Mod4 Publickey Encryption Pdf Public Key Cryptography Cryptography

Public Key Cryptography Pdf Public Key Cryptography Key This document discusses public key encryption and several public key encryption algorithms including rsa. it explains that public key encryption solves the key distribution problem by using a public private key pair. Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures.

Public Key Encryption Download Free Pdf Public Key Cryptography Each receiver possesses a unique decryption key, generally referred to as his private key. receiver needs to publish an encryption key, referred to as his public key. some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver. Requirements for public key crypto key generation: computationally easy to generate a pair (public key pk, private key sk) • computationally infeasible to determine private key pk given only public key pk encryption: given plaintext m and public key pk, easy to compute ciphertext c=epk(m). Present an overview of the basic principles of public key cryptosystems. explain the two distinct uses of public key cryptosystems. list and explain the requirements for a public key cryptosystem. present an overview of the rsa algorithm. understand the timing attack. If knowing the public key lets anyone encrypt a message but allows only the intended recipient to decrypt that message, the problem goes away. a coding strategy that allows encryption keys to be shared but protects decryption keys is called public key encryption.

An Introduction To Basic Security Concepts Authentication Access Present an overview of the basic principles of public key cryptosystems. explain the two distinct uses of public key cryptosystems. list and explain the requirements for a public key cryptosystem. present an overview of the rsa algorithm. understand the timing attack. If knowing the public key lets anyone encrypt a message but allows only the intended recipient to decrypt that message, the problem goes away. a coding strategy that allows encryption keys to be shared but protects decryption keys is called public key encryption. The established key can then be used to encrypt subsequent communication using a symmetric key cipher “new directions in cryptography” by whitfield diffie and martin hellman, 1976. Such as encryption and decryption or signature generation and signature verification public key certificate a digital document issued and digitally signed by the private key of the certification authority that binds scriver to a public key. the certificate indicates that the sub. Asymmetric key public key cryptography asymmetric key cryptosystems public key cryptosystems use a pair of keys: public key (encryption key) and private key (decryption key). However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc.
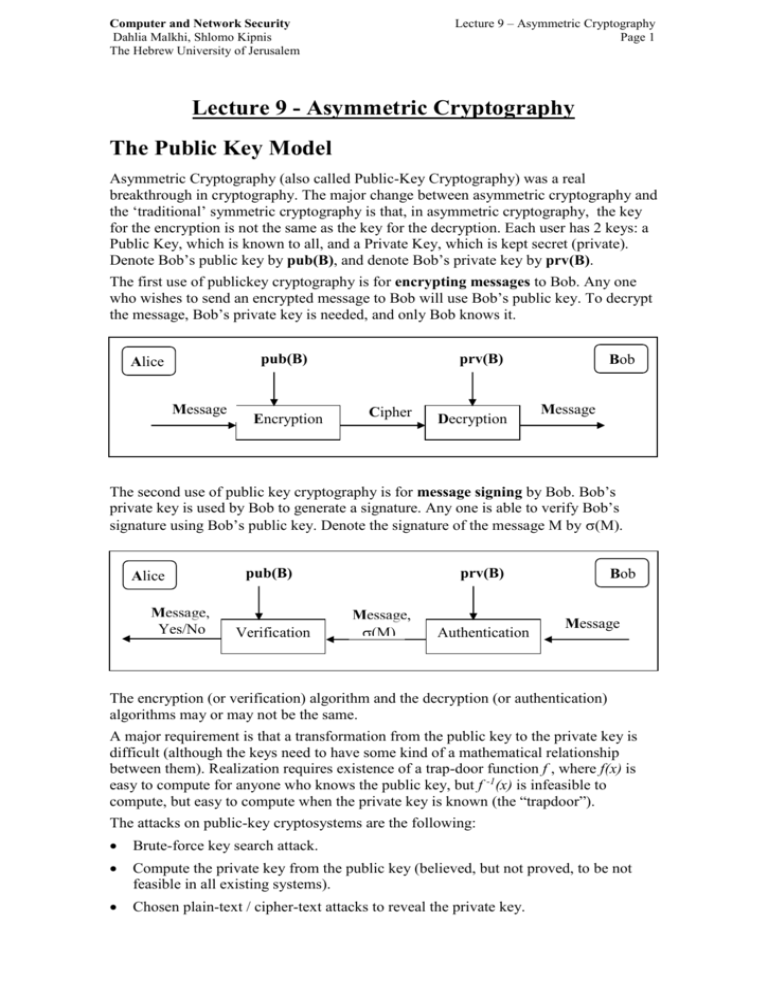
Public Key Cryptography The established key can then be used to encrypt subsequent communication using a symmetric key cipher “new directions in cryptography” by whitfield diffie and martin hellman, 1976. Such as encryption and decryption or signature generation and signature verification public key certificate a digital document issued and digitally signed by the private key of the certification authority that binds scriver to a public key. the certificate indicates that the sub. Asymmetric key public key cryptography asymmetric key cryptosystems public key cryptosystems use a pair of keys: public key (encryption key) and private key (decryption key). However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc.
Comments are closed.