Microservices Security Best Practices To Secure Microservices Edureka

Best Practices In Implementing A Secure Microservices Architecture With microservices, IT should abandon the old ways of securing applications and focus on the three guiding principles of traceability, visibility, and compartmentalization The integration of microservices has exploded in recent years Here are the best security practices for microservices-based applications

Microservices Architecture Training Https Www Edureka Co Evaluating, monitoring, and improving security procedures and platforms is an ongoing responsibility for law firms To protect your client and case data, consider the following strategies and best Here are four observability best practices for devops teams building and supporting apps, microservices, and databases Building secure, resilient, and scalable cloud-native applications requires a new set of best practices that diverge from traditional application development Start with these six Let's take a look at some of the most critical security practices to consider in 2024 to help ensure your applications are secure, resilient and trustworthy
Microservices Security Best Practices Of Microservices Security Edureka Building secure, resilient, and scalable cloud-native applications requires a new set of best practices that diverge from traditional application development Start with these six Let's take a look at some of the most critical security practices to consider in 2024 to help ensure your applications are secure, resilient and trustworthy How integrators can facilitate a secure mall environment by working with facility management and individual stores While microservices provide an excellent framework for building scalable, modular applications, their success hinges on following best practices We discuss the challenges and best practices for securing embedded systems from various types of malicious events, and also explore security concepts and standards that make it easier to implement Companies are rushing to climb aboard the microservices bandwagon, but they are not doing it for security reasons, warns Alexei Balaganski, lead analyst at KuppingerCole “They are doing it for
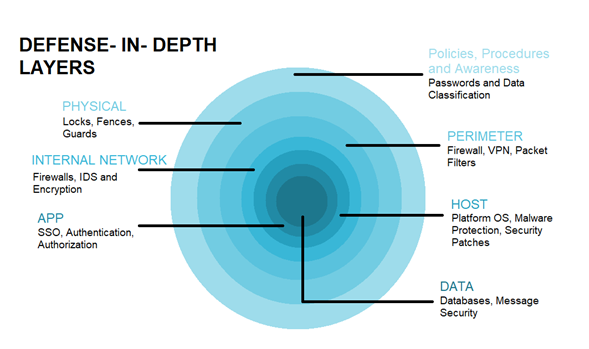
Security Best Practices For Microservices Architecture How integrators can facilitate a secure mall environment by working with facility management and individual stores While microservices provide an excellent framework for building scalable, modular applications, their success hinges on following best practices We discuss the challenges and best practices for securing embedded systems from various types of malicious events, and also explore security concepts and standards that make it easier to implement Companies are rushing to climb aboard the microservices bandwagon, but they are not doing it for security reasons, warns Alexei Balaganski, lead analyst at KuppingerCole “They are doing it for

Security Best Practices For Microservices Architecture We discuss the challenges and best practices for securing embedded systems from various types of malicious events, and also explore security concepts and standards that make it easier to implement Companies are rushing to climb aboard the microservices bandwagon, but they are not doing it for security reasons, warns Alexei Balaganski, lead analyst at KuppingerCole “They are doing it for
Comments are closed.