Impact Of Sybil Attack On Blockchain Network Training Ppt Ppt Example
Impact Of Sybil Attack On Blockchain Network Training Ppt Ppt Example This slide showcases the multiple impacts of sybil attack on blockchain network. the multiple impacts of sybil attack such as creation of fake identities, blocking users, performing reverse transaction, and security and privacy risk. Motivation for sybil attack • one entity presents multiple identities for malicious intent • disrupt geographic and multi path routing protocols by “being in more than one place at once” and reducing diversity • relevant in many contexts • p2p network • ad hoc networks • wireless sensor networks.
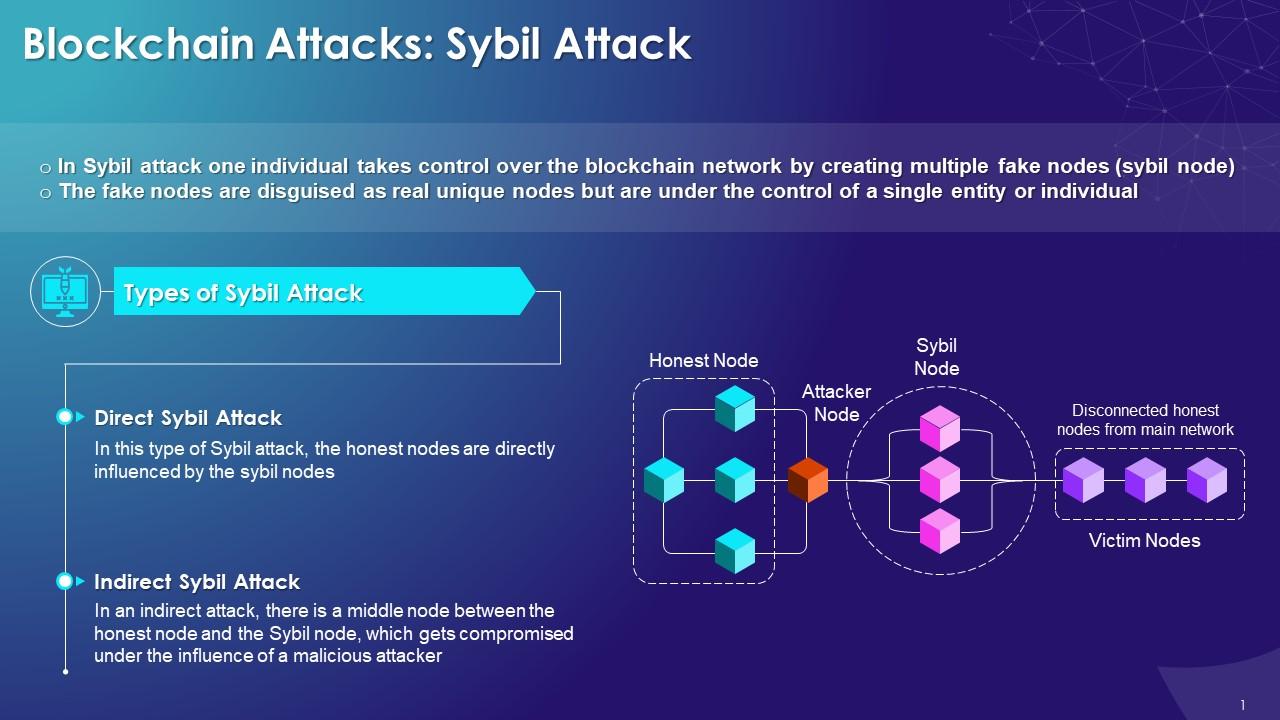
Sybil Attack On Blockchain Network Training Ppt Ppt Powerpoint The following slide showcases major scenarios of sybil attack to minimize the impact and manage operations. it includes elements such as attack on bitcoin network, tor network, peer to peer model, etc. 1 the sybil attack john r. douceur microsoft research presented for cs294 4 by benjamin poon 2 outline background motivation model lemmas conclusion 3 outline background motivation model lemmas conclusion 4 background p2p systems use multiple, independent entities to mitigate possible damage by other hostile entities replication computations. A sybil attack poses a significant threat to the integrity and security of blockchain networks. in this type of attack, a malicious actor creates multiple fake identities to gain disproportionate influence over the network. The following slide illustrates brief introduction of sybil attack to reduce security violations. it includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.
Prevention From Sybil Attack On Blockchain Network Training Ppt A sybil attack poses a significant threat to the integrity and security of blockchain networks. in this type of attack, a malicious actor creates multiple fake identities to gain disproportionate influence over the network. The following slide illustrates brief introduction of sybil attack to reduce security violations. it includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. This slide gives an overview of the sybil attack in the blockchain network. the purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network. Introduction to sybil attack • centralized authority: • control sybil attack easily • verify real life credential • hard for worldwide to trust • single point of failure – bottleneck, dos • scare away potential users – requires sensitive information. These slides cover the adverse impact of the sybil attack on a blockchain, such as security and privacy risks and reverse transactions. these also include information about strategies to preventive to avoid the sybil attack. Sybil attack is one in which an attacker subverts the reputation system of a cheng & friedman 'sybil proof reputation mechanisms' – a free powerpoint ppt presentation (displayed as an html5 slide show) on powershow id: 1210a3 ntvkn.
Comments are closed.