Issue 73 Encryption Algorithm

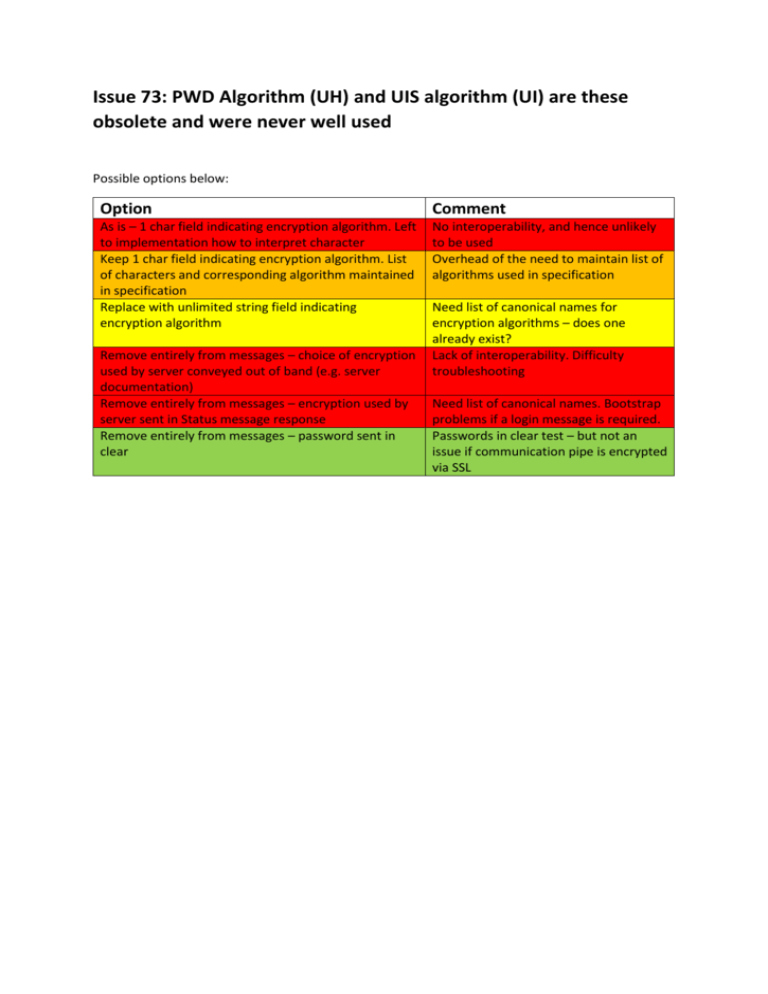
New Encryption Algorithm Pdf Cryptography Key Cryptography Issue 73: pwd algorithm (uh) and uis algorithm (ui) are these obsolete and were never well used possible options below: option comment as is – 1 char field indicating encryption algorithm. left to implementation how to interpret character keep 1 char field indicating encryption algorithm. list of characters and corresponding algorithm maintained. Cryptographic failures (previously called “sensitive data exposure” in the owasp top ten) refer to vulnerabilities that occur due to the incorrect implementation, configuration, or use of.
Issue 73 Encryption Algorithm Cisco ios secure shell (ssh) servers support the encryption algorithms (advanced encryption standard counter mode [aes ctr], aes cipher block chaining [aes cbc], triple data encryption standard [3des]) in the following order:. However, public key encryption has proved indispensable for key management, for distributing the keys needed for the more traditional symmetric key encryption decryption of the content, for digital signature applications, etc. We have an expert written solution to this problem! fill in the missing word: the output of a hashing algorithm is . which one of the following is a benefit of computer based training (cbt)? what is the most crucial element of any security instruction program?. In this chapter, different types of parallel architectures and interconnection networks are discussed before actually implementing the parallel algorithm of encryption.

Issue 73 Encryption Algorithm We have an expert written solution to this problem! fill in the missing word: the output of a hashing algorithm is . which one of the following is a benefit of computer based training (cbt)? what is the most crucial element of any security instruction program?. In this chapter, different types of parallel architectures and interconnection networks are discussed before actually implementing the parallel algorithm of encryption. Utilizing pseudo random numbers generated by lc cmhm, a tailored encryption algorithm is developed specifically for the structural features of 3d medical models. this algorithm encrypts both the faces and vertices of the 3d model, disrupting inherent correlations to enhance encryption effectiveness. In this paper, we examine the security aspects and processes involved in the design and implementation of most widely used symmetric encryption algorithms such as data encryption standard (des. Caesar cipher is a mono alphabetic cipher. it is a type of substitution cipher in which each letter in the plaintext is replaced by a letter. in this paper, author modified the traditional caesar cipher and fixed the key size as one. A. rc4 stream cipher rc4 encryption algorithm is shared key stream cipher, which is needed to secure exchange the content. symmetric key algorithm usually works as identically for encryption and decryption such as the data stream is typically ex ored with generated key sequences.
Issue 73 Encryption Algorithm Utilizing pseudo random numbers generated by lc cmhm, a tailored encryption algorithm is developed specifically for the structural features of 3d medical models. this algorithm encrypts both the faces and vertices of the 3d model, disrupting inherent correlations to enhance encryption effectiveness. In this paper, we examine the security aspects and processes involved in the design and implementation of most widely used symmetric encryption algorithms such as data encryption standard (des. Caesar cipher is a mono alphabetic cipher. it is a type of substitution cipher in which each letter in the plaintext is replaced by a letter. in this paper, author modified the traditional caesar cipher and fixed the key size as one. A. rc4 stream cipher rc4 encryption algorithm is shared key stream cipher, which is needed to secure exchange the content. symmetric key algorithm usually works as identically for encryption and decryption such as the data stream is typically ex ored with generated key sequences.

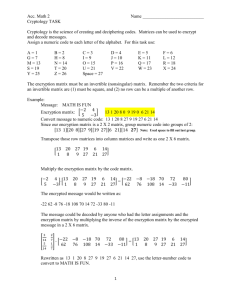
Encryption And Decryption Algorithms 1 Pdf Cryptography Encryption Caesar cipher is a mono alphabetic cipher. it is a type of substitution cipher in which each letter in the plaintext is replaced by a letter. in this paper, author modified the traditional caesar cipher and fixed the key size as one. A. rc4 stream cipher rc4 encryption algorithm is shared key stream cipher, which is needed to secure exchange the content. symmetric key algorithm usually works as identically for encryption and decryption such as the data stream is typically ex ored with generated key sequences.

3 Encryption Algorithm Download Scientific Diagram
Comments are closed.