How To Secure And Rotate Api Keys And Secrets For Microservices

Tutorial Rotate Api Keys Documentation Esri Developer Microservices increase security risks with more attack surfaces, inconsistent storage, and complex access controls. learn how centralized management, automated rotation, and zero trust principles keep secrets secure. One of the best practices for securing and rotating api keys and secrets in a microservices architecture is to use a centralized vault that stores and encrypts them. a vault is a service.

Tutorial Rotate Api Keys Documentation Esri Developer Learn how to implement secure, automated secret rotation for java microservices using hashicorp vault and kubernetes. 🔗 secure apis — ensure that apis used for accessing secrets are secured with authentication and encryption. 🛡️ incident response — have a robust incident response plan in place to quickly address any security breaches involving secrets. Securing apis in a microservices setup involves following essential principles that ensure safe communication and data integrity. here are the key pillars of api security: 1. authentication. Secrets management is a crucial practice in microservices architecture that involves securely storing, accessing, and managing sensitive information such as api keys, passwords, certificates, and tokens.

How To Revoke And Rotate Api Keys And Tokens Securely Securing apis in a microservices setup involves following essential principles that ensure safe communication and data integrity. here are the key pillars of api security: 1. authentication. Secrets management is a crucial practice in microservices architecture that involves securely storing, accessing, and managing sensitive information such as api keys, passwords, certificates, and tokens. Use a centralized secrets management system: avoid storing secrets in code or in environment variables. use encryption: always encrypt sensitive data using a kms. rotate keys regularly: regularly rotate encryption keys to ensure security. monitor and audit access: monitor and audit access to sensitive data. implementation guide. Securing sensitive information is a critical challenge in microservices architectures. as applications are decomposed into numerous independent services, the volume of secrets—passwords, api keys, certificates, and encryption keys—increases dramatically, creating significant security and operational challenges. Rotate secrets regularly: regularly rotate secrets, such as api keys and database credentials, to reduce the risk they are compromised. limit access to secrets: ensure that only authorized services or users can access specific secrets, applying the principle of least privilege. Before implementing specific patterns, establish these foundational principles: 1. use a single source of truth with distributed access. rather than duplicating secrets across services, maintain definitive versions while providing appropriate access to services that need them. 2. assign clear ownership.

How To Secure And Rotate Api Keys And Secrets For Microservices Use a centralized secrets management system: avoid storing secrets in code or in environment variables. use encryption: always encrypt sensitive data using a kms. rotate keys regularly: regularly rotate encryption keys to ensure security. monitor and audit access: monitor and audit access to sensitive data. implementation guide. Securing sensitive information is a critical challenge in microservices architectures. as applications are decomposed into numerous independent services, the volume of secrets—passwords, api keys, certificates, and encryption keys—increases dramatically, creating significant security and operational challenges. Rotate secrets regularly: regularly rotate secrets, such as api keys and database credentials, to reduce the risk they are compromised. limit access to secrets: ensure that only authorized services or users can access specific secrets, applying the principle of least privilege. Before implementing specific patterns, establish these foundational principles: 1. use a single source of truth with distributed access. rather than duplicating secrets across services, maintain definitive versions while providing appropriate access to services that need them. 2. assign clear ownership.

Authentication Implementing Public Api Keys With Microservices Rotate secrets regularly: regularly rotate secrets, such as api keys and database credentials, to reduce the risk they are compromised. limit access to secrets: ensure that only authorized services or users can access specific secrets, applying the principle of least privilege. Before implementing specific patterns, establish these foundational principles: 1. use a single source of truth with distributed access. rather than duplicating secrets across services, maintain definitive versions while providing appropriate access to services that need them. 2. assign clear ownership.
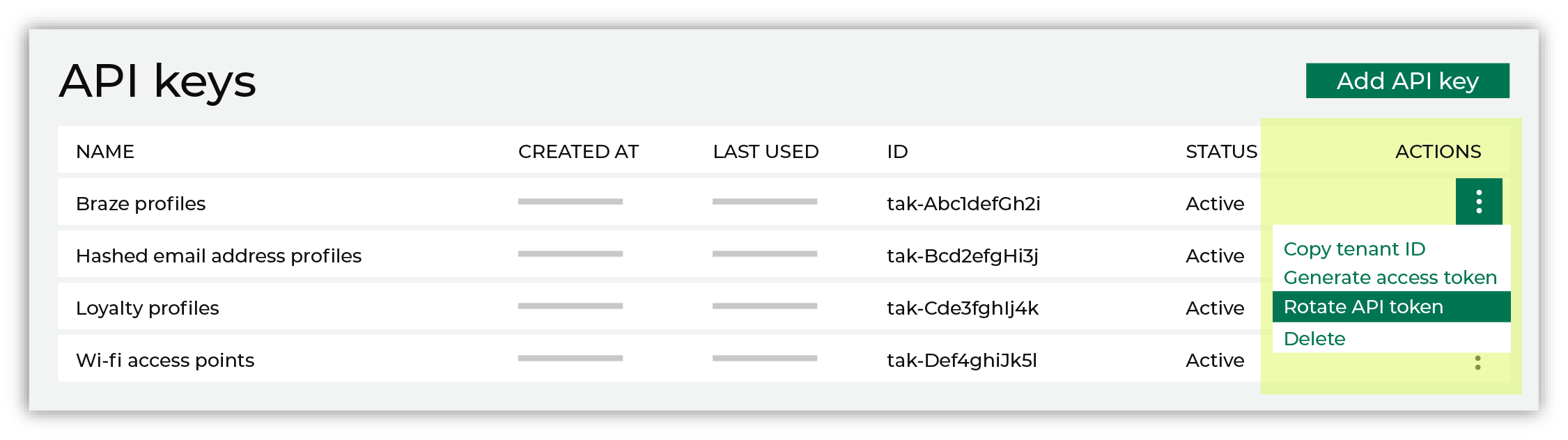
Authentication Amperity Api
Comments are closed.