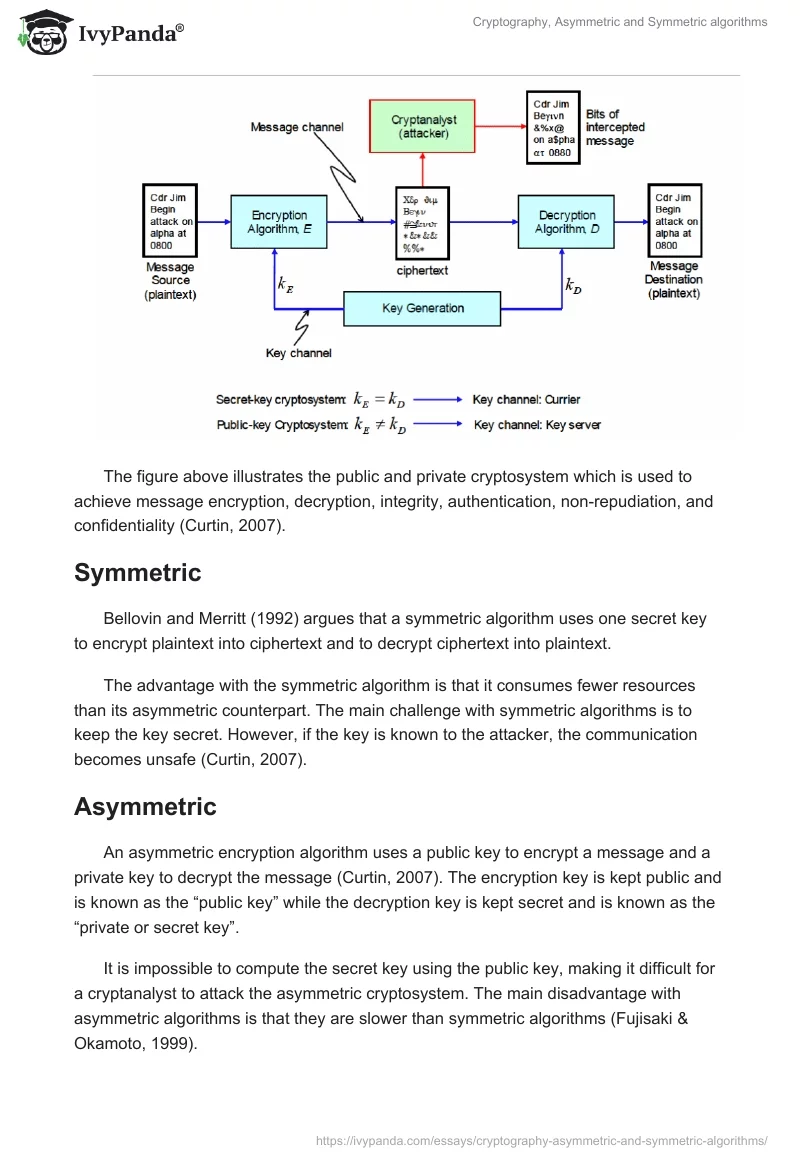
Cryptography Asymmetric And Symmetric Algorithms 1653 Words 4.0 overview of asymmetric key encryption algorithms: this section discusses about the rsa algorithm and diffie hellman key exchange algorithm. these two algorithms remain for evaluation to understand the asymmetric key concept. Defines the structure and operations that an algorithm can perform, its characteristics and how they are implemented. it also determines that the algorithm is symmetric or asymmetric that is whether it makes use of secret key or public key for encryption and decryption. In this paper various symmetric and asymmetric algorithms like aes des, and triple des, are discussed for their properties and use in mobile computing based worked solution. Asymmetric systems make it possible to authent2cate messages whose contents must be revealed to an opponent or allow atransmitter whose k has y been compromised to communmate m privacy toa receiver whose k has y been kept secret neither of which is possible using a symmetric c yptosystem.
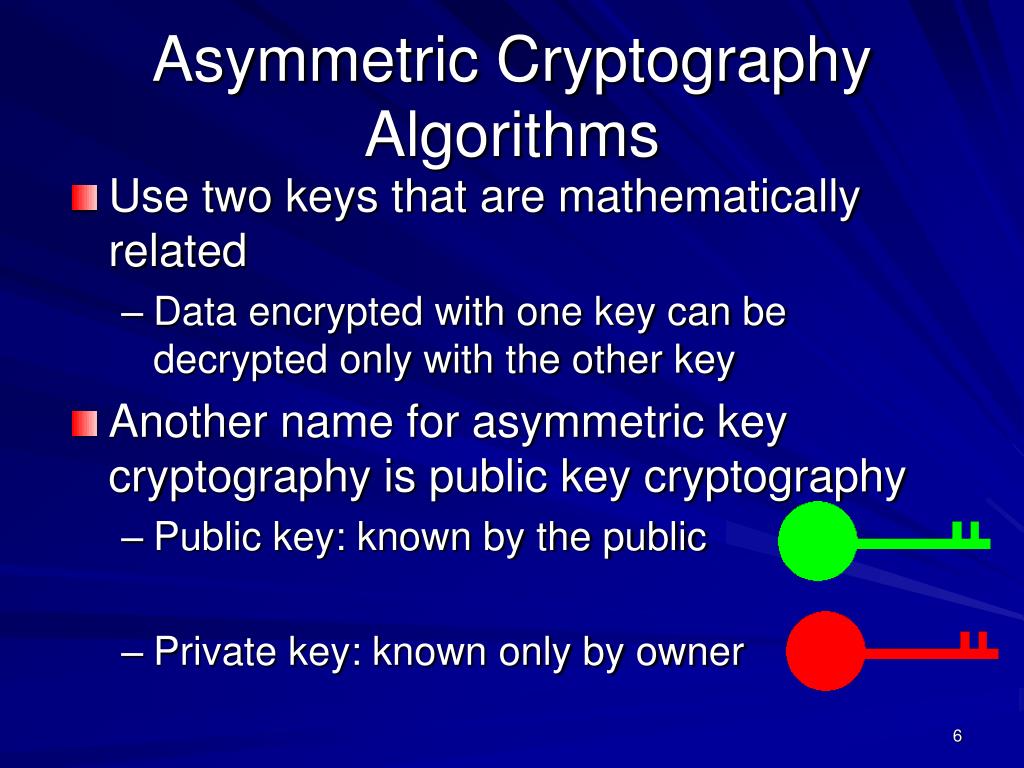
Ppt Symmetric Cryptography Asymmetric Cryptography And Digital In this paper various symmetric and asymmetric algorithms like aes des, and triple des, are discussed for their properties and use in mobile computing based worked solution. Asymmetric systems make it possible to authent2cate messages whose contents must be revealed to an opponent or allow atransmitter whose k has y been compromised to communmate m privacy toa receiver whose k has y been kept secret neither of which is possible using a symmetric c yptosystem. The cryptosystem consists of both symmetric cryptography algorithms and asymmetric cryptography algorithms. some of the asymmetric cryptography algorithms are discussed in this paper. keywords— rsa, a rsa, rabin, cipher text, plain text, encryption, decryption. This paper presents a performance evaluation of selected symmetric and asymmetric encryption algorithms such as des, 3des, aes, blowfish, rsa and diffie hellmen. In this paper, we examine the security aspects and processes involved in the design and implementation of most widely used symmetric encryption algorithms such as data encryption standard (des), triple data encryption standard (3des), blowfish, advanced encryption standard (aes) and hybrid cubes encryption algorithm (hisea). This paper conducts a comparison of the encryption speed for five different cryptographic symmetric block cipher algorithms: des, 3des, blowfish, twofish, and threefish.

Pdf Classification Of Efficient Symmetric Key Cryptography Algorithms The cryptosystem consists of both symmetric cryptography algorithms and asymmetric cryptography algorithms. some of the asymmetric cryptography algorithms are discussed in this paper. keywords— rsa, a rsa, rabin, cipher text, plain text, encryption, decryption. This paper presents a performance evaluation of selected symmetric and asymmetric encryption algorithms such as des, 3des, aes, blowfish, rsa and diffie hellmen. In this paper, we examine the security aspects and processes involved in the design and implementation of most widely used symmetric encryption algorithms such as data encryption standard (des), triple data encryption standard (3des), blowfish, advanced encryption standard (aes) and hybrid cubes encryption algorithm (hisea). This paper conducts a comparison of the encryption speed for five different cryptographic symmetric block cipher algorithms: des, 3des, blowfish, twofish, and threefish.
Comments are closed.