Introduction To Encryption Techniques Css322 Lecture 2 2013

02 L2 L3 Ch02 Classical Encryption Techniques Pdf Cryptography Model for encryption for confidentiality, cryptography terminology, caesar and monoalphabetic ciphers, brute force attacks. lecture 2 of css322 security and. From the website you can download software from the cdrom that provides many examples and animations of classical (and current) encryption algorithms. cryptool free software for apply many encryption algorithms (classical, symmetric, public key) and analysing (breaking) ciphertexts.
Cloud Security Lecture 1 Pdf Cryptography Encryption Block ciphers and des css322: security and cryptography sirindhorn international institute of technology thammasat university prepared by steven gordon on 28 october 2013 css322y13s2l03, steve courses 2013 s2 css322 lectures des.tex, r2963. Css322, semester 2, 2013, lectures at sirindhorn international institute of technology, thammasat university, thailand by steven gordon. course material via: teaching | steven gordon. Introduction to encryption techniques the subject of encryption is fundamental to a com plete network security strategy. with increased use of public facilities such as the internet comes a need to guarantee message confidentiality and integrity for many applications. Css322, semester 2, 2013, lectures at sirindhorn international institute of technology, thammasat university, thailand by steven gordon. course material via:.

Ch3 Classical Encryption Techniques Pdf Classical Encryption Introduction to encryption techniques the subject of encryption is fundamental to a com plete network security strategy. with increased use of public facilities such as the internet comes a need to guarantee message confidentiality and integrity for many applications. Css322, semester 2, 2013, lectures at sirindhorn international institute of technology, thammasat university, thailand by steven gordon. course material via:. I symmetric algorithms used same secret key for encryption and decryption i asymmetric algorithms in public key cryptography use one key for encryption and different but related key for decryption i characteristics of asymmetric algorithms: i require: computationally infeasible to determine. Css322 { classical encryption techniques notes figure 1: caesar cipher example; lecture 02 figure 2: playfair cipher example; lecture 03 figure 3: rail fence cipher example; lecture 03 figure 4: rows columns cipher example; lecture 03. What will you learn in css 322? • the role of security in computers and networks • theory and concepts behind secure systems. – cryptography . • details of important and popular algorithms. – des, aes, rsa, digital signatures, … • internet security techniques and attacks. – layered security, viruses, spyware, …. Css322 { classical encryption techniques notes figure 1: caesar cipher decryption; lecture 01 figure 2: attack on caesar cipher; lecture 02 figure 3: key length of a monoalphabetic cipher; lecture 02 figure 4: encryption with playfair cipher; lecture 03.
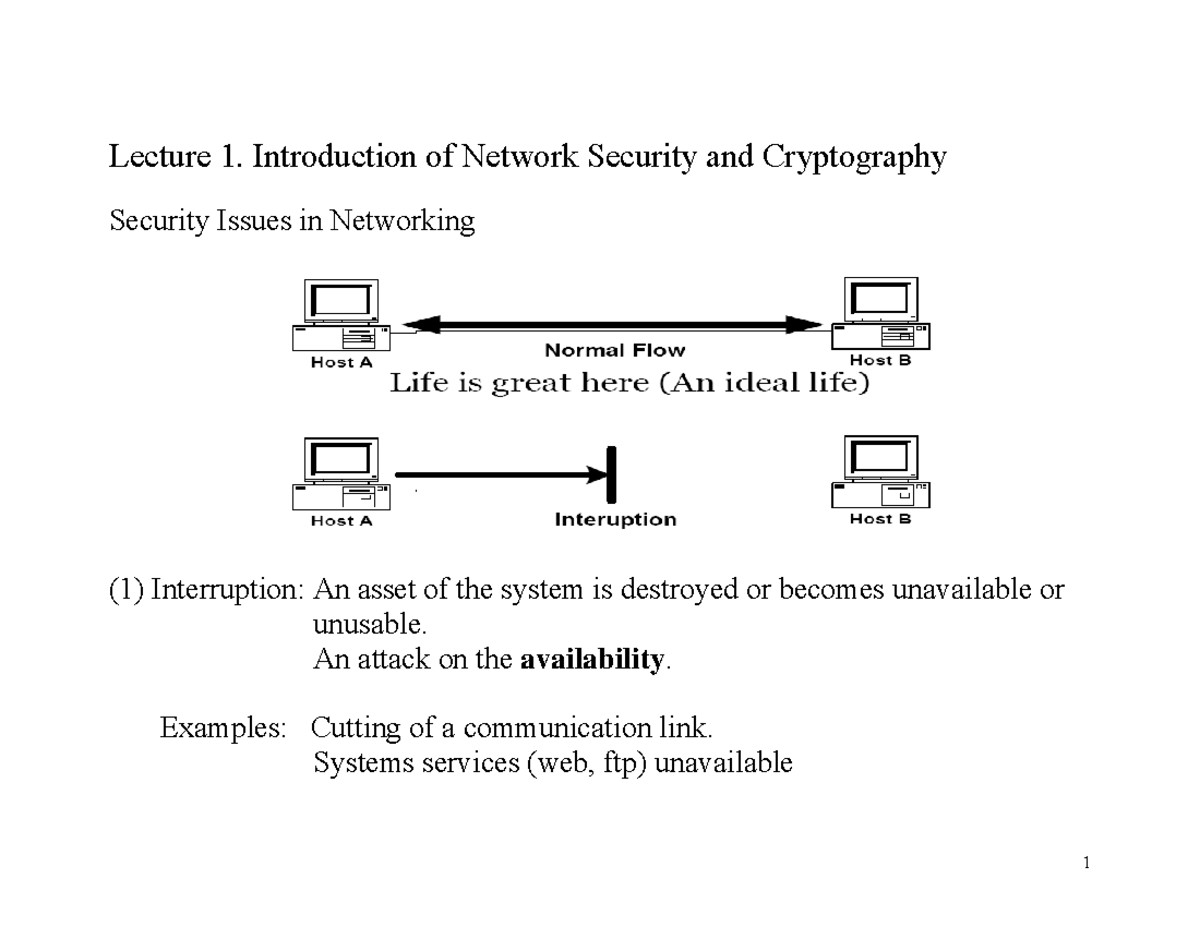
Lecture 1 Introduction Lecture 1 Introduction Of Network Security I symmetric algorithms used same secret key for encryption and decryption i asymmetric algorithms in public key cryptography use one key for encryption and different but related key for decryption i characteristics of asymmetric algorithms: i require: computationally infeasible to determine. Css322 { classical encryption techniques notes figure 1: caesar cipher example; lecture 02 figure 2: playfair cipher example; lecture 03 figure 3: rail fence cipher example; lecture 03 figure 4: rows columns cipher example; lecture 03. What will you learn in css 322? • the role of security in computers and networks • theory and concepts behind secure systems. – cryptography . • details of important and popular algorithms. – des, aes, rsa, digital signatures, … • internet security techniques and attacks. – layered security, viruses, spyware, …. Css322 { classical encryption techniques notes figure 1: caesar cipher decryption; lecture 01 figure 2: attack on caesar cipher; lecture 02 figure 3: key length of a monoalphabetic cipher; lecture 02 figure 4: encryption with playfair cipher; lecture 03.
Comments are closed.