Learn To Hack Directory Fuzzing Php Reverse Shells

Php Reverse Shell Pdf Unix Computer Engineering If you you are new to this series and would like to follow along, watch this video to setup your virtual machines: • get started hacking: creating a virtu more. In this post, we’ll demonstrate how to exploit a file upload vulnerability using a simple php web shell script. a php web shell allows attackers to execute system commands on the server via.
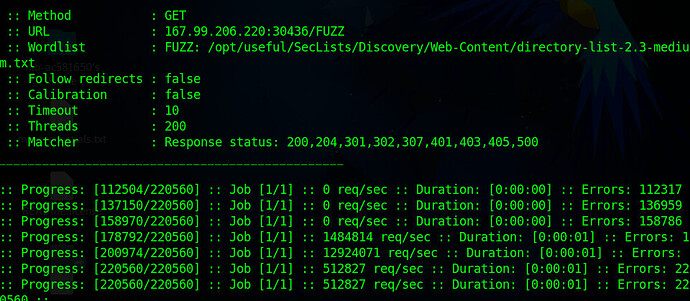
Directory Fuzzing Academy Academy Hack The Box Forums In this lesson, we’ll use burpsuite to conduct a privilege escalation attack. we’ll hack into a machine provided by tryhackme. this is one of my favorite companies for learning cybersecurity. they have incredible resources for free (and 100% legal) hacking!. Master web shells for pentesting: upload methods, av evasion, and post exploitation. learn to detect and analyze malicious shells. If the victim has php installed, you can use it to create a reverse shell with a few lines of code. first, launch a listener on the attacking machine using the command below. We can leverage a tool from github to generate a base64 link that exploits the php filter and executes a php command on the target server: → tool: php filter chain generator. → step 1: create a reverse shell locally: → step 2: generate a base64 encoded payload using the tool and insert it into the url:.

Andrew S Research Fuzzing Php With Domato If the victim has php installed, you can use it to create a reverse shell with a few lines of code. first, launch a listener on the attacking machine using the command below. We can leverage a tool from github to generate a base64 link that exploits the php filter and executes a php command on the target server: → tool: php filter chain generator. → step 1: create a reverse shell locally: → step 2: generate a base64 encoded payload using the tool and insert it into the url:. Along the way we get to use lots of tools like nmap, gobuster, burpsuite, the pentestmonkey reverse php shell, and gtfobins. as we use these tools, we learn about source code analysis, directory enumeration, exploiting an upload form, fuzzing, and privilege escalation using a binary with suid permissions. For number 2 you mixed a command line reverse shell that gets executed by php (that’s what the „php r“ stands for) with php script tags that get executed automatically. This article will describe how to access a tryhackme machine by exploiting a vulnerable php application. the room is called vulnversity and its challenge is to capture user’s and root’s flags. This is a detailed cheat sheet of various methods using lfi & rce & webshells to take reverse shell & exploitation. join certcube labs oscp training.
Github Ngductung Reverse Shell Php Along the way we get to use lots of tools like nmap, gobuster, burpsuite, the pentestmonkey reverse php shell, and gtfobins. as we use these tools, we learn about source code analysis, directory enumeration, exploiting an upload form, fuzzing, and privilege escalation using a binary with suid permissions. For number 2 you mixed a command line reverse shell that gets executed by php (that’s what the „php r“ stands for) with php script tags that get executed automatically. This article will describe how to access a tryhackme machine by exploiting a vulnerable php application. the room is called vulnversity and its challenge is to capture user’s and root’s flags. This is a detailed cheat sheet of various methods using lfi & rce & webshells to take reverse shell & exploitation. join certcube labs oscp training.
Comments are closed.